Researchers warn that APT41, a notorious China-linked threat group, has targeted more than 75 organizations worldwide in “one of the broadest campaigns by a Chinese cyber-espionage actor observed in recent years.”
Between Jan. 20 and March 11, researchers observed APT41 exploiting vulnerabilities in Citrix NetScaler/ADC, Cisco routers and Zoho ManageEngine Desktop Central as part of the widespread espionage campaign. Researchers said it’s unclear if APT41 attempted exploitation en masse, or if they honed in on specific organizations — but the victims do appear to be more targeted in nature.
“While APT41 has previously conducted activity with an extensive initial entry such as the trojanizing of NetSarang software, this scanning and exploitation has focused on a subset of our customers, and seems to reveal a high operational tempo and wide collection requirements for APT41,” wrote Christopher Glyer, Dan Perez, Sarah Jones and Steve Miller with FireEye, in a Wednesday analysis.
Dozens of companies were targeted from varying industries, including banking and finance, defense industrial bases, government, healthcare, legal, manufacturing, media, non-profit, oil and gas, transportation and utilities. APT41 also targeted firms from a broad array of countries, including Australia, Canada, Denmark, Finland, France, India, Italy, Japan, Malaysia, Mexico, Philippines, Poland, Qatar, Saudi Arabia, Singapore, Sweden, Switzerland, UAE, the U.K. and the U.S.
Cisco, Citrix and Zoho Exploits
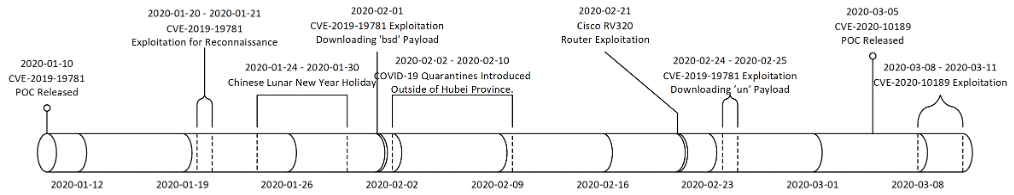
Starting on Jan. 20, researchers observed the threat group attempting to exploit the notorious flaw (CVE-2019-19781) in Citrix Application Delivery Controller (ADC) and Citrix Gateway devices revealed as a zero-day then patched earlier this year. It was disclosed on Dec. 17 – and proof of concept (PoC) code was released shortly after – before a patch was issued in January.
In this campaign, researchers observed three waves of exploits against CVE-2019-19781 – the first on Jan. 20 – 21, the second on Feb. 1, and finally a “significant uptick” in exploitation on Feb. 24 – 25.
Post-exploit, APT41 executed a command (‘file /bin/pwd’) on affected systems that researchers say may have achieved two objectives: “First, it would confirm whether the system was vulnerable and the mitigation wasn’t applied,” researchers noted. “Second, it may return architecture-related information that would be required knowledge for APT41 to successfully deploy a backdoor in a follow-up step.”
On Feb. 21, researchers next observed APT41 switching gears to exploit a Cisco RV320 router (Cisco’s WAN VPN routers for small businesses) at a telecommunications organization. After exploitation, the threat actors downloaded an executable and linkable format (ELF) binary payload. Researchers aren’t sure what specific exploit was used in this case, but pointed to a Metasploit module combining two CVEs (CVE-2019-1653 and CVE-2019-1652) to enable remote code execution on Cisco RV320 and RV325 small business routers.
Finally, on March 8, the threat actor was observed exploiting a critical vulnerability in Zoho ManageEngine Desktop Central, an endpoint management tool to help users manage their servers, laptops, smartphones, and more from a central location. The flaw (CVE-2020-10189) was first disclosed on March 5 as a zero-day, and was later patched on March 7. The attackers exploited the flaw to deploy payloads (install.bat and storesyncsvc.dll) in two ways. First, after exploiting the flaw they directly uploaded a simple Java-based program (“logger.zip”) containing a set of commands, which then used PowerShell to download and execute the payloads. In a second attack, APT41 leveraged a legitimate Microsoft command-line tool, BITSAdmin, to download the payload.
Notably, after exploitation, the attackers have been seen only leveraging publicly available malware, including Cobalt Strike (a commercially available exploitation framework) and Meterpreter (a Metasploit attack payload that provides an interactive shell from which an attacker can explore the target machine and execute code). Said researchers: “While these backdoors are full featured, in previous incidents APT41 has waited to deploy more advanced malware until they have fully understood where they were and carried out some initial reconnaissance.”
APT41 Activity
Interestingly, between waves of exploitation, researchers observed a lull in APT41 activity. The first lull, between Jan. 23 and Feb. 1, was likely related to the Chinese Lunar New Year holidays (which occurred Jan. 24 – 30): “This has been a common activity pattern by Chinese APT groups in past years as well,” said researchers.
The second lull, occurring Feb. 2 – 19, may have been related to fallout from the rapid spread of the coronavirus pandemic. Researchers noted that China had initiated COVID-19 related quarantines in cities in the Hubei province Jan. 23 – 24, and rolled out quarantines to additional provinces starting between Feb. 2 and Feb. 10.
“While it is possible that this reduction in activity might be related to the COVID-19 quarantine measures in China, APT41 may have remained active in other ways, which we were unable to observe with FireEye telemetry,” said researchers.
They also said that APT41 has historically (since 2012) conducted dual Chinese state-sponsored espionage activity and personal, financially motivated activity. More recently, in October 2019, the threat group was discovered using a new malware strain to intercept telecom SMS server traffic and sniff out certain phone numbers and SMS messages – particularly those with keywords relating to Chinese political dissidents.
“In 2020, APT41 continues to be one of the most prolific threats that FireEye currently tracks,” said researchers on Wednesday. “This new activity from this group shows how resourceful and how quickly they can leverage newly disclosed vulnerabilities to their advantage.”
Do you suffer from Password Fatigue? On Wednesday April 8 at 2 p.m. ET join Duo Security and Threatpost as we explore a passwordless future. This FREE webinar maps out a future where modern authentication standards like WebAuthn significantly reduce a dependency on passwords. We’ll also explore how teaming with Microsoft can reduced reliance on passwords. Please register here and dare to ask, “Are passwords overrated?” in this sponsored webinar.