Many Android device manufacturers are not telling the truth when they say they have patched phone vulnerabilities in new updates, researchers found.
Karsten Nohl and Jakob Lell, researchers with Security Research Labs, told Threatpost they have tested the firmware on close to 3,000 phones and found that the devices are missing several patches – even after manufacturers said they were already patched.
“Our large study of Android phones finds that most Android vendors regularly forget to include some patches, leaving parts of the ecosystem exposed to the underlying risks,” the researchers wrote in a recent report.
The researchers tested samples of phones patched from October 2017 onward from 23 vendors, including known vendors such as Samsung and Motorola, and Chinese-owned ZTE and TCL.
W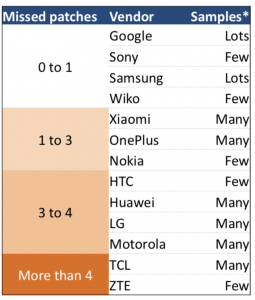 hile these vendors said that they had regularly issued patches, the researchers found that in several cases patches were not installed on devices.
hile these vendors said that they had regularly issued patches, the researchers found that in several cases patches were not installed on devices.
For instance, researchers found that in Samsung’s 2016 J3 model, with the Android version 5.1.1, there were two critical patches and 10 high-rated patches missing.
Samsung did not respond to a request for comment before article publication.
Some vendors, such as Sony and Samsung, were missing an average of zero to one patch – while others, such as TCL and ZTE were missing an average that exceeded four patches.
Android has also had difficulties with patching in the past. According to a report by Duo Labs, three out of 10 Android devices hadn’t applied a security patch that has been released since the start of 2016, leaving them susceptible to exploits for critical vulnerabilities.
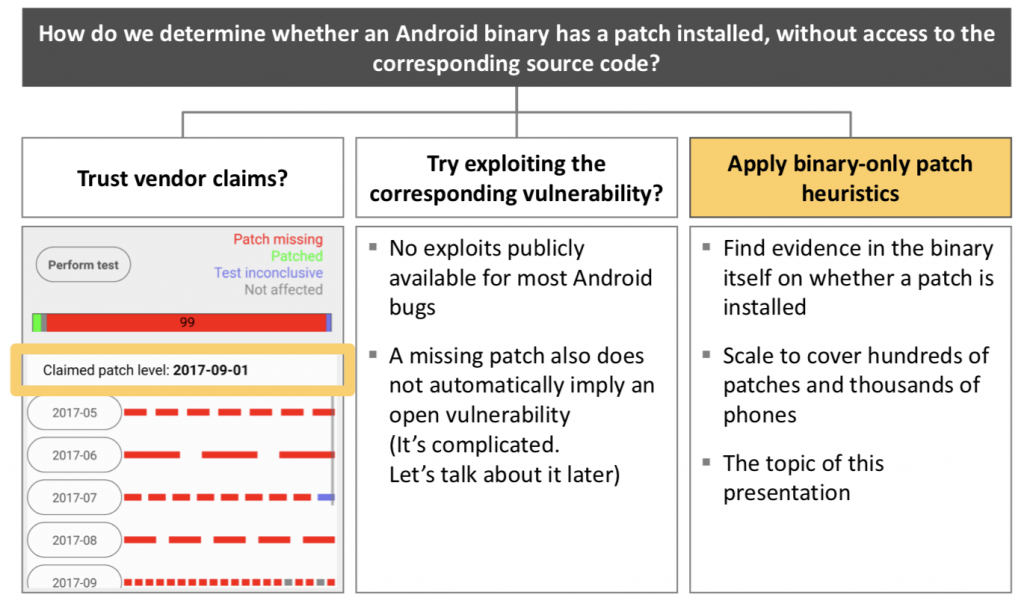
Nohl and Lell were able to determine whether an Android binary had a patch installed without access to the corresponding source code by applying binary only patch heuristics.
This meant that they looked for evidence in the binary itself to determine whether a patch was installed.
Nohl told Threatpost that the Android ecosystem’s complexity makes it more difficult for vendors to issue and follow up on patches.
“The Android ecosystem is very complex, with patches being handled by multiple companies and for thousand of different phone models before they reach the consumers,” Nohl said. “Simplification of the ecosystem, for example by moving more phones to recent versions of Android and by creating fewer network-specific phone versions, would certainly help in making patching easier.”
Some of the patch gap is likely due to the chipset vendors forgetting to include them as well, said the researchers.
“We would like to thank Karsten Nohl and Jakob [Lell] for their continued efforts to reinforce the security of the Android ecosystem,” A Google spokesperson told Threatpost. “We’re working with them to improve their detection mechanisms to account for situations where a device uses an alternate security update instead of the Google suggested security update.”
The spokesperson said that Android devices have several layers of of security including updates that act as protection for end users.
“Built-in platform protections, such as application sandboxing, and security services, such as Google Play Protect, are just as important. These layers of security—combined with the tremendous diversity of the Android ecosystem—contribute to the researchers’ conclusions that remote exploitation of Android devices remains challenging,” said the spokesperson.
Nohl and Lell agreed that exploiting Android was difficult due to the operating system’s security barriers, such as sandboxing and ASLR – and helped tamp down criminal hacking activity over the last year.
“The criminal ecosystem seems to understand the challenges in hacking Android phones. Instead criminals focus on using social engineering tricks to prompt users into installing malicious apps, often from insecure sources, and then granting excessive permissions to these apps,” according to the report.
That said, the risk still exists, and making sure that known bugs are patched reliably can stop more sophisticated hackers – such as state-sponsored attackers.
The researchers said that end users can use an Android app, called SnoopSnitch, to verify vendor claims about whether devices have been patched and measures the patching level of their phones.
“As Android is ever increasing in popularity, the hacking incentives will only keep growing, as does the ecosystem’s responsibility for keeping its users secure … Patching is critically important to uphold the effectiveness of the different security layers already found in Android,” according to the report.