Armorblox researchers have spotted an ongoing credential-phishing attack that spoofs an encrypted Zix email – one coming, weirdly enough, from what looks like a legitimate domain associated with the Baptist religion.
At least, the threat actor is sending the phishing attack from “thefullgospelbaptist[.]com”: a domain that might be a deprecated or old version of a legitimate Baptist domain, fullgospelbaptist[.]org, which is a religious organization established in 1994.
In a Tuesday post, researchers said that, to date, the fake-Zix encrypted email has targeted close to 75,000 inboxes and has slipped past embedded spam and security controls across Office 365, Google Workspace, Exchange, Cisco ESA and others.
God isn’t sending encrypted Zix messages: If hapless users click on the spoofed email’s link, it will try to download a presumably unholy HTML file onto their system.
The attack is targeting a range of companies across sectors including state and local government, education, financial services, healthcare, and energy, selectively going after a mix of senior executives and cross-departmental employees.
In fact, Armorblox’s research team found that the attacker is cherry-picking targets, being careful to select no more than one employee in any single department, probably to forestall the “Hey, did you get this weird email?” chat among officemates.
The Bogus Zix Email
Zix is a key player in the email encryption market, right up there with Cisco Systems, Trend Micro, Proofpoint, Sophos and Norton LifeLock, et al.
Building on the name recognition alone helps the email to pass a sniff test it should rightfully flunk. But beyond the brand name alone, the email attack also uses a “gamut” of additional techniques to evade traditional security filters and to “pass the eye tests of unsuspecting end users,” Armorblox explained, including social engineering, exploiting a legitimate-looking Baptist domain and replication of existing workflows.
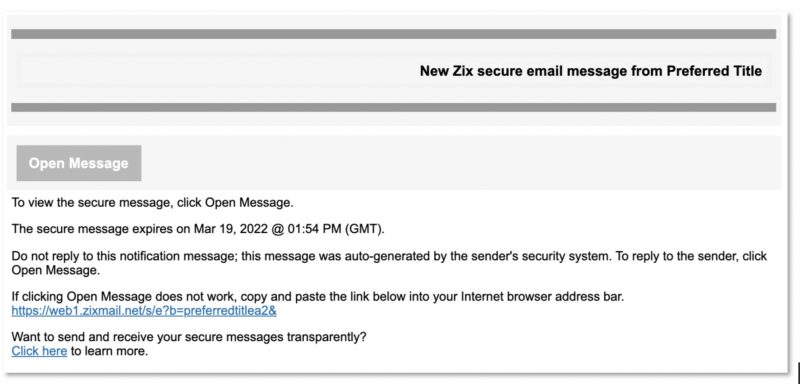
The subject header is “Secure Zix message.” The email body’s header reiterates that title and tells the intended victim that they’ve received a secure Zix message. Click on the “Message” button to check it out, the email instructs.
Armorblox provided screenshots of both a genuine Zix secure message and the spoofed Zix secure message notification. As you can see below, the two interfaces aren’t identical, but they’re close enough to trick unsuspecting users.
Satan Wants Select Employees to Click on ‘Message’
Clicking on the “Message” link in the email will trigger an attempted drive-by download of an HTML file named “securemessage.” Armorblox researchers couldn’t open that file in their virtual machine (VM) instance, since that’s not where the redirect appeared. Fortunately, by the time researchers wrote up the attack, most site blockers were erecting a block page to prevent systems from getting infected.
As far as the threat actor’s preferred prey goes, Armorblox had a few examples: For example, one of the SLED (state and local government and education) businesses that Armorblox counts as customers experienced an attack wherein the targets included the CFO, a director of operations, a director of marketing and a professor.
Another example: The credential phishers went after a wellness company, targeting the senior vice president of finance and operations, the president, and a utility email alias (member.services@company[.]com).
Why such a seemingly random spread? The researchers theorized that the attackers might have deliberately chosen their victims “to be across departments and to contain a good mix of senior leadership and individual contributors.”
As well, the attackers may have gone after people who don’t tend to turn to each other if they receive a suspicious email, Armorblox explained.
Slippery Techniques
Armorblox summed up these techniques that the spoofed Zix email is using to evade traditional email security filters and watchful eyes:
- Social engineering: The email title, design, and content aimed to induce a sense of trust and urgency in the victims – a sense of trust because the email claimed to come from a legitimate company (Zix), and a sense of urgency because it claimed the victim was sent a secure message – something they would be eager to view. The context of this attack also leverages the curiosity effect, which is a cognitive bias that refers to our innate desire to resolve uncertainty and know more about something.
It’s easy to see how getting an email that somebody bothered to encrypt could pique recipients’ curiosity. A May 2021 report from Security Advisor found that the curiosity effect – the desire to resolve uncertainty – has shown up as one of the top three cognitive biases to be exploited in phishing attacks, appearing in 17 percent of such attacks.
- Brand impersonation: The email has HTML stylings and content disclaimers similar to real emails from Zix. While not a perfect replica of the real thing, it bears enough resemblance to a legitimate email to be dangerous.
- Exploiting legitimate domain: The parent domain of the email sender was a deprecated or old version of a legitimate domain – ‘thefullgospelbaptist[.]com’. This helped the email bypass authentication checks.
Armorblox researcher Abhishek Iyer told Threatpost on Monday that using legitimate (if unrelated) domains to send emails “is more about tricking security controls (i.e. bypassing authentication checks) than it is about tricking recipients, especially if the domains are not spoofed to look like the real thing.”
An example that Armorblox came across last year was a Verizon credential phishing campaign where the page was hosted on the website of a Wiccan coven. Another example: an Amazon credential phishing campaign where the email was sent from the domain of Blomma Flicka Flowers, a small floral design company based out of Vermont. The campaign aimed to lift credentials and other personal information under the guise of Amazon package-delivery notices.
“Whether these domains are used to send the email or host the phishing page, the attackers’ intent is to evade security controls based on URL/link protection and get past filters that block known bad domains,” Iyer said via email.
Needless to say, the legitimate Baptist organization had nothing to do with the Zix campaign, he continued. “To host phishing pages on legitimate domains, attackers usually exploit vulnerabilities in the web server or the Content Management Systems (CMS) to host the pages without the website admins knowing about it.”
- Replicating existing workflows: The context for the email attack replicates workflows that already exist in our daily work lives (getting encrypted email notifications). When we see emails we’ve already seen before, our brains tend to employ System 1 thinking and take quick action. The email content even had every victim’s first name filled in to increase the feeling of legitimacy and the chances of follow through.
“System 1 thinking” is a reference to Daniel Kahneman’s book, “Thinking, Fast and Slow,” which delves into our brains’ two information processing and decision making systems, System 1 being “the automatic, unconscious, and fast mode of thinking, offering little to no rationale behind its actions.” System 2 thinking is what we need when we look into our inboxes: That’s the “slow, methodical, and analytical mode of thinking, skeptical and rational by default,” Armorblox explained.
“Security awareness training programs require us to operate in the System 2 mode of thinking, encouraging us to be suspicious of emails we receive,” Armorblox co-founder Arjun Sambamoorthy recommended in a post earlier this month.
Phishing Is Getting Harder to Spot
In a recent column for Threatpost’s InfoSec Insider series, Troy Gill, manager of security research at Zix, discussed the most common ways sensitive data is scooped up by nefarious sorts. His thoughts on how easy it is for any of us to fall for increasingly sophisticated phishing attempts such as the Zix spoofed email:
“Everyone wants to believe that they wouldn’t fall victim to typical phishing scams. However, the truth is that these methods of intrusion are getting harder to spot as cybercriminals become more savvy with their tactics. Cybercriminals continue to build on trickier spear-phishing strategies that rely on brand-new techniques and even more deceitful tricks that can catch even the most discerning person unaware.” —Troy Gill, Threatpost InfoSec Insider column.
How to Protect Your Business
Armorblox provided this guidance and recommendations to keep the credential-phishers at bay:
- Augment native email security with additional controls
The spoofed Zix email got past the security controls of Office 365, Google Workspace, Exchange, Cisco ESA and others. Armorblox recommended that for better protection coverage against email attacks, be they spear-phishing, business email compromise (BEC) or credential phishing attacks like this one, “organizations should augment built-in email security with layers that take a materially different approach to threat detection.”
The screenshot below shows the spoofed Zix email with a Spam Confidence Level (SCL) score of -1. As Microsoft outlines in its matrix of spam confidence level (SCL) in Exchange Online Protection, a rating of -1 means that the message skipped spam filtering and was delivered, since it was assumed to be “from a safe sender, was sent to a safe recipient, or is from an email source server on the IP Allow List.”

The email has an SCL score of -1, which means it skipped Microsoft’s spam filters. Source: Armorblox.
- Watch out for social engineering cues
“Since we get so many emails from service providers, our brains have been trained to quickly execute on their requested actions. It’s much easier said than done, but engage with these emails in a rational and methodical manner whenever possible,” researchers recommended. “Subject the email to an eye test that includes inspecting the sender name, sender email address, language within the email, and any logical inconsistencies within the email (e.g. Why is a Zix link leading to an HTML download? Why is the sender email domain from a third-party organization?).”
- Follow MFA and password management best practices
“Since all workplace accounts are so closely interlinked, sharing credentials to one of your accounts can prove to be very dangerous as cybercriminals send emails in your name to trick your customers, partners, acquaintances, and family members,” Armorblox said.
Its specific recommendations:
If you haven’t already, implement these hygiene best practices:
- Deploy multi-factor authentication (MFA) on all possible business and personal accounts.
- Don’t use the same password on multiple sites/accounts.
- Use a password management software like LastPass or 1password to store your account passwords.
- Avoid using passwords that tie into your publicly available information (date of birth, anniversary date, etc.).
- Don’t repeat passwords across accounts or use generic passwords such as ‘password123’, ‘YourName123’, etc.
092821 14:27 UPDATE: Corrected misspellings of Armorblox. We regret the error.
Rule #1 of Linux Security: No cybersecurity solution is viable if you don’t have the basics down. JOIN Threatpost and Linux security pros at Uptycs for a LIVE roundtable on the 4 Golden Rules of Linux Security. Your top takeaway will be a Linux roadmap to getting the basics right! REGISTER NOW and join the LIVE event on Sept. 29 at Noon EST. Joining Threatpost is Uptycs’ Ben Montour and Rishi Kant who will spell out Linux security best practices and take your most pressing questions in real time.