Google introduced new security mitigations for its Chrome browser to defend against recently discovered Spectre variants.
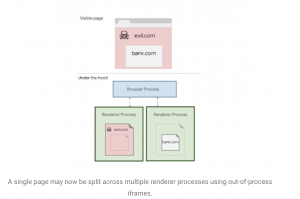
The new security feature, called site isolation, essentially isolates different browser work processes between various browser tabs. That means one tab’s webpage rendering and functions won’t interfere with what is happening in another. It has now been pushed out to most users of Chrome 67, released in May, for platforms Windows, Mac, Linux and ChromeOS, said Google.
“Speculative execution side-channel attacks like Spectre are a newly discovered security risk for web browsers,” said Google software engineer Charlie Reis in a Wednesday post. “A website could use such attacks to steal data or login information from other websites that are open in the browser.”
Site Isolation is nothing new. It’s been optionally available as an experimental enterprise policy since Chrome 63 for customers. But, said Reis, many known issues have been resolved since then, making it practical to enable by default for all desktop Chrome users.
On Tuesday, more Spectre variants were disclosed – dubbed Spectre1.1 and a subset, Spectre1.2, collectively referred to as Variant 4 of Spectre by Intel and ARM.
Like the two Spectre and Meltdown variants disclosed in January, Variant 4 is a side channel analysis security flaw – meaning that it uses the speculative execution features of most CPUs to access parts of memory that should be off-limits to a piece of code, and then use timing attacks to discover the values stored in that memory.
However, Variant 4 uses a different process involving JavaScript code to extract information – and the most common use impacts web browsers.
“This is particularly relevant for web browsers, since browsers run potentially malicious JavaScript code from multiple websites, often in the same process,” said Reis. “In theory, a website could use such an attack to steal information from other websites, violating the Same Origin Policy.”
 Starting in January most leading browser providers – such as Safari, Edge and Chrome – all patched for Meltdown in their managed runtimes, and “these mitigations are also applicable to variant 4 and available for consumers to use today,” Intel said.
Starting in January most leading browser providers – such as Safari, Edge and Chrome – all patched for Meltdown in their managed runtimes, and “these mitigations are also applicable to variant 4 and available for consumers to use today,” Intel said.
However, Google said that the most effective mitigation beyond these patches is through an approach such as site isolation, which could isolate valuable data in a different process – even if a Spectre attack does occur.
Site isolation still comes with known issues – according to the Chromium Project website, the process means a higher memory use of about 10 to 13 percent in Chrome. Google said that its team “continues to work hard to optimize this behavior to keep Chrome both fast and secure.”
Google said that other major browser vendors are finding related ways to defend against Spectre by better isolating sites. “We are collaborating with them and are happy to see the progress across the web ecosystem,” said Reis.
Microsoft Edge and Safari did not respond to requests for comment from Threatpost.










