Earlier this week, when the author behind the crypto-ransomware Locker apologized and released decryption keys for his victims, it seemed like a change of heart, uncharacteristic for an attacker. Now another ransomware creator has also decided to cut his losses and get out of the game – but not before trying to make a buck.
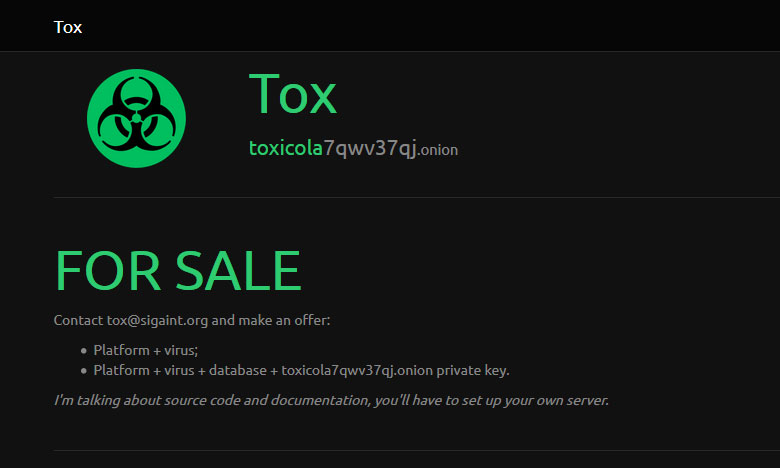
The developer behind Tox, a ransomware-as-a-service tool that only surfaced late last month, acknowledged in a post on Pastebin Wednesday that despite his plan to stay “quiet and hidden,” he’s quickly found himself over his head. Now the malware author is looking to sell Tox but claims if no one buys it he’ll just release the keys and decrypt his victim’s files.
It’s a quick about-face for the developer, who claims he released the malware by spreading links around the “deep web” just two weeks ago. Tox caught on quickly however – quicker than the author expected.
The malware went on to tally 1,000+ users and 1,000+ infections, with more than two hundred polling viruses each half hour, according to the author, who refers to himself as Tox.
“The number of the users started growing. From 20 to 50, from 50 to 100, it was doubling every day,” according to his post, “Plan A was to stay quiet and hidden. Well, I think I screwed up.”
Now, claiming the situation got too hot for him to handle, the author is looking to get out of the business.
Tox is encouraging prospective buyers to contact him to purchase both source code and documentation for the ransomware, adding that he’ll entertain offers for the platform and virus together, or as a package deal, alongside an additional database and .onion private key.
If no one takes the bait, Tox claims he’ll release the keys in a month and any victims of the ransomware will have their files automatically unlocked.
The post is a little disjointed at times–at one point he claims that he’s just a teenager student and that he doesn’t want to be a criminal but later insists that if he had more time and resources, “[Tox] would have become one [of] the greatest viruses ever.”
Lawrence Abram of BleepingComputer.com discovered the post and shared it on his site’s forums Wednesday.
Powered by Tor and Bitcoin, Tox is one of the first ransomware-as-a-service tools to make the rounds. The tool is a free suite that allows criminals to enter their own ransom amount and the platform basically takes it from there.
Tox disguises an executable as a screensaver (.scr) file with the icon of a Word document. Once circulated and opened, the malware encrypts the affected machine and demands a ransom. Tox’s interface keeps track of the entire process, including installs and any profit that comes in. While the author claims Tox has caught on over the last week, it’s unclear exactly how many computers were ultimately infected. With this ransomware the ransom, paid in Bitcoin by the victim, is credited to the attackers’ account and the author of Tox receives 30 percent of the income.
Earlier this week the creator behind the Locker ransomware called it quits, with some experts surmising the attacker had made enough money with the campaign and was opting to shut it down before being caught by law enforcement.
As promised, the ransomware’s author decrypted his victims’ machines and apologized for releasing the malware, claiming it was never his intention to release the malware.