While APT activity and a raft of malware types continue to capture the notice of researchers and journalists, it turns out that trusty old banking trojans remain the top email-borne threat out there.
According to Proofpoint’s latest quarterly report, analyzing trends for the fourth quarter of 2018 based on its telemetry, banking malware that harvests online banking credentials made up 56 percent of all malicious payloads at the end of last year.
Of those, the firm found that Emotet comprised 76 percent of them – although, strictly speaking, Emotet has evolved into much more than just a banking trojan.
“Despite the presence of a range of banking trojans appearing in the wild, threat actors continue to coalesce around known malware,” the report highlighted. “Taken together, Emotet, Panda Banker and Ursnif comprised almost 97 percent of observed banking trojans in Q4. Emotet traffic, while far more consistent and appearing in higher volumes than other bankers in Q4, was quiet for most of October; the actor primarily responsible for high-volume Emotet campaigns was also inactive for most of April. Aside from these two periods, however, Emotet steadily increased in the volume and frequency of associated email campaigns throughout 2018.”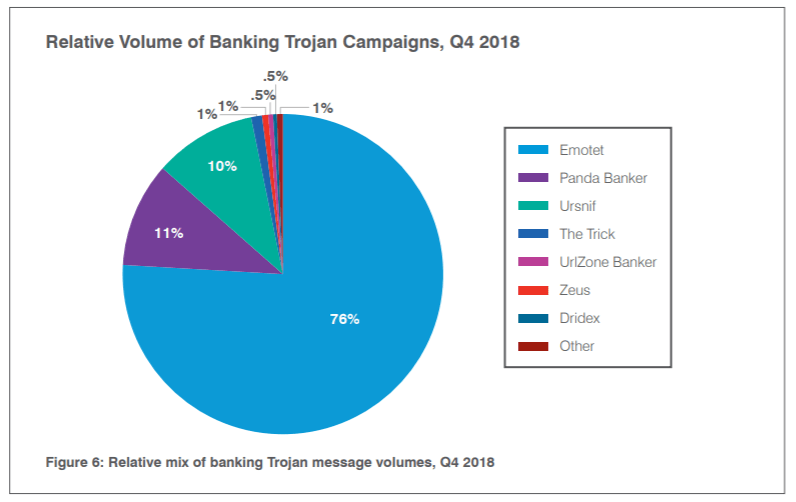
In all, malicious messages bearing credential-stealers or downloaders in general collectively jumped more than 230 percent year-over-year – an illustration of the value of stolen credentials on the Dark Web.
As for the rest of the bunch, espionage-ready remote access trojans (RATs) accounted for just 8.4 percent of all malicious payloads in Q4 and 5.2 percent for the year; however, that marks a significant change from previous years in which they were more rarely used by crimeware actors, according to the report. RATs establish backdoors on a victim’s machine for the purposes of reconnaissance, data exfiltration, credential theft, loading additional malware and so on. APT505 was particularly active using RATs in the quarter.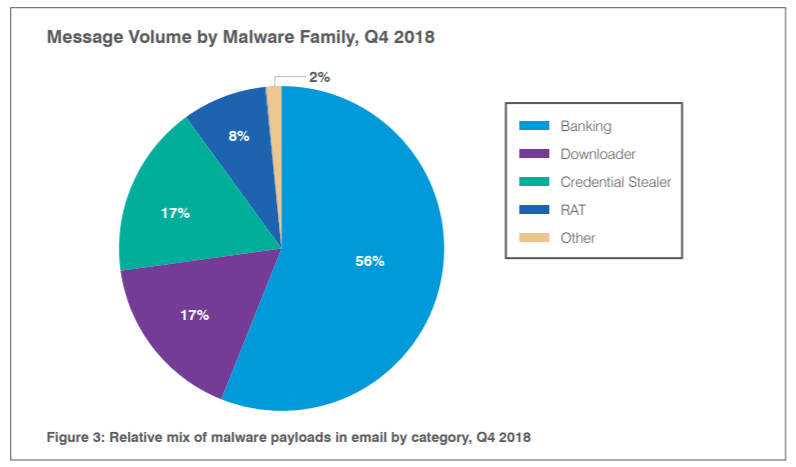
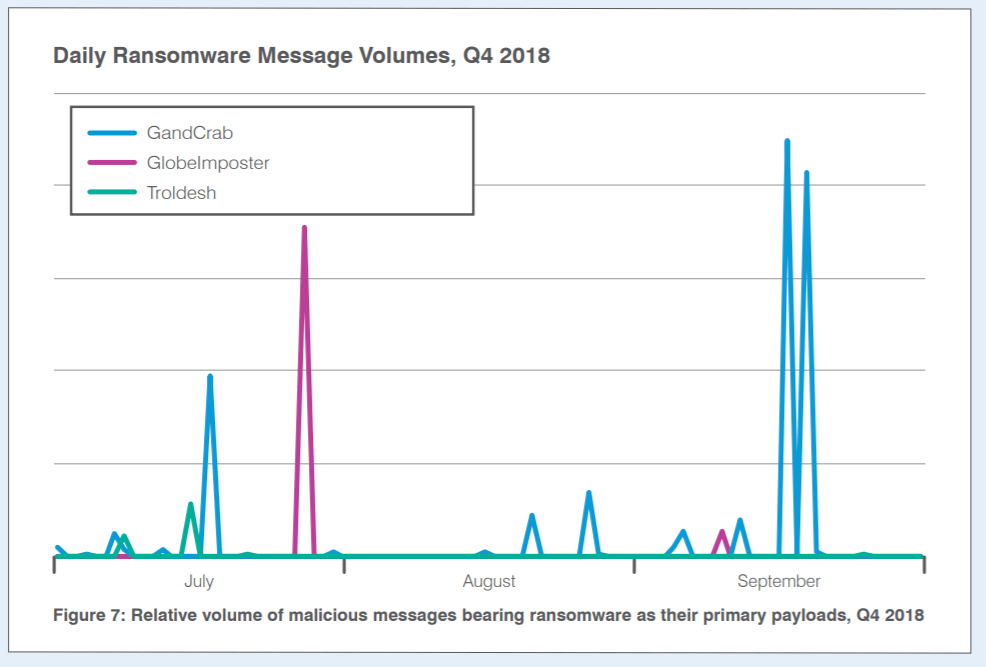
And, ransomware dropped even further in Q4 to just one tenth of 1 percent of overall malicious message volume.
“After dominating the threat landscape in 2016 and much of 2017, ransomware nearly disappeared in Q1 2018,” the report explained. “In Q2, we observed a return of ransomware, albeit at much lower levels than we saw in 2017. However, this spike appeared to be a ‘testing of the waters,’ since ransomware message volumes dropped by 10 percentage points from Q2. This suggests that ransomware campaigns did not generate sufficient returns for threat actors to continue distributing them at scale. Ransomware dropped even further in Q4 to just one tenth of 1% of overall malicious message volume.”
Only three ransomware strains appeared, and only in relatively small, sporadic email campaigns, in Q4: GandCrab, GlobeImposter and Troldesh.
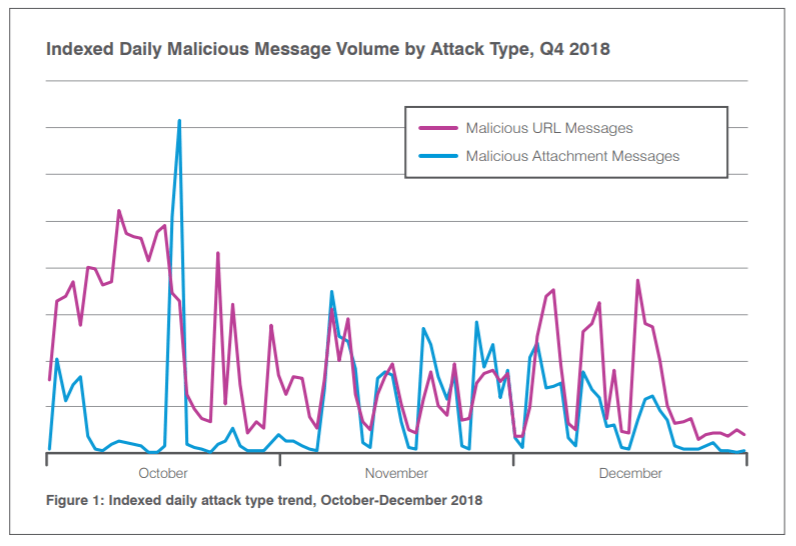
Interestingly, the malware delivery mechanism of choice seemed to be via malicious links embedded within the body of an email, rather than attachments.
“Malicious URLs continued to outnumber malicious attachments in email campaigns delivering malware throughout Q4,” according to the report. “Proofpoint observed over twice as many URL messages as attachment messages during this period, although this constituted a decrease from 2018 as a whole. For the entire year, malicious URLs appeared over three times as often as messages with malicious attachments, suggesting that the pendulum may be swinging back toward attachments as it tends to do periodically.”
On the non-malware email-attack front, business email compromise (BEC) spiked considerably, continuing its inexorable growth; the number of email fraud attacks against targeted companies increased 226 percent quarter-on-quarter and a whopping 476 percent from two years ago. On average, companies targeted by BEC received about 120 fraudulent emails in the fourth quarter of the year, up from 36 in Q3 2018 and up from 21 in the year-ago quarter.