A sophisticated criminal group operating for more than a year is utilizing a changing series of Internet protocol addresses, domains and gates in order to infect its victims with the Fiesta exploit kit.
Fiesta is among the handful of exploit kits to have emerged in the wake of the once prominent Blackhole, which wavered after its authorities arrested its alleged creator, Dmitry Fedotov, better known by the handle “Paunch.” While the Angler exploit kit is widely considered to be the most successful post-Blackhole kit, secondary ones such as Nuclear and Fiesta have garnered a decent amount of attention and driven substantial infections as well.
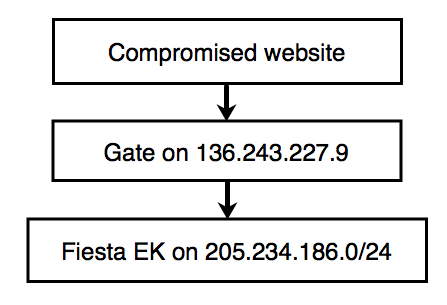
Brad Duncan, a security expert at the cloud management company, Rackspace, has been monitoring a threat group that uses Fiesta for more than year. In an entry on the SANS Institute’s information security forums, he explained that the group pulls traffic from compromised sites through a gate — or redirection domain — to a final, malicious domain hosting the kit.
Duncan is calling the group the “BizCN gate actor” because it exclusively uses gate domains purchased from www.bizcn.com, a Chinese domain registrar. Duncan explains that the registrant’s information is protected, so he can’t see who is registering the malicious gateway sites, but that each of them resides on the same IP at the same time, currently 205[.]234[.]186[.]114. Earlier this month, he says, the malicious domains were hosted at 136[.]243[.]227[.]9. Following Duncan’s publication, it’s likely that the IP will change again.
Each unique gate domain is paired with a paired with its own compromised website.
“Organizations with web proxy logs can search for 136[.]243[.]227[.]9 to see the HTTP requests,” Duncan writes of this attack’s indicators of compromise. “Those HTTP headers should include a referrer line with the compromised website.”
At present, the group is using Fiesta to disseminate malware that copies itself into directories inside the victim’s appdata/local folder, from where it updates the registry keys in order to maintain persistence. Duncan’s write-up contains a link to the specific malware payload used in the attacks he monitored. The malware is classified differently by nearly every antivirus provider listed on VirusTotal.
Duncan warns that researchers could have trouble trying to analyze the threat, because it’s apparently difficult to achieve the full infection chain on purpose.