A weakness discovered in Jaff ransomware by researchers has led to the creation of decryption keys to unlock files locked by the malware.
“We have found a vulnerability in Jaff’s code for all the variants to date. Thanks to this, it is now possible to recover users’ files (encrypted with the .jaff, .wlu, or .sVn extensions) for free,” Kaspersky Lab said in a prepared statement announcing the availability of the decryption keys.
Jaff was only first identified last month. At the time it was being distributed by Necurs botnet – the same botnet behind the Locky and Dridex campaigns. Attacks have included massive spam campaigns that include PDF attachments with an embedded Microsoft Word document functioning as the initial downloader for the ransomware.
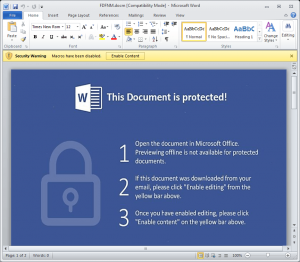 According to researchers, if recipients downloaded and enabled a Word macro associated with the .PDF the ransomware was downloaded. Actors behind the malware then demanded a ransom of between 0.5 to 2 Bitcoin (approximately $1,500 – $5,000, based on current exchange rates).
According to researchers, if recipients downloaded and enabled a Word macro associated with the .PDF the ransomware was downloaded. Actors behind the malware then demanded a ransom of between 0.5 to 2 Bitcoin (approximately $1,500 – $5,000, based on current exchange rates).
Earlier this month, the ransomware made news when researchers found a strain of the malware’s C2 shared backend infrastructure with a black market bazaar selling stolen bank and credit card account information.
Top countries impacted by the malware include China, India, Russia, Egypt, and Germany, according to Kaspersky Lab.
The free decryption tool for unlocking files has been added to the RakhniDecryptor (version 1.21.2.1).
Kaspersky Lab has previously released more than a dozen decryption keys for ransomware variants of CoinVault, TeslaCrypt, Wildfire and Crybola. A full list of available decryption utilities can be found at Kaspersky Lab’s No Ransom Project website.










