The Cynet security platform takes a different approach to traditional point security offerings, by providing a consolidated solution to all aspects of breach protection through a single interface. Unlike endpoint security solutions that only focus on particular types of threats targeting the endpoints, Cynet protects the entire internal environment – including hosts, files, users and the network. The platform converges Endpoint protection and EDR, Network Analytics, User Behavior Analytics, Deception and Vulnerability Management into a single platform, deployed in minutes and easy to use for any size organization. The platform is also available for a free 14-day trial.
One of the points touted by Cynet is the platform’s ease-of-use, especially important in a market where security products are frequently challenging to deploy and navigate. The platform interface takes the capabilities needed by security professionals and presents them in a way that is more intuitive, making both the implementation process and product management more user-friendly. As it provides multiple capabilities, the Cynet platform is promoted as eliminating the need for multiple security product configurations, and makes the job easier for the personnel tasked with security management, even if it is an IT person and not a dedicated security professional.
The platform also comes (without additional cost) with the services of CyOps – a team of security experts who are online 24 hours a day, seven days a week for alerting about threats, proactive threat hunting and assisting in incident response.
Deployment: Fast and Easy
Deployment Options: On-premise, IAAS, SAAS and hybrid mode. Cynet can deploy across tens to hundreds of endpoints in minutes, without the usual technical issues like blue screens and IT downtime.
Immediate Visibility into 4 Areas: Endpoints, Users, Network & Files
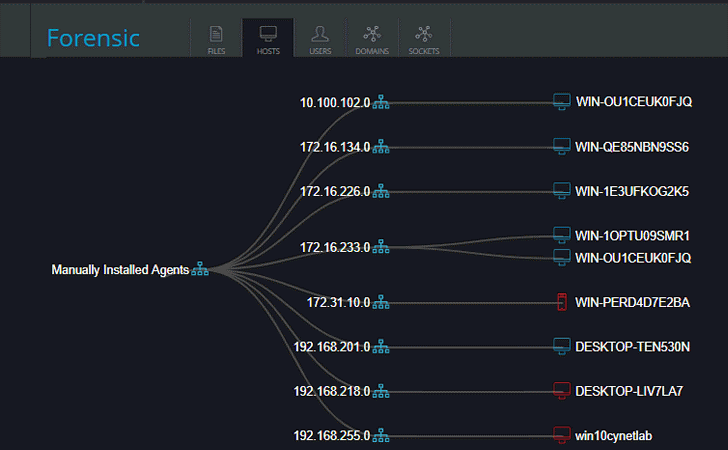
The Cynet dashboard offers users immediate visibility into the complete organizational network, showing the security team exactly what is going on in their internal system. This includes: user activities, host configurations, executed files and network traffic. Attacks are quickly identified by correlating across all anomalies, as well as file executions, network traffic and user behavior.
All active hosts are visible in this dashboard, within minutes after the platform’s launch:
This total environment visibility is in contrast to most security solutions, where only one aspect of activity is usually visible. Security practitioners can view the networks, sources, applications in use, inventory of hosts and vulnerabilities.
At-risk hosts are clearly marked and can be clicked for more detail.
Once installed, users can manage vulnerabilities and compliance issues. This includes:
- OS Updates: the Windows patches are checked and an alert is issued if missing, users also get a list of all current patches.
- Unauthorized applications: Blacklisted and customizable apps are identified and the user is updated if found.
- Out-of-date apps: If the platform identifies outdated app versions, it updates the user.
- Validation of security policies: Cynet reviews a list of agents to see if they are on the endpoints and running. If it finds anything missing, it alerts the user.
Users can also enter via the Forensic screen to access data on vulnerability management, for use in correlating risk. They can use this data to create reports and queries.
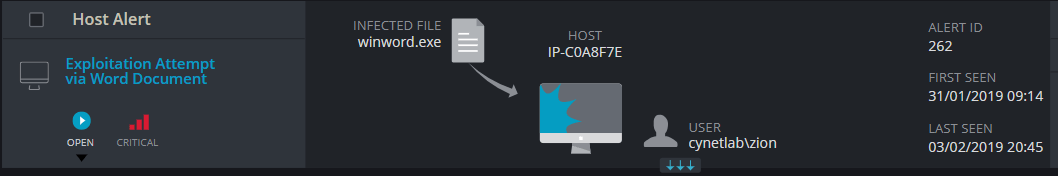
Within the Forensics area, users can search across the 4 main areas of files, hosts, users, and endpoints. Every image is clickable allowing users to deep-dive into its history. Red flaggable security issues can easily be addressed this way – old password alerts, files called up at startup, apps running on endpoints, unauthorized access to network visibility apps, and more.

Figure 7: All users that haven’t changed their password during a specific period and logged in over the last week
The Cynet platform presents information via objects, all can be clicked, allowing the user to access more information on a chronological timeline that includes history and activity.
Security professionals can also access and utilize all information the Cynet platform collects via a completely documented rest API.
Prevention with the Cynet platform
Files/running processes
Using multiple layers, Cynet can prevent execution altogether or kill malicious processes in runtime:
- Threat Intelligence – This includes more than 30 live feeds of Indicators of Compromise.
- Known Malware – Identify known signatures to prevent execution of malware.
- Machine learning based NGAV – Identify malicious attributes by analyzing files pre-execution using independent machine learning.
- Fuzzy Hashing – Identify files with known malware hash similarities.
- Memory Access Control – Protect critical memory areas to ensure only legitimate processes can gain access.
- Behavioral Analysis – detect and terminate malicious behavior by monitoring process at runtime.
Stopping Malicious Network Traffic
Network-based attackes stopped by Cynet include tunneling attacks, ARP poisoning, DNS responder and more. Automated traffic blocking can be achieved through alerts, ensuring proactive prevention.
Detection
Cynet converges detection, correlation and automation with analysis across endpoints, for users, files and networks – providing a level of protection absent in point solutions.
Detection capabilities include endpoint protection, Endpoint Detection and Response, User Behavior Analytics, network analytics and deception.
During live demos, alerts are issued for a broad range of threats including: ransomware, brute force, malicious behavior, user login anomalies, exploitation, lateral movement, credential theft DNS , privilege escalation and others.
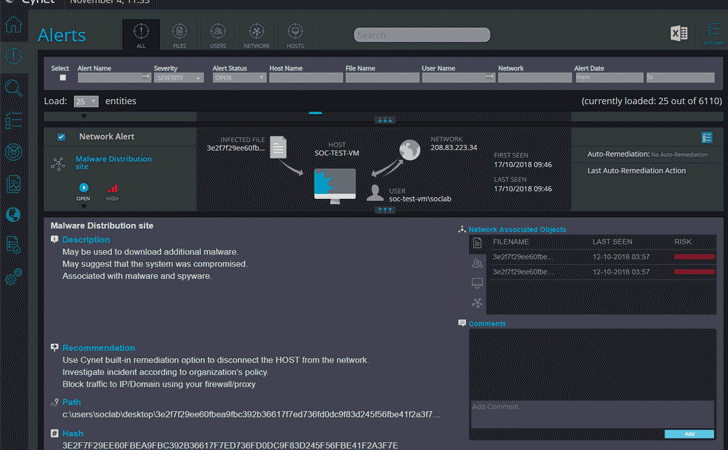
Cynet provides risk ranking for every alert, providing guidance to severity and order to action. Cynet does this by cross-correlating all the alert’s objects into a single view, providing actionable data, and recommendations with a single click.
The Cynet dashboard provides users with a simple, navigable interface that is easily understandable.
Together with this comprehensive approach to detection, Cynet claims to have a low false-positive ratio, due to its use of cross correlation across multiple layers.
Response
Hosts, users, files and networks all are covered by Cynet’s advanced response capabilities. This includes:
- Isolation or blocking of traffic.
- Shutting down processes or restarting hosts.
- Killing, deleting or quarantining malicious files.
- Disabling run commands and users.
Automated Response:
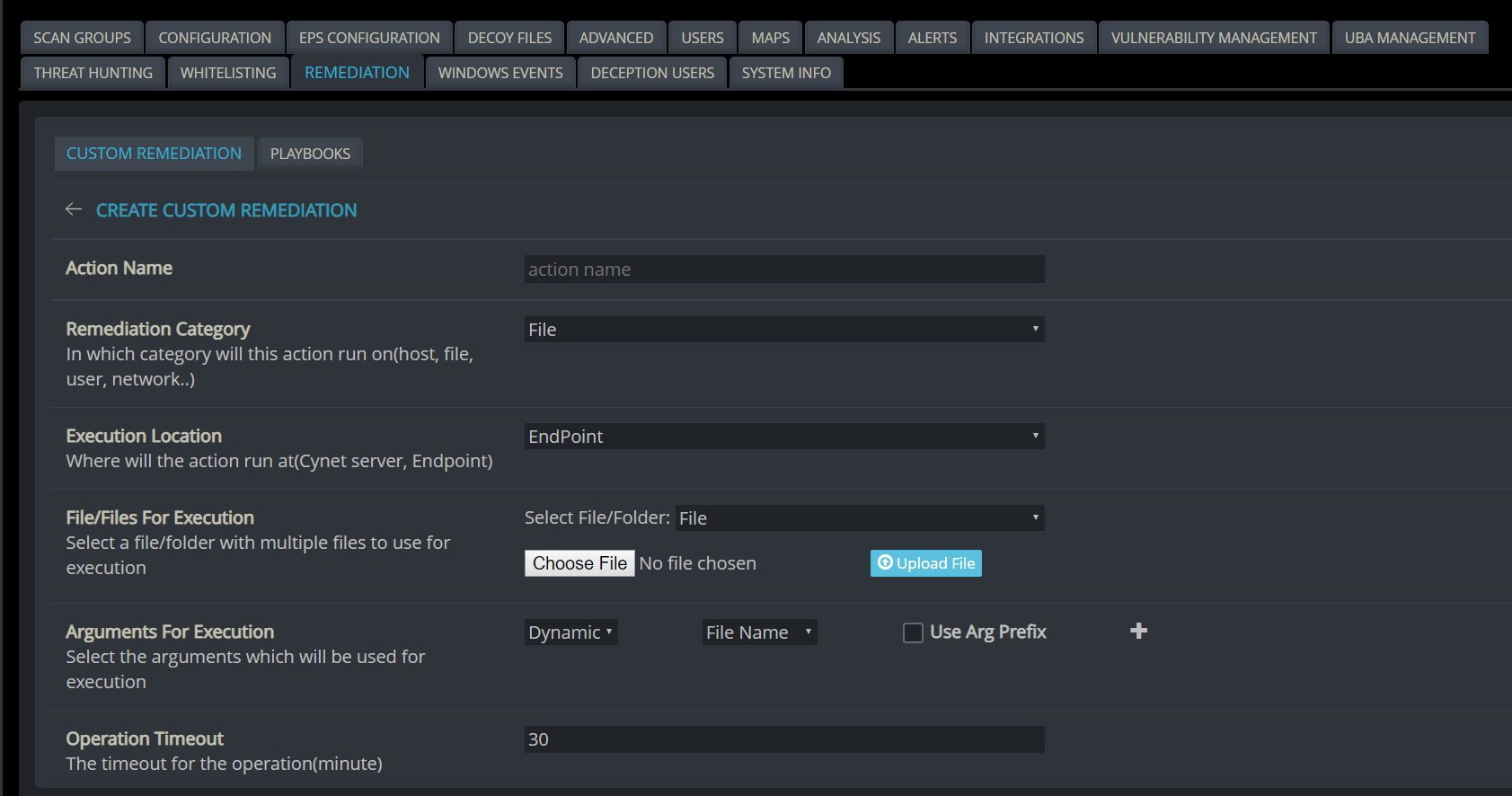
Users can create customized automated remediation rules for every alert received. This makes incident response easier, and aids in the prevention threats in real-time.
Cynet’s rule creation mechanism enables users to customize actions according to their organization’s specific needs, for example, applying the rule to certain groups while excluding others.
Custom remediations, including chained remediation actions, can be created by the user, as well as uploaded scripts which can interface with firewall, DC, etc. for a broader response operation.
24/7 Online Security Team – Cynet CyOps CyOps is Cynet’s fast response, 24/7 security operations team. It is part of the Cynet platform and comes with no added price. For organizations that are resource-strapped, the CyOps team can easily complement their own security IT team.
The CyOps team is online all the time, providing threat hunting, reviewing alerts, and available when needed, with someone calling the customer in the event of high-risk alerts.
- Threat hunting: Cynet’s own customer ecosystem intelligence is used to uncover advanced threats across users, endpoints, files, and networks.
- Malware analysis: CyOps engineers review malware samples, identifying complete attack chain, origin and potential risk. Potential threat actors and targets are thus quickly identified.
- Forensics: CyOps security experts perform post mortems in cases of breach.
Part of a growing niche
As the world of security moves from point solutions to comprehensive detection and response, the Cynet platform has staked a claim to this growing niche. For organizations which are constrained in resources and manpower, it provides a full-scale, easily manageable solution with broad security capabilities. Rapid deployment, a full-view dashboard and multiple technologies are all wrapped in one.
But it is always better to try for yourself – for small organizations with up to 300 endpoints, Cynet currently offers a free 14-day trial .
If your organization is over 300 endpoints, you can contact Cynet to request a one-on-one demo .