CANCUN, Mexico – Researchers have uncovered a new cyber-espionage threat, dubbed Slingshot, that targets routers and uses them as a springboard to attack computers within a network.
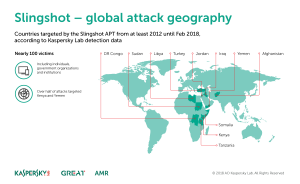
Kaspersky Lab, which released details of its discovery during its Security Analyst Summit on Friday, said that the campaign has successfully targeted at least 100 victims in the Middle East and Africa from at least 2012 until February 2018.
Alexey Shulmin, malware analyst at Kaspersky Lab, said at the conference that the Slingshot campaign represents a complex threat that employs a wide range of tools and techniques, including kernel mode modules: “We discovered a new highly sophisticated and complicated APT last year, this was one of the most complex frameworks,” he said.
 Kaspersky’s Shulmin and Sergey Yunakovsky, speaking at SAS, said Slingshot stands out for its unusual attack vector – the malicious actors infected victims through compromised MikroTik routers and placed a malicious dynamic link library inside it that acts as a downloader for other malicious components.
Kaspersky’s Shulmin and Sergey Yunakovsky, speaking at SAS, said Slingshot stands out for its unusual attack vector – the malicious actors infected victims through compromised MikroTik routers and placed a malicious dynamic link library inside it that acts as a downloader for other malicious components.
“When an administrator logs in to configure the router, the router’s management software downloads and runs the malicious module on the administrator’s computer. The method used to hack the routers in the first place remains unknown,” according to Kaspersky’s statement on Slingshot.
After infecting the router, Slingshot downloads an array of additional malware modules onto the device – including two particularly sophisticated ones called Cahnadr and GollumApp – that are linked and can support each other in gathering information.
GollumApp is the most sophisticated module, containing 1,500 user-code functions and providing most of the controls for persistence, file system control and C2 communications, according to Kaspersky. Meanwhile, Canhadr (aka NDriver), touts a kernel-mode program to execute malicious code without crashing the entire file system.
Researchers said that the threat is effective at stealthily gathering data, hiding traffic in data packets that adversaries can intercept without being traced by communications.
“Slingshot’s main purpose seems to be cyber-espionage. Analysis suggests it collects screenshots, keyboard data, network data, passwords, USB connections, other desktop activity, clipboard data and more, although its kernel access means it can steal whatever it wants,” according to Kaspersky.
Researchers said most of Slingshot’s victims appear to be targeted individuals rather than organizations, but there are some government organizations and institutions also targeted. While MikroTik routers were impacted, the company said that victims may have been infected through other routes.
Meanwhile, researchers said that the complexity of Slingshot could mean that it is the group behind it is highly organized and potentially state sponsored. Similarities in technique also exist between Slingshot and GRAYFISH operation, by the Equation Group, as well as Gray Lambert.
Researchers first came upon Slingshot when they found a suspicious keylogger program and created a behavioral detection signature to see if the code appeared anywhere else; which triggered detection of a suspicious file inside the system folder called scesrv.dll.
“Analysis of the file showed that despite appearing legitimate, the scesrv.dll module had malicious code embedded into it,” according to Kaspersky’s release. “Since this library is loaded by ‘services.exe,’ a process that has system privileges, the poisoned library gained the same rights. The researchers realized that a highly advanced intruder had found its way into the very core of the computer.”
To avoid falling victim to Slingshot, Kaspersky recommended that MikroTik users upgrade to the latest firmware version as soon as possible.