Google’s official G Suite Twitter account, which has more than 800,000 followers, on Tuesday became the latest victim of an increasingly widespread Bitcoin scam, according to researchers.
The growing size and scope of the scam — as well as the cybercriminals’ success in hijacking high-profile, verified accounts — has some calling for Twitter to intervene.
Scammers had apparently hacked the Google account to tweet out an ad for the scam, which attempts to lure unsuspecting consumers into “participating” in a 10,000 BTC giveaway (almost $62,000 dollars as of press time). All someone has to do is invest a small amount of money in exchange for a chance to win the big pot, the ad claimed.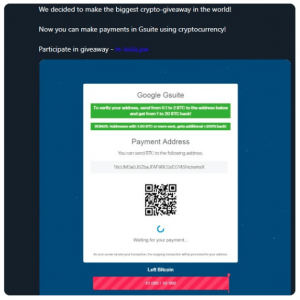
The fraudulent message, which was visible on the account’s home page and in its feeds for about 10 minutes according to reports, also purported to make a legitimate announcement that Google’s G Suite now accepts cryptocurrency as a means of payment.
While the offending message was quickly removed, many picked up on its existence anyway. “First time I’ve seen this scam – it’s a promoted tweet, but If you click the user ID in the tweet, it actually takes you to the legit G Suite Twitter account. Very clever. @Google @gsuite,” tweeted Andrew Maxey, a Cisco security researcher.
The hack is a bit ironic given that Google in June said that it would move to restrict advertisements from cryptocurrency firms.
It’s also just the latest in a string of such hacks; the G Suite hack followed hard on the heels of a nearly identical incident on Target’s Twitter account, which has about 2 million followers. There, the fake tweet advertised a $5,000 BTC giveaway (around $31 million).
“Early this morning, Target’s Twitter account was inappropriately accessed,” the retail giant said in a media statement on Wednesday. “The access lasted for approximately half an hour and one fake tweet was posted during that time about a Bitcoin scam.”
Also this week, the scammers (it’s unclear if these are all carried out by the same actors) hit the official accounts of the Indian Consulate in Frankfurt, IT consultancy Capgemini, the Consulate General of India in Germany, California state senator Ben Allen and Israeli politician Rachel Azaria, with similar hacks and fake tweets, according to reports.
And, earlier in November, a whole bevy of verified accounts were hacked to tweet out the same ad. In that incident, the fraudsters changed the profile name and picture to impersonate Tesla CEO Elon Musk – going so far as to participate in comment threads on Musk’s actual account in order to gain an air of legitimacy.
One of the earliest examples of the scam is from July, when fraudsters gained control of the official Twitter account of the long-canceled FOX show Almost Human (which wrapped its day in the sun back in 2014). They used the access to spread the same kind of giveaway links, while changing the profile of the account to that of Justin Sun, founder and CEO of Chinese blockchain startup TRON.
The approach is not that novel – Sophos Security pointed out that “the technique is a variant of the 419 scams that have plagued email users for so long, in which scammers claim to be high-ranking officials needing to get money overseas. They ask victims to send them a small amount of money in exchange for millions, which predictably never arrive.”
This type of scam has also been seen targeting Vitalik Buterin, co-founder of Ethereum, who changed his Twitter username to Vitalik ‘Not giving away ETH’ Buterin in the aftermath; he also asked Twitter to intervene.
Speaking of Twitter intervening, independent researcher Graham Cluley placed the blame squarely at the social media company’s feet in a tweet, noting “This is @Twitter’s problem. They clearly haven’t got a handle on these cryptocurrency scams.”
He added in a blog post that Twitter should make two-step verification via a third-party app like Google Authenticator mandatory for verified accounts.
“And if a user turns off Login Verification, they should also lose their verified ‘tick,'” he said.
For its part, Twitter didn’t immediately respond to a request for comment from Threatpost, but we’ll update the story with any statements.










