British virtual private network (VPN) company Hide My Ass has taken a stand about their involvement in the arrest of an alleged Lulzsec member last week. In a blog post published on Friday, the company reiterated that they keep logs of their users’ history for 30 days and they will cooperate with law enforcement agencies if it’s become evident certain accounts have been used for illegal activites.
The post was prompted by news on Thursday that agents from Los Angeles’ Federal Bureau of Investigation (FBI) arrested suspected Lulzsec member Cody Kretsinger in Phoenix, Ariz. In an indictment filed September 2 at the U.S. District Court of California, Kretsinger, going by the online handle “recursion,” reportedly used the proxy services of Hidemyass.com as a medium for his attacks.
In the post, titled “Lulzsec fiasco,” Hide My Ass calls back to its terms of service, emphasizing the fact that the site was originally formed “as a way to bypass censorship of the world-wide-web.” The company goes on to clarify that its services were never designed to be used to break the law and defends its practice of logging its customer’s whereabouts.
“Ask yourself this: if a provider claims not to do any form of logging, but is able to locate abusive customers, how are they able to do this without any form of logging?” the post questions.
While the company admits it has known the service was being used by members of Anonymous and Lulzsec since June, it wasn’t until they received a court order requesting information about some of the groups’ high profile attacks that they cooperated. Authorities sought information on Playstation Network hack, the NATO hack, as well as attacks on the Web pages of The Sun and The Times.
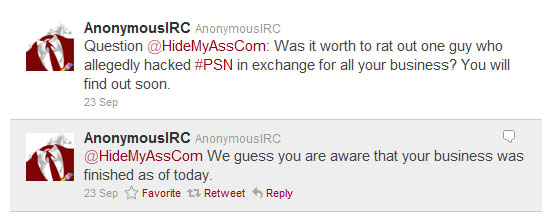
As expected, the blog post received its fair share of scrutiny from the hacktivist crowd. Anonymous’ Twitter account, AnonymousIRC, sent a handful of pointed tweets to the VPN service over the weekend.
Despite efforts by the group’s leadership to remain “anonymous,” authorities in the U.S., UK Turkey and Spain have scored some apparent successes in recent weeks rounding up both foot soldiers who took part in denial of service attacks, and senior members of both Anonymous and the splinter group LulzSec. Authorities often using records from ISPs or fellow members to lead police to their man.








