HackerOne said Monday its average dollar payouts to participants are up, and cross site scripting vulnerabilities cause the biggest headaches for companies.
The bug bounty platform provider culled data from the past four years, analyzing 50,000 reported bugs and more than $17 million in payouts to white hat hackers, and published it yesterday in its 2017 Hacker-Powered Security report.
Top-line findings revealed the average bug bounty payout today is $1,923, up 16 percent from 2015’s average of $1,624. The highest bug bounty paid was $30,000 for a critical vulnerability. The payout was one of several $30,000 awards paid by an undisclosed tech firm.
“In the last year, gaming, ecommerce and retail, and media and entertainment programs each awarded a $20,000 bounty to hackers for a critical vulnerability,” according to the report. In the past 12 months, 88 individual bounties were for more than $10,000.
Marten Mickos, CEO of HackerOne, said bug bounty programs follow a natural progression, becoming more lucrative for hackers the older they get. “As a company patches more vulnerabilities, and the attack surface hardens, bounty payouts increase over time,” he said.
Mickos also noted that during the past year, bug bounty programs have experienced more acceptance and growth beyond the tech sector. According to the report, 41 percent of HackerOne bug bounty programs launched in 2016 are for non-tech industries including government, media and entertainment, financial services such as banking and ecommerce.
“When the Department of Defense launched its Hack the Pentagon program that changed a lot of minds about trusting hackers,” Mickos said. “It triggered all sorts of companies to come to us and say, ‘if you are hacking the DoD we want you to hack us as well.'”
Of those bugs reported via the HackerOne platform, 32 percent are high severity or critical. During the past four years the transportation sector has paid the most on average for a critical vulnerability ($4,491) followed by gaming ($3,583) and the ecommerce and retail sector ($3,471). Technology firms came in fifth, paying on average $1,923 for a critical vulnerability and education paid the least ($317).
“The average time to first response for security issues was six days in 2017, compared to seven days in 2016. Ecommerce and retail organizations fixed security issues the fastest on average in four weeks,” according to the report.
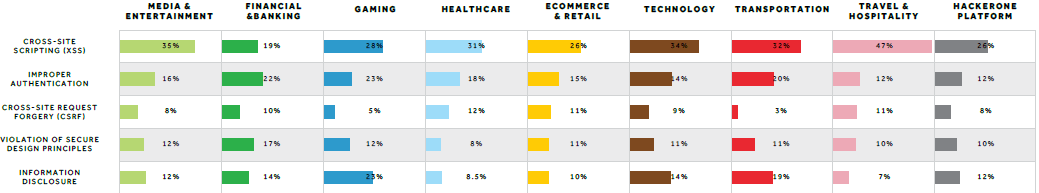
Across all industries, with the exception of financial services and banking, cross-site scripting was the most common vulnerability type discovered by hackers using the HackerOne platform. The report notes that XSS vulnerabilities ranged in severity from reflected to more severe ones similar to one patched by Verizon earlier this year.
Bugs tied to improper authentication were most commonly reported by financial services and banking. SQL injection vulnerabilities also dominated the list of most common vulnerabilities reported to the HackerOne platform. “Healthcare programs have a notably high percentage of SQL injection vulnerabilities (6 percent) compared to other industries during this time period,” according to the report.