The Apache Software Foundation has patched a denial of service vulnerability in the XML parser of the Apache CXF Web services framework.
Researchers, Andreas Falkenberg from Sec Consult Vulnerability Labs, and Christian Mainka, Juraj Somorovsky, and Joerg Schwenk from Ruhr-University Bochum, determined that they could initiate a denial of service condition in all versions of Apache CXF prior to versions 2.5.10, 2.6.7 and 2.7.4. Apache and Sec Consult are urging that users running these vulnerable versions should upgrade their systems to the most up-to-date build as soon as possible.
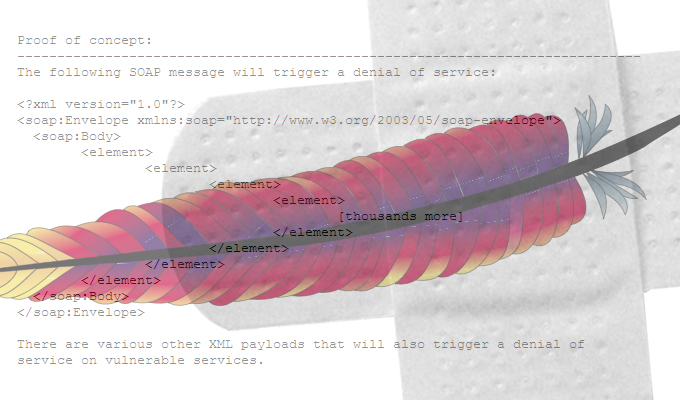
The flaw existed because the streaming XML parser failed to enforce limit restrictions on the number of elements and attributes and the nested structure of the documents it received in addition to other features. If properly exploited, the effect of such an attack can cause high CPU usage, and cause the Java Virtual Machine to run out of memory.
Researchers reported the vulnerability to Apache in late February. Apache acknowledged the report immediately, confirmed the vulnerability in April, patched it in May, and disclosed it in June. SEC Consult Vulnerability Lab published an advisory detailing the bug on the Full Disclosure mailing list this morning.