Researchers are warning that a new class of botnets could be marshaled and used to manipulate energy markets via zombie armies of power-hungry connected devices such as air conditioners, heaters, dryers and digital thermostats. A coordinated attack could cause an energy stock index to predictably go up or down – creating an opportunity for a rogue operator to cash in.
 Researchers with the Georgia Institute of Technology laid out the scenario in a Black Hat 2020 virtual session Wednesday. They warned, high-wattage IoT devices are vulnerable to takeover by threat actors who can hijack them in the same way that millions of CCTV cameras, DVRs and home routers are recruited into botnet armies to conduct distributed denial-of-service attacks and mine cryptocurrency.
Researchers with the Georgia Institute of Technology laid out the scenario in a Black Hat 2020 virtual session Wednesday. They warned, high-wattage IoT devices are vulnerable to takeover by threat actors who can hijack them in the same way that millions of CCTV cameras, DVRs and home routers are recruited into botnet armies to conduct distributed denial-of-service attacks and mine cryptocurrency.
“If an attacker can just slightly affect electricity market prices in their favor, it would be like knowing today what’s going to happen in tomorrow’s stock market,” said Tohid Shekari, a graduate research assistant in the School of Electrical and Computer Engineering at the Georgia Institute of Technology.
Shekari was joined by Raheem Beyah, professor, vice president for Interdisciplinary Research, at Georgia Institute of Technology, during the session. They explained that energy markets are split into either a day-ahead or real-time. Energy producers work with resellers who deliver electricity to end users. The ecosystem is ripe for manipulation by threat actors, they said.
“To meet the demand for electrical energy, utility companies must predict future demand and purchase power from the day-ahead wholesale energy market at competitive prices,” according to a Georgia Tech report on the research. “If the predictions turn out to be wrong, the utilities may have to pay more or less for the energy they need to meet the demands of their customers by participating in the real-time market.”
Those real-time markets are more volatile and subject to price fluctuation. “Creating erroneous demand data to manipulate forecasts could be profitable to the suppliers selling energy to meet the unexpected demand, or the retailers or utilities buying cheaper energy from the real-time market,” the report said.
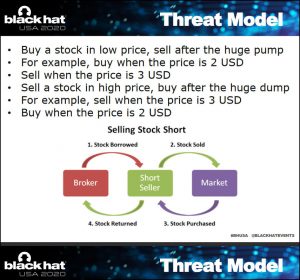
Manipulation of this energy ecosystem can also allow a rogue investor to accurately predict a shift in market value and capitalize on ups and downs.
During the Black Hat session, Beyah estimated that the number of hijacked IoT devices needed to carry out an attack might be 50,000 within a single market. That would enable what he called an “IoT Skimmer” attack. Using a botnet to increase or decrease power consumption by just 1 percent would be enough to manipulate prices and be extremely hard to detect.
Bigger swings in power consumption, researchers pointed out, could also be used to sabotage an energy supplier.
“By turning the compromised equipment on or off to artificially increase or decrease power demand, botnets made up of these energy-consuming devices might help an unscrupulous energy supplier or retailer (electric utility) alter prices to create a business advantage, or give a nation-state a way to remotely harm the economy of another country by causing financial damage to its electricity market,” according to the Georgia Tech report.
IoT Skimmer Attacks: Hypothetical
While the damage wrought by botnets and botnet malware like Mirai, Hydra and BASHLITE is not hypothetical, the IoT Skimmer attacks are. Researchers said they are unaware of any specific attacks designed to manipulate energy markets.
Separately, the energy sector is often targeted by way of disruptive attacks. In January, researchers identified the threat actor group APT33, dubbed Magnallium, targeting global oil-and-gas industry and electric companies in North America. Months before that campaign was uncovered, another advanced persistent threat group (APT34), also known as ZeroCleare, was bent on destruction and disruption of the Middle East oil industry.
Destructive intent aside, researchers estimate a three-month IoT Skimmer campaign could yield attackers $24 million a year. A malicious IoT Skimmer attack, on the other hand, could cause $350 million per year in economic damage to the U.S. energy sector, the researchers estimated.
The Georgia Tech research was based on one year of real-world data analysis of the two largest electricity markets in the U.S. – New York and California, Shekari and Beyah said.
Mitigating against these types of attacks, the researchers said, will take comprehensive monitoring of high-wattage IoT-connected devices and any unexpected spikes or dips in power consumption would need to trigger alarm bells.
Please follow all of Threatpost’s Black Hat 2020 coverage by clicking here.
Complimentary Threatpost Webinar: Want to learn more about Confidential Computing and how it can supercharge your cloud security? This webinar “Cloud Security Audit: A Confidential Computing Roundtable” brings top cloud-security experts from Microsoft and Fortanix together to explore how Confidential Computing is a game changer for securing dynamic cloud data and preventing IP exposure. Join us Wednesday Aug. 12 at 2pm ET for this FREE live webinar with Dr. David Thaler, software architect, Microsoft and Dr Richard Searle, security architect, Fortanix – both with the Confidential Computing Consortium. Register Now.










