Microsoft is warning of malware, Dexphot, that has infected more than 80,000 machines, sucking up their CPU power in order to mine cryptocurrency.
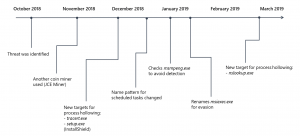
Researchers first discovered Dexphot in October 2018 and saw its activity peak during July. They said that the malware has a complex attack chain and also uses various methods to outwit detection efforts, including an obfuscated script designed to check for antivirus products, and regularly-scheduled malware updates.
“Its goal is a very common one in cybercriminal circles — to install a coin miner that silently steals computer resources and generates revenue for the attackers — yet Dexphot exemplifies the level of complexity and rate of evolution of even everyday threats, intent on evading protections and motivated to fly under the radar for the prospect of profit,” said Hazel Kim of the Microsoft Defender ATP Research Team, in a Tuesday post.
Researchers did not say how Dexphot is initially spread; Threatpost has reached out for further comment. During the initial execution stage, Dexphot first writes five key files to the disk. With the exception of one of the files – an installer with two URLs – most of these files are legitimate processes, making detection of the malware difficult.
These legitimate system processes include msiexec.exe (for installing MSI packages later in the process), rundll32.exe (for loading a loader DLL, which later downloads a password-protected ZIP archive), unzip.exe (for extracting files from the password-protected ZIP archive), schtasks.exe (for scheduled tasks), powershell.exe (for forced updates). 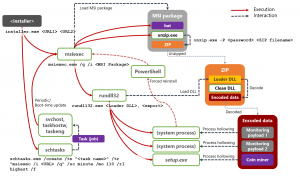
Meanwhile, the lone non-legitimate file (SoftwareBundler:Win32/ICLoader) is primarily used to run the Dexphot installer.
Once running, the installer then uses two URLs to download malicious payloads. Dexphot also uses these two URLs later to establish persistence, update the malware and re-infect the device.
Then, “the installer downloads an MSI package from one of the two URLs, and then launches msiexec.exe to perform a silent install,” researchers said. “Dexphot’s package often contains an obfuscated batch script. If the package contains this file, the script is the first thing that msiexec.exe runs when it begins the installation process.”
The malware’s attack chain ends by launching a cryptocurrency miner on compromised systems, which then depletes system resources in order to mine for cryptocurrency. The malware switches up miners and either deploys XMRig and JCE Miner.
Evasion Detection
Researchers say that Dexphot uses a variety of sophisticated methods to evade security solutions, including using layers of obfuscation, encryption and randomized file names to hide its installation process.
The installed MSI package (described above) also contains an obfuscated script is designed to check for antivirus products – including Windows Defender Antivirus, Avast and AVG – and halts the malware infection process immediately if an antivirus product is found running.
And, if not stopped, Dexphot ultimately runs as a cryptocurrency miner on the device with monitoring services and scheduled tasks triggering re-infection when attempts are made to remove the malware, they said.
“Two monitoring services simultaneously check the status of all three malicious processes,” said researchers. “Having dual monitoring services provides redundancy in case one of the monitoring processes is halted. If any of the processes are terminated, the monitors immediately identify the situation, terminate all remaining malicious processes and re-infect the device.”
Finally, the malware uses process hollowing (a prevalent technique used by cybercriminals to hide malware within a legitimate system process by replacing the contents of that process with malicious code) to load executables onto infected systems.
“This method has the additional benefit of being fileless: the code can be run without actually being saved on the file system,” researchers said. “Not only is it harder to detect the malicious code while it’s running, it’s harder to find useful forensics after the process has stopped.”
Researchers say that the malware peaked during July with more than 80,000 infections. Since then, malicious behavior reports have dropped to a low hum. “Dexphot is not the type of attack that generates mainstream media attention; it’s one of the countless malware campaigns that are active at any given time,” said researchers.
Is MFA enough to protect modern enterprises in the peak era of data breaches? How can you truly secure consumer accounts? Prevent account takeover? Find out: Catch our free, on-demand Threatpost webinar, “Trends in Fortune 1000 Breach Exposure” to hear advice from breach expert Chip Witt of SpyCloud. Click here to register.