A function of the Android storage mechanism opens up an attack surface that affects all Android devices, and allows an attacker to corrupt data, steal sensitive information or even take control of a mobile phone.
Simply put, the issue – dubbed “man in the disk” – allows a bad actor to hijack the communications between privileged apps and the device disk, bypassing sandbox protections to gain access to app functions and potentially wreak havoc.
Android’s OS makes use of two types of storage – internal storage which provides every app with its own sandbox; and an external storage mechanism that uses a removable SD card. This latter storage is shared across the OS, because it’s designed to enable apps to transfer data from one app to another. So, if a user takes a picture and then wants to send it to someone using a messaging app, the external storage is the platform that allows this to happen.
“These are temporary files written to external storage, and they enable many legitimate uses of data propagation across apps,” said Check Point’s Orli Gan, head of threat prevention product management, in an interview with Threatpost at DEF CON 2018.
The issue, according to Check Point research that it presented at the hacking conference on Sunday, is that there are no built-in protections against malicious data sharing; rather, Google provides developer guidelines meant to provide a road map for security best practices. These include advice such as never writing critical data files to the external storage, and not using it to store executables or files that impact the way apps operate. Also, external storage files should be signed and cryptographically verified prior to dynamic loading, Google advises.
“However, as we know, developers do not always follow guidelines,” Gan said. “They may have their own agendas, or they’re lazy, or ignorant to security, or they just haven’t bothered reading them. We started looking at that and sampling a small set of apps, and saw that not complying with guidelines is a common thing.”
In fact, roughly half of the Android apps in Google Play that Check Point examined did not comply with the guidelines. The firm examined Google Translate (see video embedded, below), Yandex Translate, Google Voice Typing, Google Text-to-Speech and Xiaomi Browser, among others.
“Some of the apps in question are made by Google themselves,” said Gan. “So even Google’s own developers don’t necessarily follow Android guidelines.”
This lack of diligence opens up the data that an application writes to the external storage to interlopers.
“Apps monitor what’s being written to the shared external storage component – and an attacker can use this fact to ultimately replace that data to cause any number of results,” Gan explained. “The way an attacker uses this is that he would convince a user to download a conceivably naïve app – a flashlight, a game, something trivial. Once that app is installed, then the attacker has a way to continuously monitor that external storage – because all Android apps have visibility to it. He can see when apps are writing to to that storage – and can simply replace its data with his own data.”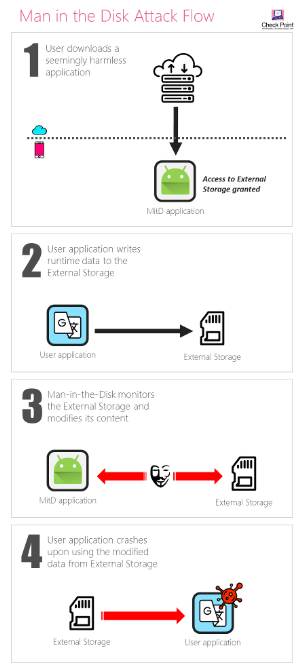
This can be abused to install another app in the background without the user’s knowledge; and further, whatever privileges the attacked app has, the bad code can gain access to all of those privileges for its own purposes.
“If you have an improperly developed app with high privileges, such as one that allows access to the camera, microphone, contact list etc., the malicious app can inject code running in context of app to make use of those,” Gan explained.
For instance, in the case of Google Translate, Yandex Translate and Google Voice Typing, Check Point found that the developers failed to validate the integrity of data read from the external storage. As such, the team was able to compromise certain files required by these apps, resulting in the crash of each of them – which in turn opened the door to code injection.
Check Point approached the developers of the vulnerable applications, and Gan said that “most, not all” chose to fix it – Google was in the former camp, although it was not as responsive on the built-in protection front; Gan said that its Android team told Check Point that the responsibility lies with developers to be secure when they create applications.
This lack of tackling built-in protections is problematic, she said.
“Two decades ago, you just needed a buffer overflow to inject code into Windows – it was simple to craft malware to run in the context of the OS. One could always argue that the developer didn’t follow the guidelines and introduce the right checks and balances, but the security landscape didn’t improve until MSFT and Intel introduced built-in protections. There are millions of developers and it’s unrealistic to expect them to all put security first. Solving the problem of this attack surface is not going to happen without the help of the OS-maker.”
Here’s the demo video for Google Translate:










