An under-construction malware called Chaos has been spotted, which is being advertised on an underground forum as being available for testing. While it calls itself ransomware, an analysis revealed that it’s actually more of a wiper.
According to Trend Micro researcher Monte de Jesus, Chaos has been around since June, and has already cycled through four different versions, with the last one being released on August 5. This rapid development could mean that it will soon be ready for primetime, but so far it hasn’t been used in actual attacks, he said.
Chaos started out purporting to be a .NET version of the Ryuk ransomware – a ruse it went all in on, complete with Ryuk branding on its GUI. However, de Jesus said that looking under the hood of its first version reveals very little of this supposed heritage. Instead, the sample is “more akin to a destructive trojan than to traditional ransomware,” he noted, in a Tuesday analysis.
He added, “Instead of encrypting files (which could then be decrypted after the target paid the ransom), it replaced the files’ contents with random bytes, after which the files were encoded in Base64. This meant that affected files could no longer be restored, providing victims no incentive to pay the ransom.”
This version of Chaos also had other notable tricks up its sleeve.
“One of the more interesting functions of Chaos version 1.0 was its worming function, which allowed it to spread to all drives found on an affected system,” de Jesus wrote. “This could permit the malware to jump onto removable drives and escape from air-gapped systems.”
Once installed, this first version of Chaos searched for various file paths and extensions to infect, and then dropped a ransomware note named read_it.txt, asking for .147 Bitcoin, which is around $6,600 at today’s exchange rate.
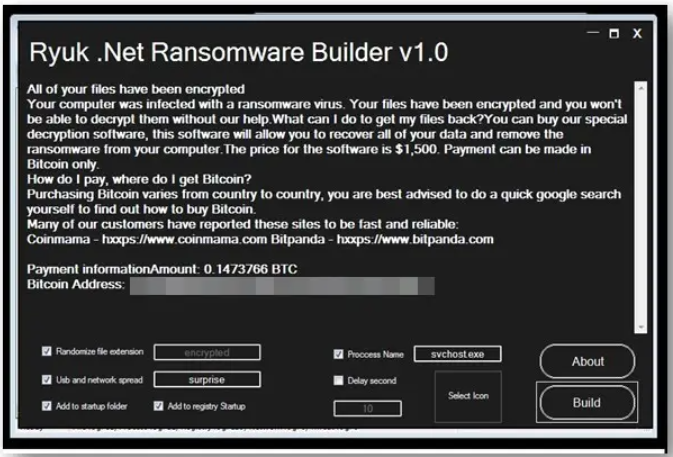
The second version meanwhile added advanced options for administrator privileges, the ability to delete all volume shadow copies and the backup catalog, and the ability to disable Windows recovery mode.
“However, version 2.0 still overwrote the files of its targets,” de Jesus said. “Members of the forum where it was posted pointed out that victims wouldn’t pay the ransom if their files couldn’t be restored.”
Chaos became more ransomware-ish with version 3.0, when it added encryption to the mix. This sample had the ability to encrypt files under 1 MB using AES/RSA encryption, and featured a decryptor-builder, according to the researcher.
Then, in early August, the fourth iteration of Chaos appeared on the forum, with an expansion of the AES/RSA encryption feature. Now, files up to 2MB in size can be encrypted. And, operators can append encrypted files with their own proprietary extensions, like other ransomwares, according to the analysis. It also offers the ability to change the desktop wallpaper of their victims.
Ransomware has been on the rise so far in 2021, with global attack volume increasing by 151 percent for the first six months of the year as compared with the year-ago half, according to a recent report. Meanwhile, the FBI has warned that there are now 100 different strains circulating around the world. The most-deployed ransomware in the wild is Ryuk, the report found, which could account for why the Chaos authors attempted to ride its coattails.
For now, the Chaos “ransomware” is still clearly under construction, de Jesus noted, so new versions are likely on the horizon. For instance, it lacks the data-exfiltration capabilities that almost all major ransomware families have now to allow for double-extortion attempts – an oversight that will likely be remedied.
Essentially, Chaos is for now a proof-of-concept malware, according to the researcher – but one that “could be dangerous in the wrong hands” thanks to its ability to wipe out files.
He noted, “in the hands of a malicious actor who has access to malware distribution and deployment infrastructure, it could cause great damage to organizations.”
Worried about where the next attack is coming from? We’ve got your back. REGISTER NOW for our upcoming live webinar, How to Think Like a Threat Actor, in partnership with Uptycs. Find out precisely where attackers are targeting you and how to get there first. Join host Becky Bracken and Uptycs researchers Amit Malik and Ashwin Vamshi on Aug. 17 at 11AM EST for this LIVE discussion.











