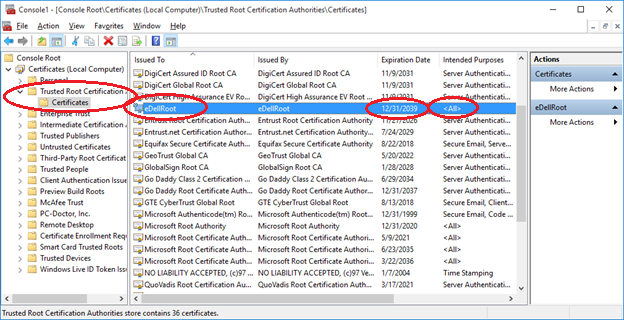
Update Just in time for Black Friday, various models of new Dell computers are shipping with a preinstalled root certificate and private key that corresponds to the cert, which as of earlier today was being accepted by all major browsers except Firefox.
Given that a number of tools exist to aid in the extracting of the private key, it doesn’t figure to be long before attackers can carry out man-in-the-middle attacks, spoof popular websites and unlock encrypted communication.
A request made to Dell for comment was not returned in time for publication. Dell said it began loading the cert on consumer and commercial devices in August to speed up online support engagements; the cert provides a support technician necessary system information including the PC model, drivers, and operating system.
“The recent situation raised is related to an on-the-box support certificate intended to provide a better, faster and easier customer support experience. Unfortunately, the certificate introduced an unintended security vulnerability,” Dell said in a statement provided to Threatpost. “To address this, we are providing our customers with instructions to permanently remove the certificate from their systems via direct email, on our support site and Technical Support. We are also removing the certificate from all Dell systems moving forward.”
Dell also said that commercial customers who image their own systems are not vulnerable.
“Dell does not pre-install any adware or malware,” Dell said. “The certificate will not reinstall itself once it is properly removed using the recommended Dell process.”
The situation of course harkens back to the Superfish ordeal that plagued Lenovo computers starting last Christmas season before it was finally made public in February. Superfish was bloatware on new Lenovo machines used to install ads in users’ browsers, that also opened the door to abuse leading to man-in-the-middle attacks similar to the Dell situation.
So far, the cert—called eDellroot—has been found on Dell XPS 15 laptops, M4800 workstations, and Inspiron desktops and laptops.
“It means attackers are de facto certificate authorities, free to generate man-in-the-middle certs, or just direct phishing sites that won’t get flagged as illegitimate,” said researcher Kenneth White, director of the Open Crypto Audit Project. “For these users, it’s as if there’s a bogus equivalent to Verisign, Comodo, or Symantec CA.”
White has built a website that checks whether machines are vulnerable to the cert. German security blogger Hanno Bock has also built a similar online check.
https://twitter.com/kennwhite/status/668833659915382786
The situation became public over the weekend, in particular on a Reddit thread started by Dell XPS 15 owner Kevin Hicks where it quickly became apparent that this wasn’t an isolated case of one rogue cert.
From the Reddit thread:
Surely Dell had to have seen what kind of bad press Lenovo got when people discovered what Superfish was up to. Yet, they decided to do the same thing but worse. This isn’t even a third-party application that placed it there; it’s from Dell’s very own bloatware. To add insult to injury, it’s not even apparent what purpose the certificate serves. At least with Superfish we knew that their rogue root CA was needed to inject ads into your web pages; the reason Dell’s is there is unclear.
Joe Nord, a Florida-based computer programmer, also posted a warning on his personal website about a new Dell Inspiron 5000 notebook he purchased last month.
“Serial number starts with ‘6b c5 7b 95 18 93 aa 97 4b 62’ and the keys are marked non-exportable. Notice that this doesn’t mean that the private key isn’t accessible, it only means that it isn’t exportable,” Nord wrote. “Anyone possessing the private key which is on my computer is capable of minting certificates for any site, for any purpose and the computer will programmatically and falsely conclude the issued certificate to be valid.”
Bock said the cert is installed by Dell Foundation Services software, which is available on Dell’s website.
“Every attacker can use this root certificate to create valid certificates for arbitrary web pages. Even HTTP Public Key Pinning (HPKP) does not protect against such attacks, because browser vendors allow locally installed certificates to override the key pinning protection,” Bock wrote. “This is a compromise in the implementation that allows the operation of so-called TLS interception proxies.”
This article was updated on Nov. 23 with comments from Dell.