Criminals are breathing new life into Cerber ransomware with a stubborn spam campaign called Blank Slate that is successfully abusing hosting providers to spread the malware.
Researchers at the SANS Internet Storm Center said the campaign has shifted from spreading Sage 2.0 and Locky ransomware, to in recent weeks attempting to infect Windows PCs with Cerber ransomware.
Identified last July, Blank Slate has effectively survived several shutdown attempts by hosting providers with a slick process for registering new servers that host the ransomware executable, said Brad Duncan, handler at the SANS Internet Storm Center and threat intelligence analyst at Unit 42 of Palo Alto Networks, in blog post.
The Blank Slate campaign gets its name from the fact its spam messages contain no text in the subject or body of the message. Emails contain only a double-zip archive with the second zip archive containing either a malicious JavaScript file or a malicious Microsoft Word document. The blank message and double-zip archive may seem crude, but Duncan believes crooks are under the belief it is an effective way to evade detection technologies.
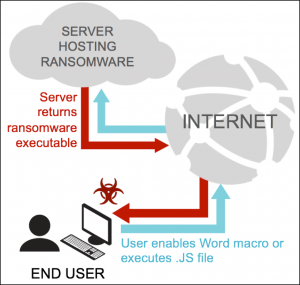 The infection chain is conventional starting with the double-zip archive. If the JavaScript is double-clicked, or the Word macro is enabled, Cerber is downloaded from a server and ultimately infects the host. Notable, researchers said, is that criminals behind Cerber have recently upped their ransomware demand from $500 to 1 bitcoin ($1,000).
The infection chain is conventional starting with the double-zip archive. If the JavaScript is double-clicked, or the Word macro is enabled, Cerber is downloaded from a server and ultimately infects the host. Notable, researchers said, is that criminals behind Cerber have recently upped their ransomware demand from $500 to 1 bitcoin ($1,000).
For its part, Cerber has been a potent strain of ransomware morphing over the past year to remain a consistent threat. Last week, researchers at Deep Instinct said the latest sample of Cerber it examined was finding great success bypassing security detection systems with a new technique where malicious code was buried inside NSIS installers.
What is most interesting about the Blank Slate campaign is how it eludes shutdown attempts by hosting providers, according to the SANS report.
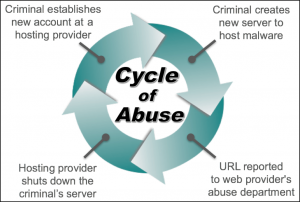
In February, Unit 42 determined Blank Slate was utilizing 500 domains. “These malicious domains were quickly taken offline, but Blank Slate actors quickly registered new ones, revealing a cycle of abuse towards legitimate hosting providers,” Duncan said.
“The requirements for establishing an account at a hosting provider are easy to obtain. The criminals only require a valid email, phone number, and credit card. Criminals can establish new servers; those servers are reported; the hosting provider shuts them down; and the criminals establish new servers,” Duncan said in an interview with Threatpost.
 Costs to perpetuate the cycle of abuse are negligible for crooks. “A new email account can be established for free. Burner phones are cheap, as low as $20,” Duncan wrote. Stolen credit card credentials can be purchased on the black market for $5.
Costs to perpetuate the cycle of abuse are negligible for crooks. “A new email account can be established for free. Burner phones are cheap, as low as $20,” Duncan wrote. Stolen credit card credentials can be purchased on the black market for $5.
Unit 42 believes the campaign of blank messages is coming from numerous hosts around the globe from what it believes are botnets. An examination of the JavaScript file revealed an HTTP GET request for the ransomware binary.
“Post-infection traffic was similar to several other recent examples of Cerber. You’ll see UDP traffic from the infected host over port 6892. That’s followed by HTTP traffic to a domain starting with p27dokhpz2n7nvgr and ending with .top. IP addresses for the UDP traffic changes every week or two (or longer). Post-infection HTTP domains change more frequently,” Duncan wrote.
He said decryption instructions were dropped to the desktop in three different files. File names began with “_READ_THIS_FILE_” and consisted of a text file, an image file and an HTML Application (HTA) file.
“Domains and IP addresses associated with the Blank Slate campaign are constantly changing,” Duncan wrote. “With the current popularity of ransomware, we continue to see malspam daily in both targeted attacks and wide-scale distribution.”










