About one in five of the 80,000 companies affected by a critical bug in the Citrix Application Delivery Controller (ADC) and Citrix Gateway are still at risk from a trivial attack on their internal operations.
If exploited, the flaw could allow unauthenticated attackers to gain remote access to a company’s local network and carry out arbitrary code-execution. Researchers told Threatpost that other attacks are also possible, including denial-of-service (DoS) campaigns, data theft, lateral infiltration to other parts of the corporate infrastructure, and phishing.
According to an assessment from Positive Technologies, which disclosed the software vulnerability in December (tracked as CVE-2019-19781), 19 percent of vulnerable organizations in 158 countries have yet to patch. The U.S. originally accounted for 38 percent of all vulnerable organizations; about 21 percent of those are still running vulnerable instances of the products as of this week, PT said.
The Citrix products (formerly the NetScaler ADC and Gateway) are used for application-aware traffic management and secure remote access, respectively.
“Patching this bug should be an urgent priority for all remaining companies affected,” said Mikhail Klyuchnikov, an expert at PT who discovered the flaw, speaking to Threatpost. “The critical vulnerability allows attackers to obtain direct access to the company’s local network from the internet. This attack does not require access to any accounts, and therefore can be performed by any external attacker.”
He added, “The flaw is really easy to exploit. It’s also very reliable.”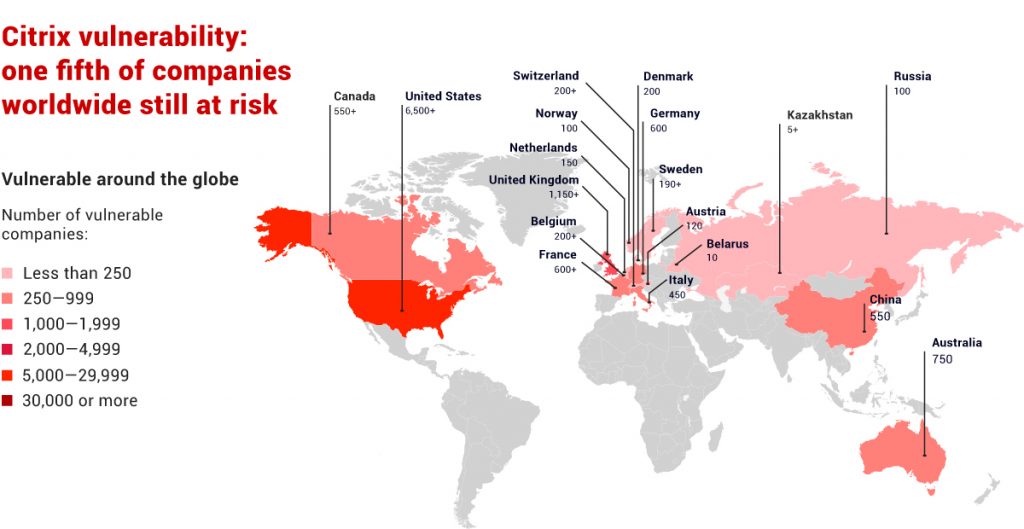
Since Citrix is mainly used for giving remote access to applications in companies’ internal networks, Klyuchnikov told Threatpost that a compromise could easily used as a foothold to move laterally across a victim organization.
“The critical information about applications accessible by Citrix can be leaked,” he explained. “That could possibly include information (and possibly credentials) about internal web applications, corporate applications, remote desktops and other applications available through the Citrix Gateway.”
Attackers also could gain the ability to read configuration files, he said; these contain sensitive information like user credentials, yet more information about the internal network and credentials for internal services (LDAP, RADIUS and so on).
“Depending on system settings, attackers can get administrative credentials for the Citrix Gateway, credentials (login, password, etc.) of company employees and credentials of other services used in Citrix Gateway [from the configuration files],” he said.
Adding insult to injury, various other kinds of attacks are possible as well.
“[An attacker] can conduct DoS attacks against Citrix Gateway, just deleting its critical files,” the researcher explained to Threatpost. “It can lead to unavailability of the login page of Citrix application. Thus, no one (e.g. company employees) can get access into internal network using Citrix gateway. In other words, the Citrix gateway application will cease to do its main task for which it was installed.”
It’s also possible to conduct phishing attacks. For example, a hacker can change the login page so that the entered username and password is obtained by the attacker as clear text.
And then there’s the remote code-execution danger: “An attacker can use a compromised application as part of a botnet or for cryptocurrency mining. And of course, it can place malicious files in this application,” Klyuchnikov noted.
In-the-wild attacks could be imminent: On January 8, a researcher released an exploit that allows a potential attacker to perform automated attacks. Others followed.
https://twitter.com/GossiTheDog/status/1214892555306971138
Citrix did not disclose many details about the vulnerability in its security advisory, however, Qualys researchers last month said that the mitigation steps offered by the vendor suggest the flaw stems from the VPN handler failing to sufficiently sanitize user-supplied inputs.
According to PT, the countries with the greatest numbers of vulnerable companies are led by Brazil (43 percent of all companies where the vulnerability was originally detected), China (39 percent), Russia (35 percent), France (34 percent), Italy (33 percent) and Spain (25 percent). The USA, Great Britain, and Australia each stand at 21 percent of companies still using vulnerable devices without any protection measures.
Last month, Citrix issued patches for several product versions to fix the issue, ahead of schedule.
“Considering how long this vulnerability has been around (since the first vulnerable version of the software was released in 2014), detecting potential exploitation of this vulnerability (and, therefore, infrastructure compromise) retrospectively becomes just as important [as patching],” Klyuchnikov said.
He added, “I think it’s easy to apply the patch, as there is already a regular update for the hardware that fixes the vulnerability. Nothing should get in the way, as there is a full update from Citrix.”
Learn how Operational Technology and Information Technology systems are merging and changing security playbooks in this free Threatpost Webinar. Join us Wednesday, Feb. 19 at 2 p.m. ET when a panel of OT and IT security experts will discuss how this growing trend is shaping security approaches for IoT and 5G rollouts. This webinar is for security and DevOps engineers, IoT edge developers and security executives.











