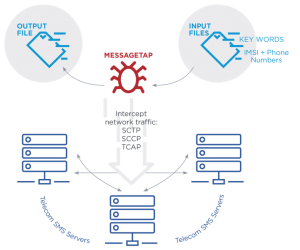
Researchers have discovered a new malware used for cyber-espionage efforts by China-linked threat group APT41. The malware intercepts telecom SMS server traffic and sniffs out certain phone numbers and SMS messages – particularly those with keywords relating to Chinese political dissidents.
The espionage tool, dubbed MessageTap, was discovered by FireEye Mandiant during a 2019 investigation of a cluster of Linux servers within an unspecified telecom network; these operated as Short Message Service Center (SMSC) servers. In mobile networks, SMSCs are responsible for sending SMS messages to an intended recipient or storing them until the recipient has come online.
“The tool was deployed by APT41 in a telecommunications network provider in support of Chinese espionage efforts,” said FireEye researchers Raymond Leong, Dan Perez and Tyler Dean, in a report on Thursday. “APT41’s operations have included state-sponsored cyber-espionage missions as well as financially motivated intrusions. These operations have spanned from as early as 2012 to the present day.”
In this case, the malware was seen intercepting network traffic to read SMS message contents, pick up international mobile subscriber identity (IMSI) numbers, as well as access the source and destination phone numbers for phone calls. The researchers said that this stolen data – particularly the IMSI numbers — shows the “highly targeted nature of this cyber-intrusion.”
Overall in 2019, researchers said they observed four different telecom organizations targeted by APT41 actors (Threatpost has asked the firm for information as to which carriers were affected and will update this post with any new information).
MessageTap is initially loaded onto the servers via an installation script (Threatpost has reached out to researchers for further comment on how the installation script infects the servers). Once installed, the malware checks for two files (keyword_parm.txt and parm.txt).
These two files contain instructions for the malware to target and save contents of certain SMS messages. From there, the malware attempts to read the configuration files every 30 seconds.
“Both files are deleted from disk once the configuration files are read and loaded into memory,” said researchers. “After loading the keyword and phone-data files, MessageTap begins monitoring all network connections to and from the server. It uses the libpcap library to listen to all traffic and parses network protocols starting with Ethernet and IP layers.”
The malware then extracts from network traffic the SMS message data contents using certain keywords, as well as certain IMSI numbers (using predetermined numbers on an imsiMap list) and phone number source and destinations (with predetermined numbers in the phoneMap list).
“If an SMS message contained either a phone number or an IMSI number that matched the predefined list, it was saved to a CSV file for later theft by the threat actor,” researchers said. “Similarly, the keyword list contained items of geopolitical interest for Chinese intelligence collection. Sanitized examples include the names of political leaders, military and intelligence organizations, and political movements at odds with the Chinese government. If any SMS messages contained these keywords, MessageTap would save the SMS message to a CSV file for later theft by the threat actor.”
APT41 is a threat group that researchers have found historically (since 2012) conducting dual Chinese state-sponsored espionage activity and personal financially-motivated activity. Researchers for their part said that this newly-discovered malware shows that APT41 – and other attributed state-sponsored hacking groups – won’t slow down any time soon. With this in mind, it’s important for “highly targeted individuals” – such as dissidents, journalists and officials – to adopt extra security precautions, according to the analysis.
“The use of MessageTap and targeting of sensitive text messages and call detail records at scale is representative of the evolving nature of Chinese cyber-espionage campaigns observed by FireEye,” researchers said. “APT41 and multiple other threat groups attributed to Chinese state-sponsored actors have increased their targeting of upstream data entities since 2017.”
What are the top mistakes leading to data breaches at modern enterprises? Find out: Join experts from SpyCloud and Threatpost senior editor Tara Seals on our upcoming free Threatpost webinar, “Trends in Fortune 1000 Breach Exposure.” Click here to register.