A credential-phishing attempt that relies on impersonating Bank of America has emerged in the U.S. this month, with emails that get around secure gateway protections and heavy-hitting protections like DMARC.
The campaign involves emails that ask recipients to update their email addresses, warning users that their accounts could be recycled if this isn’t done.
“The email language and topic was intended to induce urgency in the reader owing to its financial nature,” according to analysis from Armorblox. “Asking readers to update the email account for their bank lest it get recycled is a powerful motivator for anyone to click on the URL and follow through.”
The messages contain a link that purports to take visitors to a site to update their information – but clicking the link simply takes the recipients to a credential-phishing page that closely mirrors a legitimate Bank of America home page, researchers said.
The attack flow also included a page that asked readers for their ‘security challenge questions’, both to increase legitimacy as well as get further identifying information from targets, researchers said in a posting on Thursday.
“With the enforcement of Single Sign On (SSO) and two-factor authentication (2FA) across organizations, adversaries are now crafting email attacks that are able to bypass these measures,” Chetan Anand, co-founder and architect of Armorblox, told Theatpost. “This credential-phishing attack is a good example. Firstly, it phishes for Bank of America credentials, which are likely not to be included under company SSO policies. Secondly, it also phishes for answers to security-challenge questions, which is often used as a second/additional form of authentication. Asking security-challenge questions not only increases the legitimacy of the attack, but also provides the adversaries with vital personal information about their targets.”
More interesting, the emails are able in some cases to get past existing email security controls – because they don’t follow the patterns of more traditional phishing attacks.
For instance, the campaign, while using a classic “spray-and-pray” lure, is not a mass email effort, according to the firm. In examining one of the emails, researchers noticed that “this was not a bulk email and only a few people in the target organization received it,” they wrote. “This ensured that the email wasn’t caught in the bulk email filters provided by native Microsoft email security or the Secure Email Gateway (SEG).”
Anand told Threatpost, “We’re working on identifying scope of impact outside of our customer base but campaigns like this in the past have been fairly broad in their attack scope since the content is generic enough to cut across organizations and industry verticals. Within our customer base, it was not a mass email but not a single email either. A few key VIPs or VAPs (Very Attacked Persons) got the email.”
Also, the email they examined was able to get past common authentication checks, such as DMARC. DMARC (which stands for Domain-based Message Authentication, Reporting and Conformance) is an industry standard that flags messages where the “from” field in an email header has been tampered with. It ensures emails are authenticated before they reach users’ mailboxes and confirms that they have been sent from legitimate sources. If configured correctly, potential phishing emails can be stopped at the gateway, or redirected to the junk folder.
“Although the sender name – Bank of America – was impersonated, the email was sent from a personal Yahoo account via SendGrid. This resulted in the email successfully passing all authentication checks such as SPF [Sender-Policy Framework], DKIM [DomainKeys Identified Mail] and DMARC,” explained the researchers.
DMARC is useful but has a few key gaps, Anand told Threatpost.
“Firstly, DMARC is mainly designed to protect against direct domain spoofs (which this was not),” he said. “Secondly, to protect an organization using DMARC, all domains used in communication with employees should have DMARC enabled on them (which doesn’t happen today). Emails sent from legitimate domains (Gmail, Yahoo) while not being a direct domain spoof have a good chance of passing DMARC.”
The attackers also used a brand-new, never-before-used URL to set up their phishing website. Because the page is hosted on a new domain, it was able to get past any filters that were created to block known bad links.
Also, the effort exhibits much better social engineering than what is usually seen in attacks like these, according to the firm. For instance, the final credential phishing page was “painstakingly made to resemble the Bank of America login page,” explained the researchers.
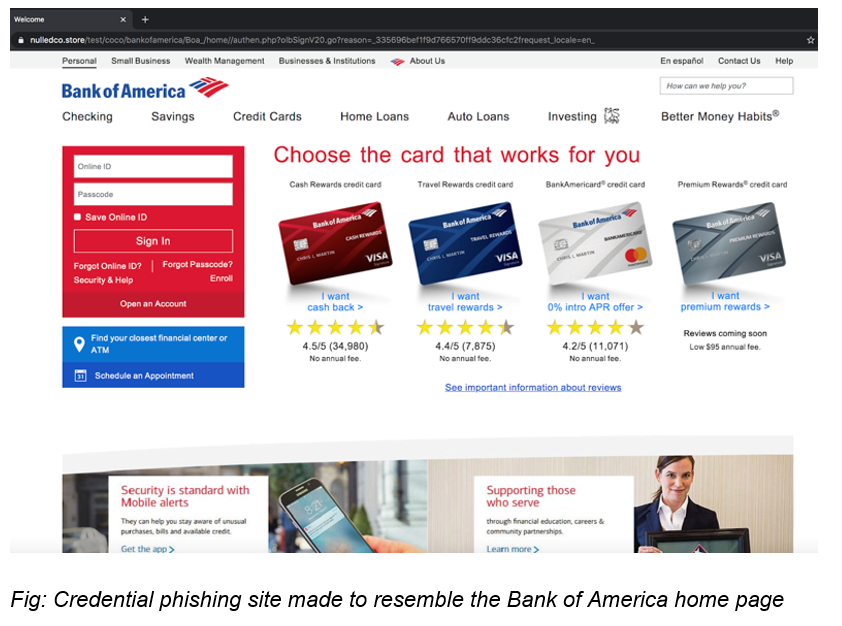
“The level of polish involved in this attack is noteworthy,” Anand said. “The phishing sites are unerringly made to resemble Bank of America pages at first glance. The other sign of sophistication in this attack is the fact that attackers asked targets for their security challenge questions as well. If attackers successfully harvest any such answers, they can potentially brute-force their way into other accounts where security challenge questions are involved (since these questions tend to be common across apps).”
Insider threats are different in the work-from home era. On June 24 at 2 p.m. ET, join the Threatpost edit team and our special guest, Gurucul CEO Saryu Nayyer, for a FREE webinar, “The Enemy Within: How Insider Threats Are Changing.” Get helpful, real-world information on how insider threats are changing with WFH, what the new attack vectors are and what companies can do about it. Please register here for this Threatpost webinar.











