A critical Cisco vulnerability exists in its administrative management tool for Cisco network security solutions. The flaw could allow an unauthenticated, remote attacker to gain administrative privileges on impacted devices.
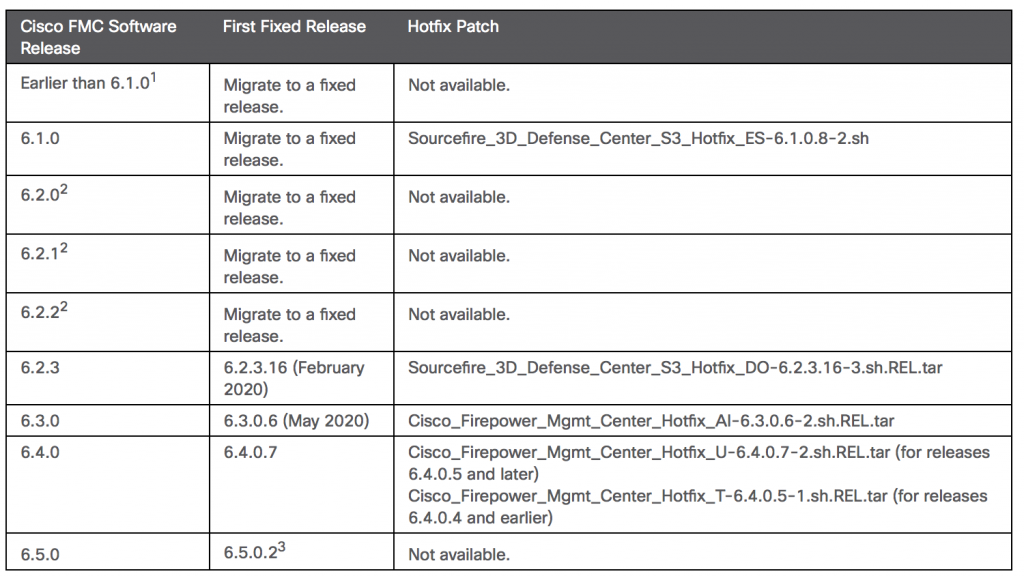
The flaw exists in the web-based management interface of the Cisco Firepower Management Center (FMC), which is its platform for managing Cisco network security solutions, like firewalls or its advanced malware protection service. Cisco has released patches for the vulnerability (CVE-2019-16028), which has a score of 9.8 out of 10 on the CVSS scale, making it critical in severity.
“The Cisco Product Security Incident Response Team (PSIRT) is not aware of any public announcements or malicious use of the vulnerability that is described in this advisory,” Cisco said in its advisory released Wednesday.
The vulnerability stems from “improper handling” of Lightweight Directory Access Protocol (LDAP) authentication responses from an external authentication server. LDAP is an industry standard application protocol used to access and manage directory information over an IP network.
LDAP is used for a variety of functions within FMC, such as FMC Web Management Portal Authentication, Remote Access VPN Authorization, command line interface authorization, and others. This vulnerability impacts only the FMC Web Management Portal if it is configured to authenticate users of the web management portal through an external LDAP server.
An attacker could exploit this vulnerability by sending crafted HTTP requests to a vulnerable device, Cisco said. They could then bypass authentication and gain administrative access to the web-based management interface of the affected device.
According to Omar Santos, principal engineer for the Cisco PSIRT, Cisco customers can do the following to determine whether they are impacted:
- Check if the Cisco FMC Software is configured to authenticate users of the web-based management interface through an external LDAP server;
- Check if external authentication using an LDAP server is configured on the device (System > Users > External Authentication)
Overall, Cisco released updates addressing 27 flaws on Wednesday, including the critical flaw, seven high-severity vulnerabilities and 19 medium-severity glitches. Some of the patched high-severity flaws exist in Cisco’s TelePresence Collaboration Endpoint (a product designed to link two rooms so they resemble a single conference room), its SD-WAN solution, its IOS XR software and more.
It’s been a busy start to 2020 so far for Cisco in terms of security updates. Earlier this month, Cisco fixed two high-severity vulnerabilities in its products, including one in its popular Webex video conferencing platform, that could enable a remote attacker to execute commands.
Also earlier in January Cisco also patched three critical vulnerabilities (CVE-2019-15975, CVE-2019-15976, CVE-2019-15977) in its Data Center Network Manager (DCNM), for which a proof-of-concept exploit was later published.