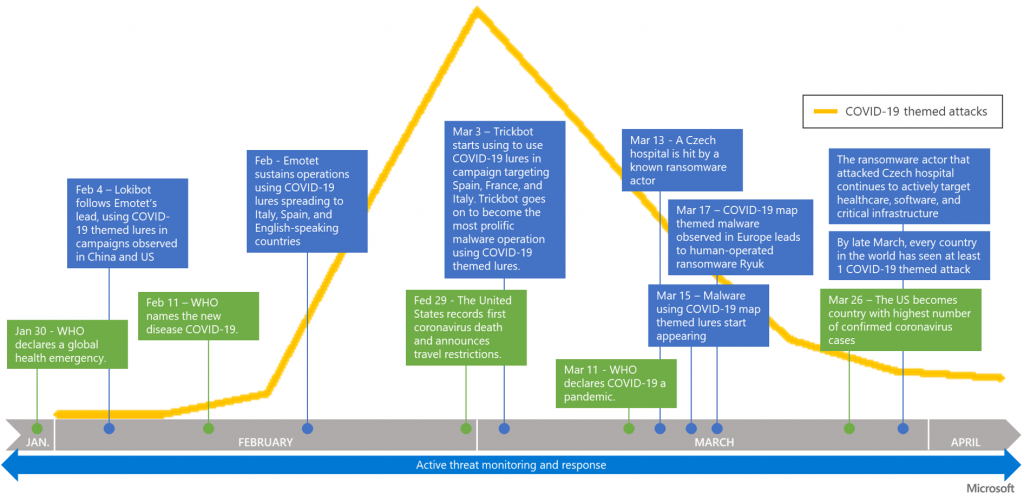
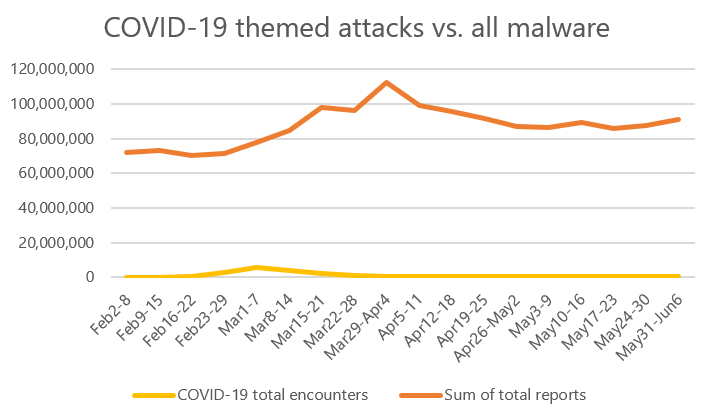
A report from the Microsoft Threat Protection Intelligence Team found that Covid-19-themed cyberattacks peaked in early March and are now trending significantly down. The report also noted that those attacks have been a drop in the bucket compared to overall threats observed over the last four months.
The report, which examined how cyberattacks exploited the crisis, found that attackers used local lures and preyed on people’s “concern, confusion, and desire for resolution” with mainly phishing campaigns aimed at spreading malware, committing identity theft or creating other disruptions.
“Cybercriminals are looking for the easiest point of compromise or entry,” researchers wrote in the report. “One way they do this is by ripping lures from the headlines and tailoring these lures to geographies and locations of their intended victims.”

Curiously, while attacks themselves increased due to COVID-19, overall trend of malware detection worldwide did not vary significantly, researchers found, calling the spike of pandemic-themed attacks “barely a blip in the total volume of threats we typically see in a month.”
Instead of creating new types of malware to use during the pandemic, Microsoft’s threat intelligence on endpoints, email and data, identities and apps concluded that “this surge of COVID-19 themed attacks was really a repurposing from known attackers using existing infrastructure and malware with new lures.”
The report highlights three countries—the United Kingdom, South Korea and the United States–and tracks the path of cyber attacks related to Covid-19 in those regions.
While coronavirus-themed attacks began roughly at the same time in those countries even though their outbreaks tracked differently, research shows attackers adapting to the level of attention and concern people in each region had regarding the virus, researchers said.
All three countries saw a spike in attacks in early March even though, for example, South Korea was hit by the virus earlier than the United Kingdom or the United States. However, attackers clearly followed the news in each country and increased attacks whenever there was a spike in interest or attention regarding the outbreak in the particular region, researchers found.
In the United Kingdom, for example, “data shows a first peak approximately at the first confirmed COVID-19 death in the UK, with growth beginning again with the FTSE 100 stock crash on March 9, and then ultimately peaking around the time the United States announced a travel ban to Europe,” researchers found.
Later, in early April, as the United Kingdom began providing more information to the public about Covid-19 and imposing lockdown measures, attacks dropped off, but when Prime Minister Boris Johnson was hospitalized on April 6 due to COVID-19 and then moved to intensive care, attacks surged, dropping off until April 12 when he was released from the hospital.
After that attacks flattened out until the end of April, when U.K. authorities announced the peak of infections, after which “attacks took a notable drop to around 2,000 daily attacks,” researchers said.
Attack cycles in South Korea and the United States followed similar trajectories, spiking whenever there was a significant news event related to the attack in that country and then tapering off when the pandemic assumed a more “business as usual” role in the news cycle, according to the report.
Researchers expect cybercriminals will be similarly opportunistic regarding not just COVID-19 but also any future global events. Going forward, organizations can use their time and resources most wisely in cross-domain signal analysis, update deployment and user education to mitigate such attacks.
“These COVID-19 themed attacks show us that the threats our users face are constant on a global scale,” researchers wrote. “Investments that raise the cost of attack or lower the likelihood of success are the optimal path forward.”
Insider threats are different in the work-from home era. On June 24 at 2 p.m. ET, join the Threatpost edit team and our special guest, Gurucul CEO Saryu Nayyer, for a FREE webinar, “The Enemy Within: How Insider Threats Are Changing.” Get helpful, real-world information on how insider threats are changing with WFH, what the new attack vectors are and what companies can do about it. Please register here for this Threatpost webinar.