A vulnerability in the Cisco WebEx Chrome Plugin, used by tens of millions for web conferencing in business environments, exposed computers to remote code execution.
Cisco has begun releasing updates that patch the flaw, details of which were disclosed Monday by Google Project Zero researcher Tavis Ormandy, who has made a number of high-profile discoveries and disclosures in popular enterprise and security software.
The core issue is what Ormandy calls a “magic URL” used by the extension during WebEx sessions. The researcher said attacks could be carried out so long as a URL request contains the string cwcsf-nativemsg-iframe-43c85c0d-d633-af5e-c056-32dc7efc570b.html; attackers could use this in an iframe, leaving users unaware of an active exploit.
“The extension uses nativeMessaging, so this magic string is enough for any website to execute arbitrary code (!!),” Ormandy wrote is a bug report posted to the Project Zero site.
There was a secret URL in WebEx that allowed any website to run arbitrary code. ¯_(ツ)_/¯ https://t.co/sAqZrDN4ad
— Tavis Ormandy (@taviso) January 23, 2017
An attacker hosting an exploit online would only need to convince someone running the Chrome extension to visit the site.
The vulnerability was privately disclosed last Thursday and by the weekend, the Chrome Web Store was blocking new installations of the extension. Cisco, meanwhile, had a fix in version 1.0.3 prepared as well, though Ormandy said there could still be an issue.
“Cisco have asked if limiting the magic URL to https://*.webex.com/… would be an acceptable fix. I think so, although this does mean any XSS on webex.com would allow remote code execution,” Ormandy said. “If they think that is an acceptable risk, it’s okay with me.”
The patch will roll out to users automatically.
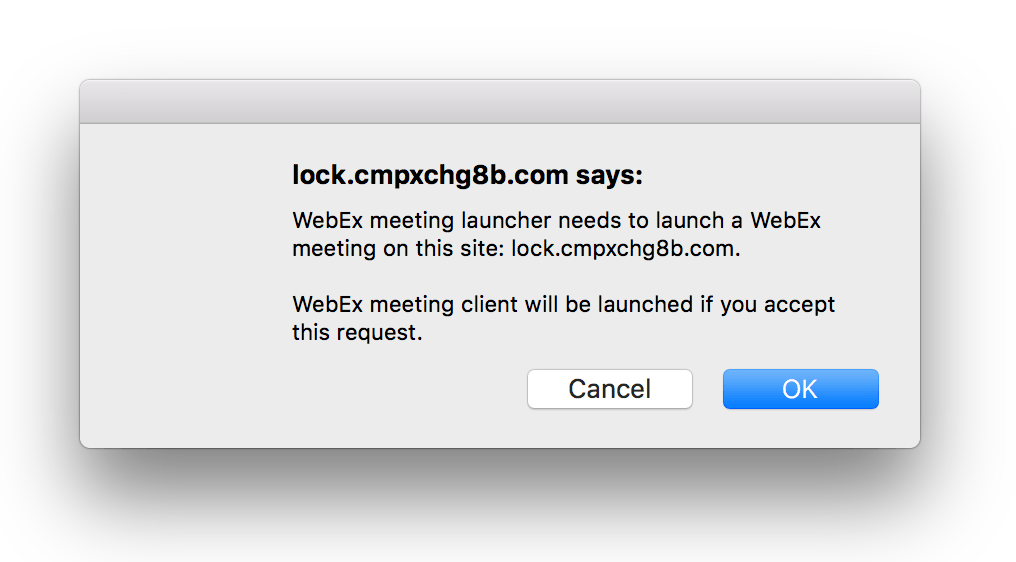
Researcher Filippo Valsorda of Cloudflare called the patch “weak” on Monday.
“All it does is show a popup like the following. Clicking OK will still cause malware to be installed,” he said.
Valsorda also cautioned: “Moreover, the webex.com website is still allowed to bypass the popup. If a vulnerability is found on the webex.com website, it can be used to compromise any machine running even the updated version.” Valsorda shared instructions on creating a dedicated WebEx profile he said would mitigate risk from the vulnerability.
The fix for arbitrary code execution on WebEx looks pretty sketchy. You might want to uninstall that extension ASAP. pic.twitter.com/B1xNnhuSSM
— Matthew Green (@matthew_d_green) January 24, 2017
Ormandy describes his dissection of the vulnerability in the bug report. As the extension invokes a command to launch a meeting, Ormandy found that a number of properties are passed during the session, some juicy enough for code execution. WebEx, Ormandy said, ships a copy of Microsoft’s C Runtime, CRT, which he used to execute system calls.
“Unbelievably, that worked,” said Ormandy, who also published a proof-of-concept exploit.
Ormandy is known for a slate of public disclosures of popular security and business software, including LastPass, Sophos, Symantec, Kaspersky, FireEye and others that have been patched.