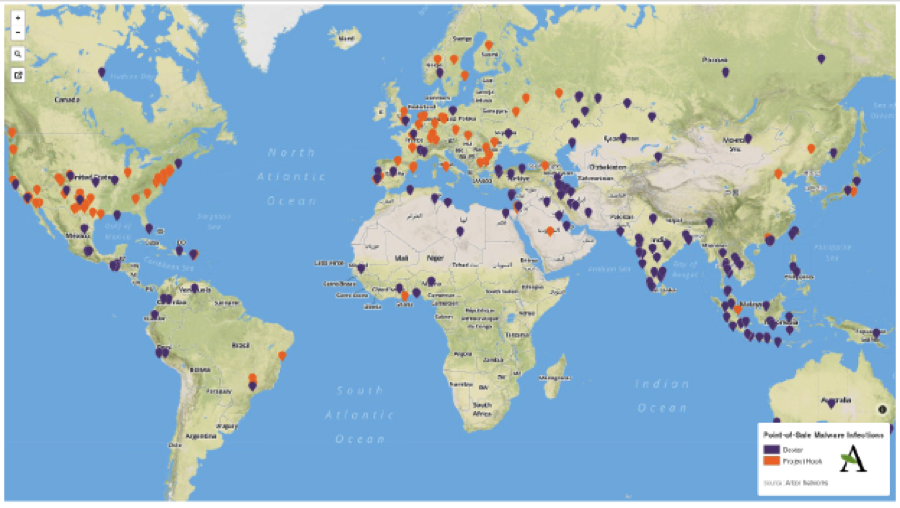
While the Target data breach may be in the rear view mirror, research this week shows it’s clear that many attackers are still using point of sale malware, namely Dexter and Project Hook, in active attacks.
Researchers at Arbor Networks’ Security Engineering & Response Team (ASERT) looked at several such campaigns, exfiltrated data dumps and decoded them to analyze the scope of their compromises. The group also analyzed network activity triggered by Dexter malware samples.
According to Arbor’s Threat Intelligence Brief 2014-3 released yesterday, researchers noticed a specific variation of Dexter, Dexter Revelation, exfiltrating stolen data, stored in fake .zip files and .txt files – via FTP credentials – from compromised terminals.
Revelation was one of three Dexter variants (along with Stardust and Millennium) that ASERT noticed in December but at that time it was unclear just how the infections were happening.
While researchers were under the assumption that Revelation was a fairly new brand of malware, new research has traced developmental versions of the malware back almost a year, early builds date back to April 2013.
It turns out the Revelation malware has several handy functions it uses including using a memory scraping procedure that “scours system memory looking for plaintext data that matches a credit or debit card format” and a keylogger function it uses to “capture keyboard activity and other system information.” The fake .zip files store a four-byte XOR key that can actually be used to decode the file’s contents.
The report suspects a threat actor going by either “Rome0” or “rome0” is directly involved with Dexter. Researchers say they’ve noticed actors going by both of the usernames demonstrating their familiarity with banking Trojans online and frequenting various carding forums.
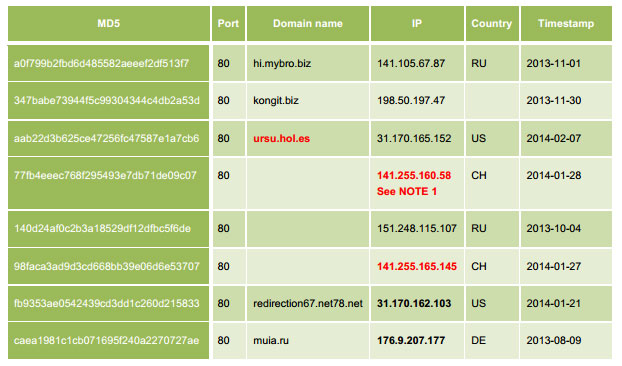
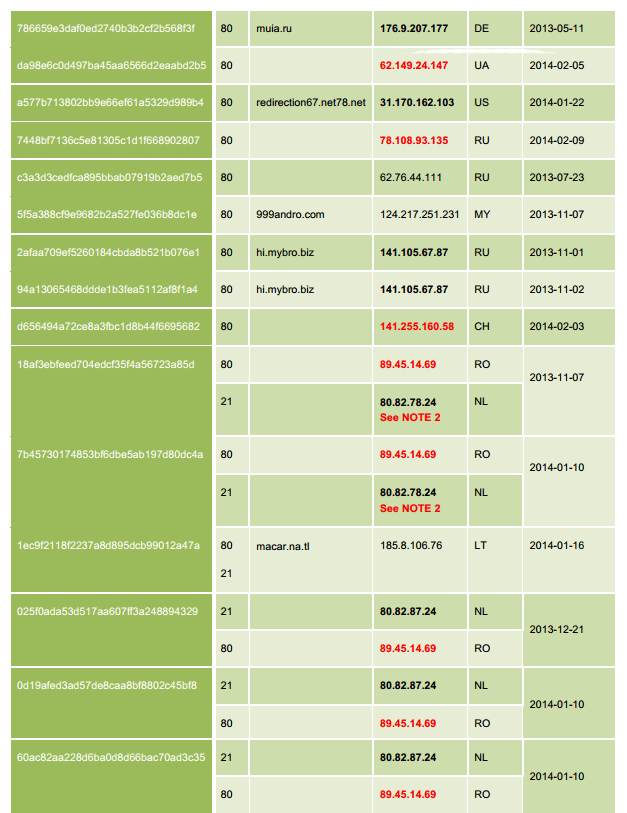
ASERT posted a list of IP addresses and hostnames associated with Dexter’s command and control activity in the report that it’s hoping organizations review.
“Organizations are encouraged to check logs and other indicators of network activity associated with these IP addresses and/or hostnames to find systems compromised as part of a past or current attack campaign.”
The IP addresses listed in red indicate that the C&C servers associated with them were still active as of the report.
While Project Hook, another point-of-sale malware, is less active than Dexter, researchers are still encouraging organizations to remain vigilant especially after they found a special URL set up hosting back-end panels for Project Hook and another PoS malware: Alina, in January and early February.
 Arbor’s report came out the same day that Target announced it would finally overhaul its information security processes and that it’s chief information officer, Beth Jacob, had resigned.
Arbor’s report came out the same day that Target announced it would finally overhaul its information security processes and that it’s chief information officer, Beth Jacob, had resigned.
Target reports that it will fill the position with an external hire as well as assign a new role: chief compliance officer.
“Target will be conducting an external search for an interim CIO who can help guide Target through this transformation,” Target’s Chairman, President, and CEO Gregg Steinhafel said Wednesday.
The transformation Steinhafel is referring to is the stress the U.S. retailer has undoubtedly had to grapple with after suffering a massive breach in November. Attackers were able to set up a command and control server and lift more than 40 million credit and debit card records and 70 million other records of customer details from Target point of sale systems.
We may be three months removed from the Target fiasco but point-of-sale malware campaigns continue to permeate the headlines.
Texas-based Sally Beauty Supply, a chain with around 2,700 locations nationwide, confirmed yesterday that someone attempted to breach its system but would not confirm that customer data was at risk. According to Krebs on Security a batch of 282,000 stolen credit card numbers popped up on an underground market and three banks purchased their of their customers cards in hopes of finding the theft’s origin. All of the banks then found that the cards they had gotten hold of had all been used at a Sally Beauty Supply store within 10 days before.