 Web based attacks and botnets kept enterprises on the defensive in the third quarter, 2010, according to data released by Cisco Systems.
Web based attacks and botnets kept enterprises on the defensive in the third quarter, 2010, according to data released by Cisco Systems.
The company’s latest Global Threat Report – a compendium of security data compiled from across the networking giant’s customer base – shows that the average enterprise was targeted by 133 Web-based malware attacks a month during July, August and September.
The report, which was released on Wednesday, presents a snapshot of enterprise-focused malicious activity and shows that Web-based attacks, botnets and spam continue to be the most common threats facing enterprises across different verticals.
On the topic of Web-based attacks, Cisco said the majority of the attacks it identified – 65% – were blocked in some fashion – for example, using Cisco’s ScanSafe Web filtering technology. Of those attacks that were successfully carried out, those targeting security holes in Sun Java, Adobe’s Reader and Acrobat applications and the Flash presentation technology were the most common, Cisco said.
SQL injection attacks, a common form of Web based attack, were the single biggest category of event handled by Cisco’s Remote Operations Services (ROS) on behalf of customers in Q3. Fully 36 percent of the events handled by ROS were related to SQL injection during the summer months.
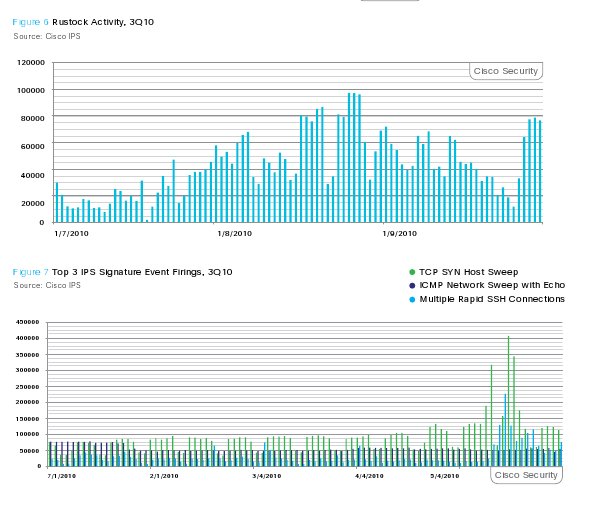
The SCADA-sniffing Stuxnet worm, which was a focus of media coverage, also affected Cisco customers. Stuxnet-related issues accounted for around 5% of the issues handled by Cisco ROS during the summer months. Much more prevalent were Rustock botnet infections, which made up 21% of all the ROS issues in Q3.
Rustock was a leading source of spam message traffic in the first half of 2010 and its takedown, as well as those of other spam-spewing botnets, has been registered as a drop in spam volume, especially in August. Kaspersky Lab’s Q3 Spam report found that, and Cisco’s global spam trend data also found a drop in spam volume between August and September – albeit from a eye-popping 326 billion messages a day in August to a only somewhat less eye-popping 257 billion per day in September.
Finally, messages masquerading as legitimate e-mail from social network LinkedIn hit Cisco’s corporate clients in a big way. Spoofed LinkedIn mail comprised 31% of all spam intercepted by Cisco at the height of the attacks in late September and early October. Those messages contained links to drive by download Web sites that pushed out variants of the Zeus Trojan, according to Cisco.
Cisco’s Third Quarter, 2010 Global Threat Report is available for download.









