Scared is a strong word, but the reality, according to a Websense analysis by Patrik Runald, is that spear-phishers, like the ones that compromised a White House network last week, are implementing new evasion tactics, fundamentally changing their attack strategies, and revolutionizing the targeted threat model, giving business executives plenty of reason to worry.
One of the newer attack strategies is the relatively recent ‘watering hole‘ technique, but the changes also include an increased focus on victim behavior, and the adoption of successful tactics used by other factions of the cybercriminal world, specifically scareware and ransomware.
Runald describes spear-phishing as ‘the CSO nightmare,’ because it is the most difficult type of attack to defend against. In an email interview, Runald said spear-phishing is nearly indefensible because the attacks make use of a number of detection-evading measures, including clever and targeted social engineering, zero-day exploits, and malware with low antivirus detection rates. In addition to this, he explained, such attacks are inherently discreet and can be sustained as long as needed, even if it takes years.
Social engineers have adopted and are implementing into their phishing campaigns the wildly successful tactics of their cousins in the business of peddling rogue antivirus products. Runald reports that the appearance of fake security alerts in corporate phishing campaigns is increasingly commonplace. In fact, the top four phishing email subject lines are, according to Websense, ‘Your account has been accessed by a third party,’ ‘[Bank Name] Internet Banking Customer Service Message,’ ‘Security Measures,’ ‘Verify your activity,’ and ‘Account security notification.’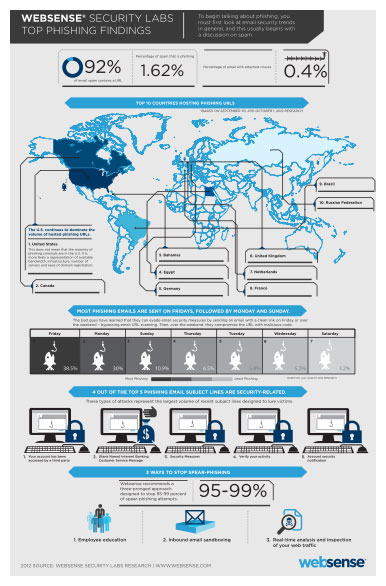
Websense’s data goes on to illustrate a substantial surge in phishing emails going out on Fridays, when phishers send 38.5 percent of emails, Mondays, where they push a clean 30 percent of such emails, and Sundays, accounting for just fewer than 11 percent of phishing emails. These statistics reflect a shift in the understanding of or perhaps a more sustained focus on the behavior targeted victims by the attackers.
Criminals will often send out phishing emails with clean links on a Friday or over the weekend, only to go back in on Monday and compromise the vulnerable website with malware. Basically, the attackers are identifying vulnerable websites, but leaving them alone at first. They then craft emails with links to the vulnerable website, taking necessary precautions to ensure that the emails won’t trigger any of the target-organizations’ spam or other email-security filters.
The key is guaranteeing that the target employee won’t open the email immediately. This way, it can clear the organization’s email defenses while the link remains clean but won’t be opened until the attacker goes back in and compromises the vulnerable website. In the best case scenarios, the attacker compromises the URL just before his or her target accesses the phishing email. Runald claims these evasion techniques are particularly useful in spear-phishing employees with access to specific network data and in what he calls whale-phishing, or targeting executives.
Water-holing is a social engineering method where attackers essentially set traps for their victims on sites that they believe a particular person, or in many cases, a potential person in a particular industry or organization, is likely to visit. Runald says that a recent compromise of Amnesty International and another in May of the Institute of National Security Studies’ website in Israel are good examples of what water hole attacks look like. There is no way to determine if the latter was actually a targeted, water-holing attack, but the INSS studies issues of Israeli and Middle Eastern security affairs and among INSS’s readership there are likely a number of individuals in important national defense-related positions in Israel, the U.S., and across the Middle East. So, Runald argues, it would be a likely target for cybercriminals seeking access to certain sensitive data. Runald explains that water-holing allows attackers (that may not yet know a victim’s contact info) to drop a slightly wider net ahead of a more precise spear-phishing attack.
“These attacks illustrate how spam has evolved to phishing,” Runald writes, “which has evolved to spear-phishing, which in turn has evolved into sophisticated, targeted web compromises (watering holes), something unheard of just a short time ago.”
Generally speaking, 92 percent of spam email contains a link and just less than two percent of spam emails are categorized as phishing attempts, outnumbering emails with malicious executables, which account for 0.4 percent of all spam.
Historically, phishing emails contain a link leading victims to a fake login page designed to pilfer login credentials. Most of these phishing websites are hosted in the U.S., though not necessarily hosted by American criminals. Websense claims that this likely reflects the availability of bandwidth, quality of infrastructure, number of servers, and the ease of domain registration in the U.S.
Websense believes there are three key components to addressing the spear-phishing problem: employee education, inbound email sandboxing, and real-time analysis and inspection of web traffic.









