 While the security teams at Microsoft, Mozilla and the other browser vendors continue to work on new defenses and exploit mitigations, the state of the art in attacks is continuing to evolve.
While the security teams at Microsoft, Mozilla and the other browser vendors continue to work on new defenses and exploit mitigations, the state of the art in attacks is continuing to evolve.
Security researcher Robert Hansen recently pointed out a new technique that could be used for a twist on the URL hijacking attack. The tactic uses JavaScript to fool users into thinking they’re downloading content from a trusted site when, in fact, they’re connected to a malicious site that’s pushing an exploit to their machines.
In a demo he put together, Hansen shows that an attacker could use the JavaScript to force a pop-up window to launch on a legitimate site while a user is trying to download some software, such as a browser add-on. If the user has the pop-up blocking mechanism enabled in Firefox, he’d see the drop-down notification indicating that the browser had blocked the pop-up from the malicious domain from installing software. But if the attacker selects a domain name that’s somewhat similar to the legitimate site’s, the user would have little indication that anything was wrong and would likely go ahead with the download.
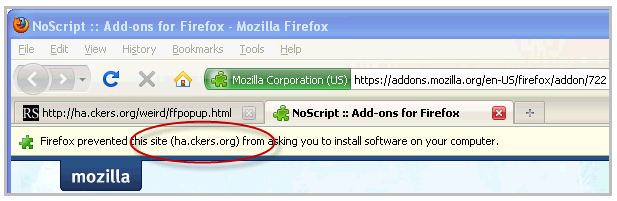
All the while, the user still sees the legitimate site’s URL in the address bar on the browser, as pictured above.
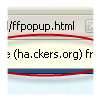
You will notice that it quite clearly says that it is being downloaded
from ha.ckers.org, but the vast majority of users won’t understand what
that means, since, of course, they are quite clearly on the EV cert
protected addons.mozilla.org. Also, presumably an attacker would
normally pick something like addons.mozilla.org.xyx.com instead of
ha.ckers.org. Worse yet, it blocks the user from downloading the
legitimate file until they take action on what my malicious website is
prompting them to do.
Trying to explain the details of that kind of attack to the average user would be a fool’s errand, and even security-conscious Web users might have a difficult time recognizing the attack when it happens.






