Researchers have uncovered a new business email compromise (BEC) threat actor, which they call Exaggerated Lion, targeting thousands of U.S. companies with money pilfering scams. The cybercrime ring is unique in its leveraging of Google’s cloud-based productivity suite, G Suite, and for its use of physical checks for collecting fraudulent payments – as opposed to wire transfers.
While only recently discovered, Exaggerated Lion has been behind scams dating back to at least 2013, researchers said. Unlike other BEC organizations, which are centrally located in Nigeria, the threat group’s primary associates are also spread around multiple countries in Africa, including Nigeria, Ghana, and Kenya. After researchers uncovered the cybercrime ring, they observed it targeting nearly 2,100 U.S. companies in four months.
“Exaggerated Lion’s M.O. has remained remarkably consistent over the years. They use very long domain names hosted on G Suite containing words that give the appearance that an email was sent from secure infrastructure,” said researchers with Agari in a report posted Thursday. “For Exaggerated Lion, their use of physical checks as a cashout mechanism sets them apart from other BEC groups and their evolution to creating fake documents that are commonly used in authentic business transactions to add legitimacy to their scams.”
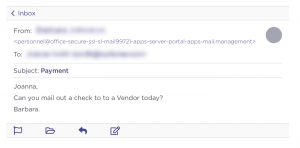
Researchers first started engaging with the threat group in April 2019 after observing an attempted attack on a customer’s Accounts Payable Specialist. The BEC attack’s initial email message impersonated the victim’s CEO and asked if a check could get mailed out to a “vendor”. Over time, the threat actor has also evolved their hooks to sometimes include fake invoices and W-9 forms attached to these initial emails to give them more legitimacy, researchers said.
Researchers responded to the email and pretended to be the targeted company in order to learn more about the threat group. Upon further communication, the threat group responded with the name and address of a “vendor” to which the victim should send a $17,640 check for “professional services,” saying that the check needs to be mailed out overnight.
The attack demonstrated that Exaggerated Lion is different from other BEC cybercriminal groups in a few ways. Most notably, attackers were asking for a physical check, which they would then use to cash out money pilfered through the BEC attacks. Other groups commonly use electronic wire payments or gift cards. Researchers believe that the use of physical checks is due to Exaggerated Lion’s previous experience and comfort with checks, because the group started as a check fraud scammers.
“Exaggerated Lion likely prefers to use physical checks rather than wire transfers because, while it might take longer to complete the transactions, they will likely be more lucrative in the long run,” Crane Hassold, senior director for threat research at Agari, told Threatpost. “These are legitimate checks getting deposited into legitimate bank accounts. And once the checks are successfully deposited, they money is funneled to the Exaggerated Lion scammers very quickly, making the funds harder to recover. Plus, Exaggerated Lion has built a large network of check mules in the US based on their long history running check fraud schemes.”
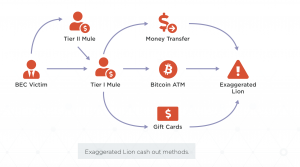
After a victim sends a check to a “vendor,” it reaches a money mule located at the address given, who then deposits the check into a bank account. The mule sends the money to Exaggerated Lion cybercriminals via a bank transfer, a Bitcoin ATM or via gift cards.
The cybercriminals also have a clear preference for using Google’s enterprise solution for cloud-based email, G Suite, as part of their delivery infrastructure.
In fact, researchers found that 1,400 domains used by Exaggerated Lion since July 2017 that have been used to launch BEC campaigns – and 98 percent of those domains were registered with Google.
It makes sense why the threat group would favor G Suite, researchers said. Google doesn’t start charging for G Suite until after the first month, meaning that the threat actor would have a 30-day free trial on each domain setup. And, by using G Suite, the threat actor wouldn’t have to worry about setting up any additional infrastructure (such as SMTP servers for sending emails).
As part of this tactic, when sending emails the threat group “has adopted one of the more unique and creative approaches to naming their domains we’ve seen,” researchers said.
 Rather than trying to resemble a target’s domain, or using words to indicate the domain is associated with a telecom provider (tactics previously used in BEC attacks), the threat group uses domains that were very long and consisted of various words (such as “secure,” “ssl,” “office,” “mail” and “executive”) separated by hyphens (See image to the left). While it clearly was not mimicking the customer’s domain, it seemed to be constructed to appear to come from secure infrastructure, researchers said.
Rather than trying to resemble a target’s domain, or using words to indicate the domain is associated with a telecom provider (tactics previously used in BEC attacks), the threat group uses domains that were very long and consisted of various words (such as “secure,” “ssl,” “office,” “mail” and “executive”) separated by hyphens (See image to the left). While it clearly was not mimicking the customer’s domain, it seemed to be constructed to appear to come from secure infrastructure, researchers said.
“Usually, when we see long domains like this, they are used to host phishing sites, but there are no indications that Exaggerated Lion has hosted any content — malicious or otherwise — on any of the domains they have registered. For all intents and purposes, these domains are solely used for setting up email accounts to launch BEC attacks,” researchers said.
Phishing scams continue to hit companies hard in terms of losses. Last week, the FBI in its IC3 annual cybercrime report said that business email compromise (BEC) attacks cost victims $1.7 billion in 2019. In 2019, these types of attacks scammed media conglomerate Nikkei ($29 million), a Texas school district ($2.3 million) and even a community housing nonprofit ($1.2 million). Other victims of scams include the City of Ocala in Florida, which was swindled out of $742,000, and a church in Brunswick, Ohio that was scammed out of $1.75 million in August.