UPDATE
Home Linksys router users were targeted in a cyberattack that changed router settings, and redirected requests for specific webpages and domains to malicious Coronavirus-themed landing pages that were booby-trapped with malware.
Researchers identified the attack last month, and earlier this week Linksys hit reset on users of its Linksys Smart Wi-Fi application to mitigate against future and past attacks. Linksys representatives told Threatpost that customers are being notified gradually and that all customers should be made aware of the incident and forced password reset “over the next week or so”.
Hackers gained access to at least 1,200 Linksys Smart Wi-Fi accounts via what is believed to be credential-stuffing attacks, according to Linksys, owned by parent company Belkin. The Linksys Smart Wi-Fi app is a password-protected webpage that allows customers to easily manage their Wi-Fi and router settings. Once compromised, attackers manipulated the device’s domain name system routing function so victims would unintentionally visit malicious webpages.
“[The] attack targets home routers and changes their DNS settings to redirect victims to a malware-serving website that delivers the Oski infostealer as a final payload,” wrote Bitdefender researchers in a post March 25.
According to a Linksys security bulletin, on April 2 Smart Wi-Fi users were locked out of their accounts as mitigation efforts to were kicked off by Linksys. “Out of an abundance of caution, we locked all Linksys Smart Wi-Fi accounts to prevent further intrusions. Unfortunately, that means you have to change your password,” Linksys wrote.
Researchers said the attacks began on March 18, peaking March 23. The attacks redirected requests to many domains, including Disney.com, RedditBlog.com, AWS.Amazon.com, Cox.net and Washington.edu.
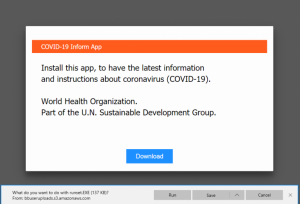 “When trying to reach one of the domains above, users are actually redirected towards an IP address… that displays a message purportedly from the World Health Organization, telling users to download and install an application that offers instructions and information about COVID-19,” researchers wrote.
“When trying to reach one of the domains above, users are actually redirected towards an IP address… that displays a message purportedly from the World Health Organization, telling users to download and install an application that offers instructions and information about COVID-19,” researchers wrote.
The download, or malware payload, was a malicious .exe file from one of four Bitbucket repositories. The .exe file was not the final Oski infostealer payload, but rather a dropper that pulled the malware down from a hacker-controlled command-and-control server.
The Oski malware is new and in the early stages of its development — but packs a sophisticated punch, according to researcher Aditya K. Sood in a January analysis of the data-harvesting tool. Oski is proliferating in North America and China.
Earlier this year, cybercriminals were peddling the malware on illicit online markets as part of malware-as-a-offering, or operators are even selling the completed package, Sood said.
Bitdefender said, of the recent attacks, it can’t say for sure if the compromised Linksys routers were part of a series of brute-force credential attacks.
“It’s still unclear how routers are being compromised but, based on available telemetry, it seems that attackers are bruteforcing some Linksys router models, either by directly accessing the router’s management console exposed online or by bruteforcing the Linksy cloud account,” researchers said.
Linksys has stated that the routers were compromised via brute force attacks.
The Linksys Smart Wi-Fi accounts “enable users to remotely dial into their home network from a browser or mobile device, by using a Linksys cloud account that can be accessed from outside the home network. Since most of the targeted routers seem to involve this particular manufacturer, it’s plausible that this is also an attack vector that attackers exploit,” researchers said.
In its security bulletin it is advising users, “Get a reset password link by going to https://linksys.com/reset. Or you can do it by clicking on Forgot your password? in the Linksys app or Linksys Smart Wi-Fi in a browser.”
(This article was updated 4/19 at 2:15 pm EST with a comment from Linksys representatives.)
Worried about your cloud security in the work-from-home era? On April 23 at 2 p.m. ET, join DivvyCloud and Threatpost for a FREE webinar, A Practical Guide to Securing the Cloud in the Face of Crisis. Get exclusive research insights and critical, advanced takeaways on how to avoid cloud disruption and chaos in the face of COVID-19 – and during all times of crisis. Please register here for this sponsored webinar.











