2009 saw many, many new botnet outbreaks and advancements in their criminal management. Throughout the year Damballa tracked thousands of distinct criminal operated botnets and identified millions of newly compromised enterprise systems each day. This week I’m going to share some of our findings from the year now that we’ve finished analyzing terabytes of unique Command and Control (CnC) data.
First on the list: the Top-10 largest botnet outbreaks of 2009.
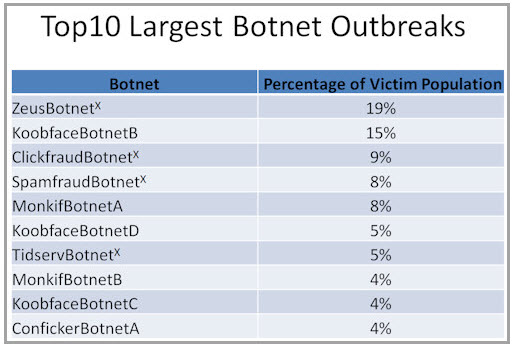
In 2009 the top-4 botnets accounted for half of all botnet infections within enterprise networks. The largest botnet accumulated 19% of all new botnet victims within corporate enterprise networks and was based upon the popular Zeus family of crimeware. At its peak, the criminal entity managing this particular botnet had interactive control of over 600,000 victims at any single point in time – and had managed to breach the security of several millions of additional hosts. It is important to note that Damballa has tracked hundreds of similar botnet operators who also prefer to use the Zeus malware as their bot agent of choice – however, only one such operator made it to the Top-10 largest botnet outbreaks of 2009.
Koobface appears three times in the Top-10 – with Koobface.B accumulating 15% of the new botnet compromises within Enterprise networks in 2009, Koobface.D came in with 5% and Koobface.C accounting for 4%. Koobface managed to successfully leverage social networking platforms and hijack their victim’s accounts to worm their way between systems, and breach millions of unsuspecting hosts.
Coming in an number three, “ClickFraudBotnet” is a single botnet operated by a criminal team that focused on sophisticated click-fraud attacks – and conducted their activities within enterprise networks. The team used many hundreds of different types of malware, from many different malware families. Unlike many other large botnet infections, they did not stick to a single family of malware – e.g. Zeus, Koobface, Conficker, etc. As such, many of the malware they used do not (and continue not to) have any antivirus names, nor are they detected by current antivirus products. Damballa tracked dozens of similarly focused click-fraud botnets in 2009.
The “SpamfraudBotnet” was one of several botnets that focused on sending spam emails from within breached enterprise networks. This class of botnet is operated by seasoned cyber criminals that provide spam services to third-parties as a paid-for offering.
The Monkif family of malware grew to fame in the later stages of 2009. Damballa observed that the Monkif.A variant managed to compromise several hundred thousand enterprise systems – accounting for 8% of all botnet infections during the year. Meanwhile the later variant, Monkif.B, was less successful operating within enterprise networks and only managed to account for 4% of system breaches.
Damballa also observed a handful of different botnet operators using and recycling the Tidserv family of malware. The largest of these Tidserv botnet operators managed to reach 7th position with 5% of system breaches in 2009.
Finally, coming in at 10th place is Conficker.A. While there was much media coverage of Conficker at the beginning of 2009, and the Conficker.C variant garnered most of the limelight, in practical terms Conficker.A was the most successful variant of 2009.
Tomorrow I’ll be covering the Top-10 most successful malware families used by botnet operators in 2009.
Gunter Ollmann is the vice president of research at Damballa. This essay first appeared on the company’s The Day Before Zero blog.










