UPDATE
Cosmetics giant Yves Rocher is warning that a giant data leak exposed the personal data of millions of its customers and reams of sensitive internal company information to the public. The data exposure stems from a database left unprotected by a third-party consultant to the firm.
Researchers with vpnMentor on Monday said that they discovered an unprotected Elasticsearch server owned by Aliznet, which provides consulting services to large firms including IBM, Salesforce, Sephora and Louboutin. The server contained data about international cosmetics and beauty brand Yves Rocher, which is one of Aliznet’s clients, as well as exposing full personal identifiable information of millions of Yves Rocher customers.
“The biggest impacts will be felt by Aliznet, its client Yves Rocher, and the retail company’s end customers,” researchers said in a security alert posted Monday. It added: “The Aliznet leak has wider-reaching consequences than the impact on individual customers. The data breach impacts Aliznet’s clients who placed their trust in the company to protect their sensitive information. One concern is that Aliznet may have other unsecured databases and applications that haven’t been discovered yet. That means other clients of Aliznet may be at risk.”
Neither Aliznet not Yves Rocher responded to a request for comment from Threatpost. A vpnMentor spokesperson told Threatpost that the database was secured shortly after the exposure was disclosed to Aliznet.
Researchers said they could view the personal data for 2.5 million Canadian customers of Yves Rocher through the unprotected database, including first and last names, phone numbers, email addresses, date of birth and zipcodes. In addition, researchers were able to view records of more than 6 million customer orders for Yves Rocher. Each order was linked to a unique customer ID; researchers were able to use the leaked personal data records to identify individuals who placed orders through their IDs.
“For each order, we were able to view the transaction amount, currency used, delivery date, and the location of the store where the order was placed,” said researchers. “The order records also included the full name of the employee who processed each order, along with their employee ID.”
The server also exposed internal information about Yves Rocher itself, including statistics describing store traffic, turnover, and order volumes; product descriptions and ingredients for over 40,000 retail products and product prices and relevant offer codes.
“These included PDF files containing previous Aliznet job postings and client success stories, Aliznet employee profile portraits, website media, and other promotional materials,” said researchers.
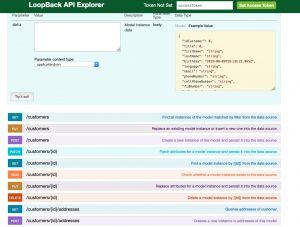
Finally, researchers were able to access the API interface for an application created by Aliznet for Yves Rocher. While the application appears to have been created to be used by Yves Rocher employees – rather than customers – alarmingly, it is linked to databases containing customers’ home addresses and purchase histories, researchers said.
“After examining the interface, our researchers believe that it would be possible for someone to easily log in to the system using an employee ID exposed in the Aliznet leak,” they said. “The unsecured Yves Rocher app could likely provide hackers and other malicious actors with additional information about the company and its customers.”
The API interface also gave researchers access to the API explorer, which they believe could be used to add, delete, or modify data in the company database. “With the proper credentials, a competitor or other malicious party could use this tool to tamper with data related to customers, products, stores, and more.”
Third-party data leaks, which exposure client and customer information such as in this incident, pose a constant threat for any company sharing data with partners, consultants or services companies. In April, hundreds of millions of Facebook records were found in two separate publicly-exposed app datasets; while in May, IT services provider HCL Technologies inadvertently exposed passwords, sensitive project reports and other private data of thousands of customers. Meanwhile three publicly-accessible cloud storage buckets from a data management company in June leaked more than a terabyte of data from its top Fortune 100 customers.
Researchers warned that this leaked database “could be harmful on multiple different levels.” Not only could the personal data of millions have been accessed by a malicious actor, but competitors to Yves Rocher could have accessed the company’s internal traffic information – giving them crucial data for launching campaigns.
“The exposed database also provides competitors with a list of Yves Rocher’s Canadian customers, complete with their name, age, contact information, and order histories,” researchers said. “Competing cosmetic and beauty companies could use this information to create highly effective advertising campaigns targeted at Yves Rocher customers. This could lead to Yves Rocher losing customers to competitors.”
This story was updated on Sept. 4 at 8am ET with an update on the status of the unprotected database.