College students settling back into school might want to think twice before clicking on an email prompting them to renew their school library account. Researchers warn that students at hundreds of universities worldwide are being targeted with fake emails this week, which tout attachments or links to cloned university login portals or impersonations of university library administration login pages.
These fake landing pages are taking full advantage of the whirlwind back-to-school season, bent on stealing students’ credentials. The threat actors then can use those to steal and resell intellectual property, move laterally within organizations, conduct internal phishing and more, researchers told Threatpost.
“Schools balance a culture of openness and information-sharing with rules and controls to effectively protect user privacy and system security while the severity and sophistication of attacks against schools continue to increase,” Chris Dawson, threat intelligence lead at Proofpoint, told Threatpost. “Cybercriminals capitalize on this atmosphere and target both students and staff to gain access to credentials and vast stores of sensitive data available in student information systems.
Notably, Proofpoint researchers found that the education sector saw the largest year-over-year increase in email fraud attacks of any industry in 2018, soaring 192 percent to 40 attacks per organization on average.
One threat group in particular behind these types of attacks is TA407/Silent Librarian. The attackers have been using low volume, highly targeted, socially engineered campaigns to steal students’ login credentials, targeting hundreds of universities in the U.S., researchers with Proofpoint said on Thursday.
“Campaigns are typically not geographically targeted, but rather tied to specific universities with phishing templates developed for library and student management portals,” they said. “While many of the examples…are from schools in the United States, we regularly observe campaigns affecting hundreds of universities worldwide.”
Phishing Scam
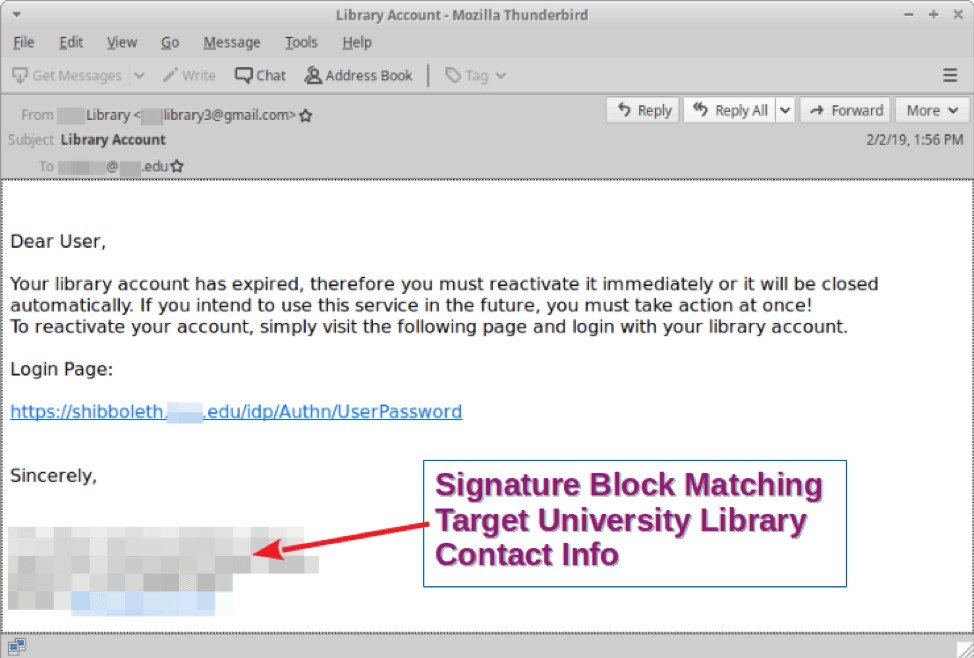
In the case of TA407/Silent Librarian, the threat actors send students emails with links or HTML attachments directing victims to cloned university login portals. The emails will have a theme asking students to renew their library account, saying, “Your library account has expired, therefore you must reactivate it immediately or it will be closed automatically. If you intend to use this service in the future, you must take action at once!” with a link to a fake landing page.
With stolen university branding, accurate street addresses for schools and other social engineering techniques, the portals in the fake landing pages look real enough to trick students into entering their usernames and passwords into the login space.
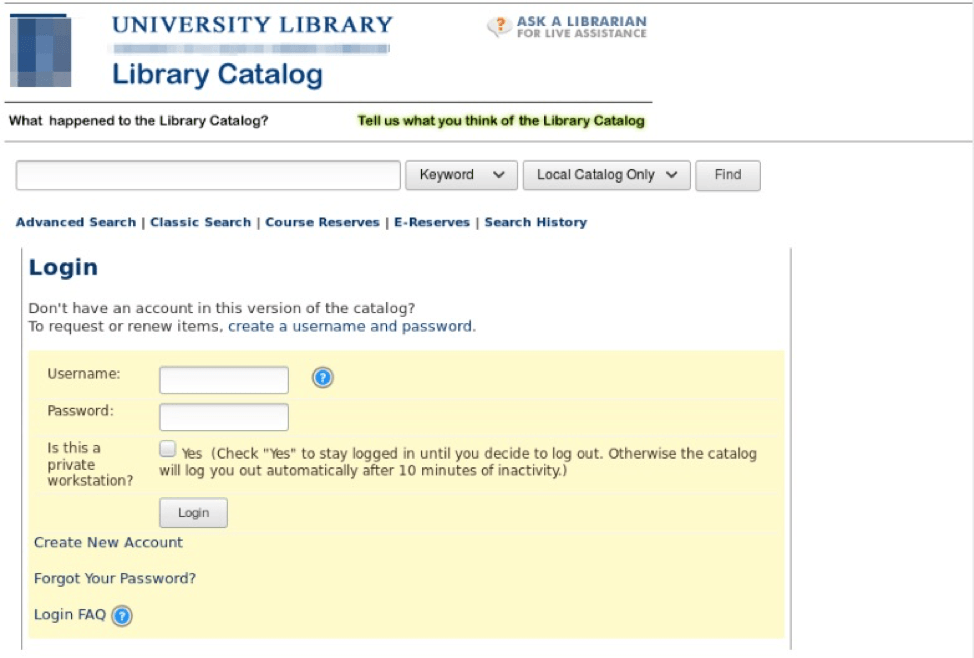
One such example shows a university library catalog login portal, which asks users to input their username and password. The landing page uses a branding image of the university, as well as legitimate-looking sign in tabs with the options to “keep me signed in” and register for password resets.
After entering their login credentials into the fraudulent login page, victims are often redirected to the genuine university login portal, at which point it tells them that the login attempt failed, leaving users unaware that they have been tricked.
“The stolen credentials are then sent to an external site controlled by the attacker, saved in a text file on the same server to be retrieved later, or emailed to inboxes that are controlled by the phisher,” researchers said.
In addition to students, professors and school administrators are also being targeted in phishing scams, “which creates unique challenges,” Dawson told Threatpost.
“Heterogeneous user populations with widely varying levels of computing expertise and frequent changes in the student population create additional hurdles for IT staff in terms of education, training, compliance and security implementation,” he said. “That said, it will most often be students accessing the particular portals used in the phishing templates, putting them potentially at greater risk.”
Malware
In other education-themed campaigns, cybercriminals are dropping malicious content into online student resources, such as essays or online textbooks. These secretly malicious files may attract students who turn to websites posting free access to materials like digital textbooks that are otherwise too expensive to buy.
According to a new Kaspersky report, over the past academic year researchers discovered at least 356,000 malicious files disguised under school and student-related filenames. That includes 223,000 cases of malicious essays being downloaded to computers owned by more than 74,000 people. One-third of those files (122,000) were textbooks, researchers said.
“English textbooks hiding malware were most popular among K-12 students with 2,080 attempted downloads,” according to Kaspersky researchers. “Math textbooks were the next most common, nearly infecting the computers of 1,213 students. Literature closes out the top three most dangerous subjects with 870 potential victims.”
The most commonly-found malware spreading via student resource-related webpages include the “Stalk” worm, which after infecting a system emails itself to all victims’ contacts; other popular malware variants include the Win32.Agent.ifdx malware downloader, WinLNK.Agent.gen downloader and MediaGet torrent application downloader.
Tips For Avoiding Danger
Researchers said that threat actors are most active in targeting the education sector toward the beginning of the school year, the return from winter break (January and February) and conclusion of the school year (April through June). During these months, Proofpoint researchers stressed that students should look out for emails with spelling mistakes, grammatical issues, unsolicited requests for data and suspicious links that might spoof reputable domains.
In particular students should “avoid interacting with suspicious messages, especially ones that request personal information or prompt the student to log in to a university service,” they said.
And, the FBI for its part in a recent alert for students suggested that victims who are targets of online threats call their local law enforcement immediately.
Interested in more on the internet of things (IoT)? Don’t miss our on-demand Threatpost webinar, IoT: Implementing Security in a 5G World. Join experts from Nokia, iboss and Sectigo as they offer enterprises and other organizations insights about how to approach security for the next wave of IoT deployments. Click here to listen to the recorded webinar.