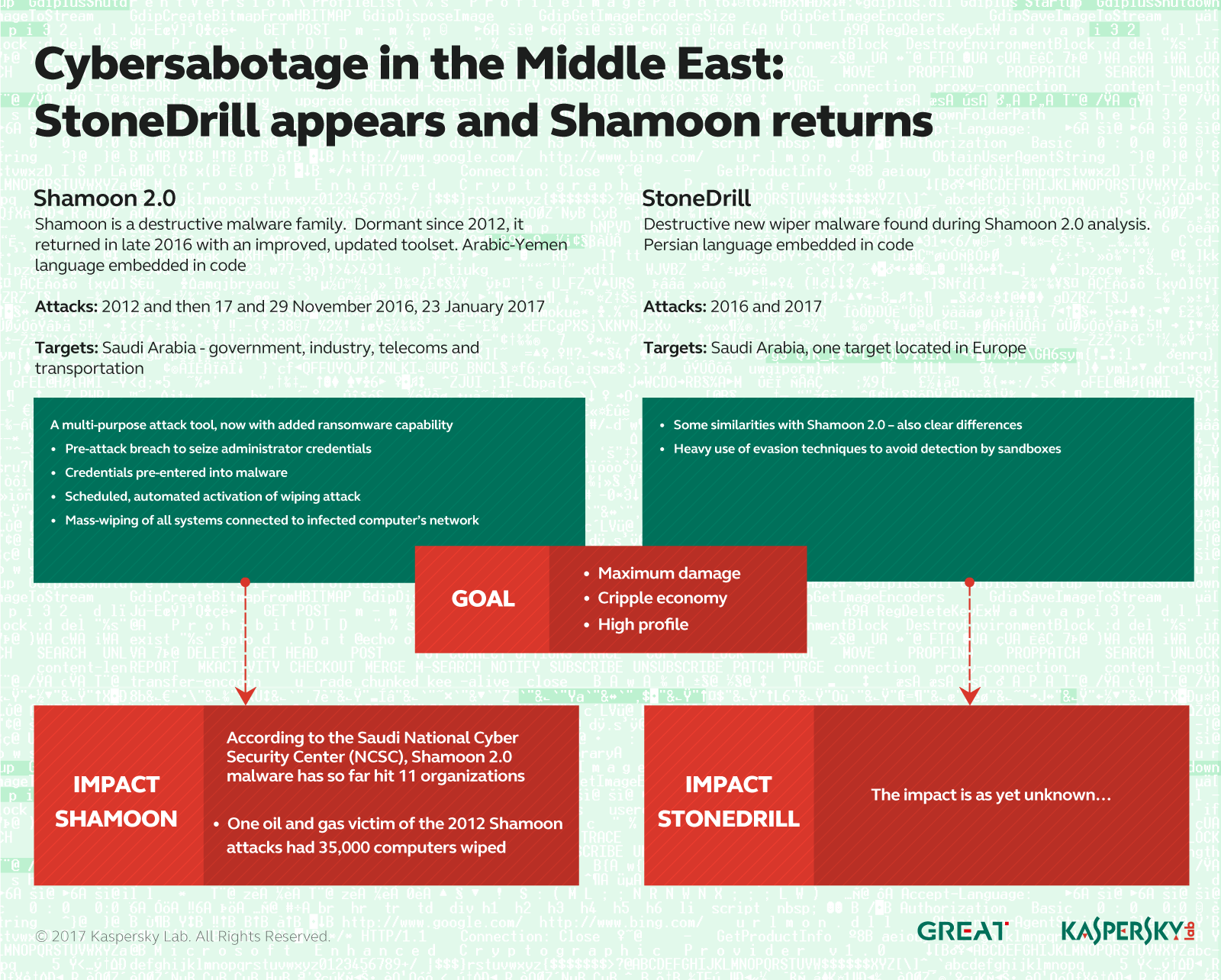
There have been a handful of wiper malware attacks in the wild in the last decade with Shamoon’s destruction of more than 35,000 workstations at Saudi Aramco in 2012 and the Dark Seoul attacks on Sony Pictures Entertainment the most high profile.
However, since last fall, Shamoon has resurfaced with a variant again mostly targeting organizations in Saudi Arabia. It also includes a newly discovered ransomware component in addition to its wiping functionality that has already been seen in two attacks in November and another in January.
Researchers at Kaspersky Lab released new information today about another piece of wiper malware found in the wild called StoneDrill that also targets organizations in Saudi Arabia, and was also found inside a European petro-chemical organization, harkening to a potential expansion of these types of attacks outside the Middle East.
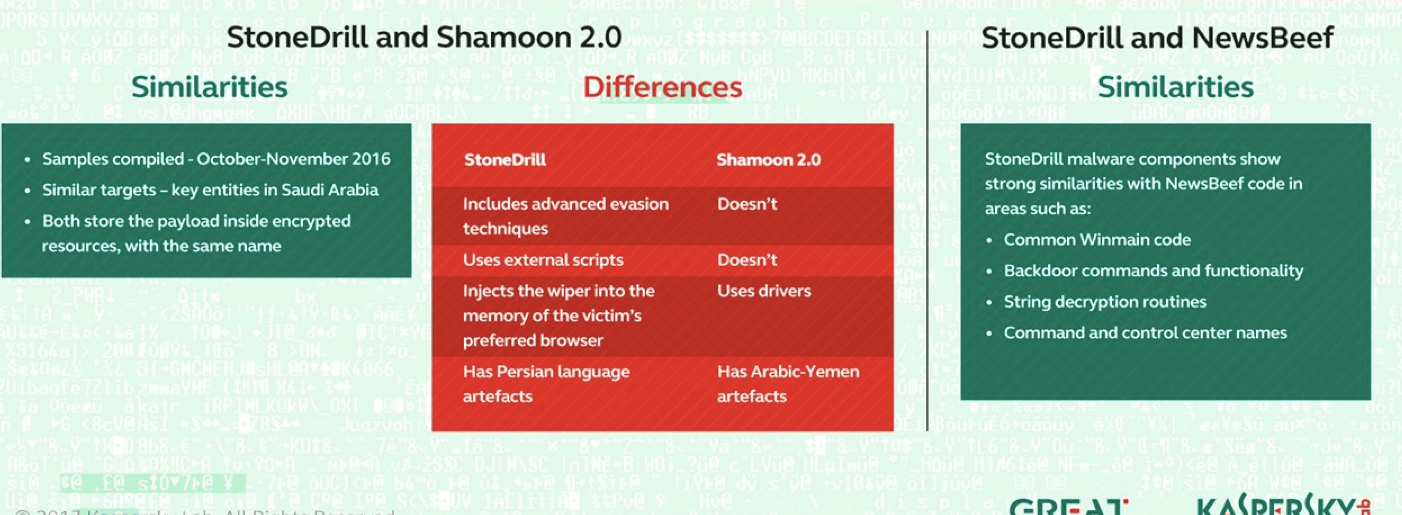
StoneDrill also bears similarities to an APT group known as NewsBeef, or Charming Kitten, for its use of the Browser Exploitation Framework known as BEeF. The similarities are numerous and include familiar WinMain and OS signatures, update commands, and command-and-control server names. It’s unknown whether the groups behind Shamoon and StoneDrill are the same, or are simply aligned in interests and regions in which they target.
“Wipers in cyberespionage attacks rarely come around,” Kaspersky Lab researcher Juan Guerrero-Saade said. “Sabotage is rare and runs counter to what you’d expect an APT actor to be interested in.”
APT actors covet stealthy access and persistence inside a network in order to maintain visibility over a target, steal data or load more malware and exploits onto compromised machines, Guerrero-Saade said, adding that the wiper functionality attached to StoneDrill has not been used in the wild yet.
“The wiper component is in place in StoneDrill, we just have not seen it leveraged adequately,” Guerrero-Saade said. “Speaking to the rarity of sabotage operations, there have probably been less than 10 in the last decade, which suggests how careful they are with using them.”
StoneDrill was discovered during Kaspersky Lab’s investigation into Shamoon 2. As a number of Yara rules written to catch behaviors associated with Shamoon around its use of Windows API functions to enumerate files it wants to wipe, also triggered with this new malware.
StoneDrill is similar stylistically to Shamoon, but has been developed to include enhanced evasion techniques and a new means of injecting the wiper malware directly into the victim’s preferred browser rather than through the user of drivers as the original Shamoon did.
“The idea is that in this way, attackers can bypass security software by doing wiping operations through a trusted process,” Guerrero-Saade said.
Depending on the configuration, StoneDrill is capable of wiping data by overwriting physical and logical drives with random data and then deleting folders in the logical drives.
“What we’re starting to understand is that given the code similarities between StoneDrill and NewsBeef, the connection between them is well cemented and interesting,” Guerrero-Saade said. Some of those similarities include the update commands, decryption routines, Winmain and OSU signatures and similar naming conventions around command and control servers (serveic[.]com v. service[.]com, for example).
Shamoon 2, meanwhile, also contains extensive spying capabilities starting with a still-unknown attack used to steal administrator credentials to facilitate lateral movement; these attacks don’t rely on exploits targeting known or unknown vulnerabilities, Guerrero-Saade said. The stolen credentials are then hardcoded into Shamoon 2 and allows the attackers to compromise one machine and then use the stolen credentials to embed themselves elsewhere in the network. Shamoon has been used against 11 organizations in Saudi Arabia, the Saudi National Cyber Security Center says.
The ransomware component of Shamoon 2 has yet to be used in the wild, Guerrero-Saade said. It’s unknown how the attackers would leverage this part of the platform to hold their victims hostage for financial or idealistic gain.
Kaspersky Lab said that Shamoon is designed to run either as a wiper or encryptor; a weak RC4 key is generated on the machine that is encrypted by an RSA public key and stored on the local hard drive.