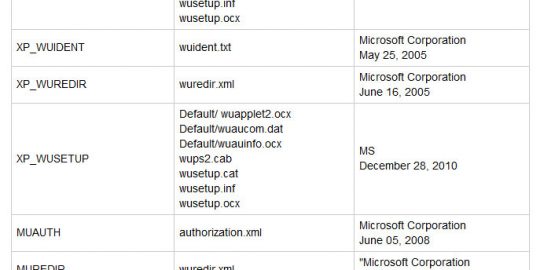
How The Flame Malware Stayed Hidden For So Long
The past week has brought to light more revelations about the mysterious Flame (or sKyWIper) worm that was first identified at the end of May. Among them: the eye-popping admission from Microsoft that the malware’s authors found a way to use that company’s Windows Update feature to distribute the malware.