Security researchers are warning of a new spam campaign targeting Brazilian institutions that contain Compiled HTML file attachments that are used to deliver a banking Trojan.
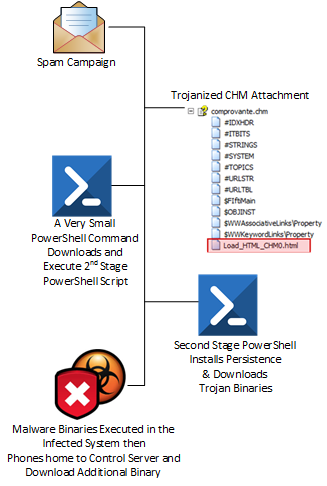
Spam messages contain a malicious CHM attachment called “comprovante.chm”, wrote Rodel Mendrez, senior security researcher at Trustwave in a technical write-up outlining the research.
He added, the multiple stage infection technique used to deliver the Trojan is effective at obfuscating the malware from detection. Currently only eight out of 60 AV scanners identified the CHM file attachments as malicious, he said.
 Attackers are taking advantage of the proprietary Microsoft online help format called Microsoft Compiled HTML Help, or CHM. CHM files are interactive and can run JavaScript, for example, which the attackers use to redirect victims to external URLs. CHM files have been used in several recent attacks including ones in November carried out by the Silence Gang.
Attackers are taking advantage of the proprietary Microsoft online help format called Microsoft Compiled HTML Help, or CHM. CHM files are interactive and can run JavaScript, for example, which the attackers use to redirect victims to external URLs. CHM files have been used in several recent attacks including ones in November carried out by the Silence Gang.
“Once a user opens the CHM, it executes a small PowerShell command that downloads a second stage PowerShell script. Persistence is then gained by creating a scheduled task to run the malware when the user logs in,” Mendrez said.
The researcher said when the CHM file containers are uncompressed it consists of HTML objects, one of which is “Load_HTML_CHM0.html.”
“When the Microsoft Help viewer (hh.exe) loads this HTML object, it runs a JavaScript function named open(),” Mendrez said. “This function open() decodes a block of data which then undergoes two layers of decoding with Base64 and XOR.”
After the data is decoded it forms a ClassID object which enables a malicious PowerShell script.
“So the attack can fly under the radar, the PowerShell command runs silently in the background by terminating instances of “hh.exe” (a program that runs the CHM file) and setting the window-style as hidden. It then invokes a command encoded in Base64 that downloads a second stage PowerShell script hosted in Google Sites,” the researcher wrote.
That triggers a second Bancos Trojan binary to be downloaded to the “%Appdata%\Sysinit” folder and then copied to “%Appdata%\SysRun,” he said. Key executable binaries downloaded are Server.bin, cmd.bin, XSysInit.bin (used to capture mouse and keyboard activity) and CRYPTUI.DLL (capable of downloading additional payloads).
The attack sequence includes three scheduled tasks. One is to run the malware when the user logs in. The second is forcing the targeted system to reboot via a malicious PowerShell script. Lastly, the Server.bin is executed which loads the file CRYPTUI.DLL, which can download new payloads.
“When the DLL is loaded (CRYPTUI.DLL), it spawns and injects its malicious code to a new process named iexpress.exe. It then obtains system information such username and computer name and reports back to its control server,” the researcher wrote.
“The attack above highlights multiple stages of malware infection originating from an email with a trojanized CHM attachment… The use of multiple stages of infection is a typical approach for attackers to stay under radar of AV scanners. As a matter of fact, as of this writing only 8 out of 60 AV scanners can detect it more than a month after we discovered this sample,” Mendrez said.










