As a security professional, it is critical that you assess the performance of your security team and keep in-the-know regarding your current security posture, in addition to planning ahead. ‘The Ultimate 2019 Security Team Assessment Template‘ is a first-of-its-kind tool that encapsulates all the major KPIs of the organizational security team’s main pillars, created to make the job of the CIO / CISO easier by saving them time and effort of having to create such a tool from scratch. The template helps measure the performance of security teams over 2019 while creating 2020 performance goals.
Because security teams vary in size and responsibility distribution from organization to organization, and because there is minimal if any consistency across the industry (for example, the responsibilities of the “security analyst” can vary greatly from place to place, the same can be said for architects, managers, and directors ) it is quite challenging to create a template along these lines.
These challenges and others are addressed head-on by ‘The Ultimate Security Team Assessment Template,’ which succeeds in doing so by focusing on functionality. This is done while keeping in mind the two main foundations of the security team: A – ensuring the organization has a sufficient deployment of security products; and B – utilizing these products to get the most prevention, detection, and response as possible.
The following are the roles and responsibilities covered in the template:
- Security Architect – designs, builds, tests and implements the security infrastructure in an IT network, with the mission of protecting business and consumer information. Those filling this role are expected to have a deep understanding of complex IT systems while staying updated on the latest standards, systems, protocols, and products in the security industry.
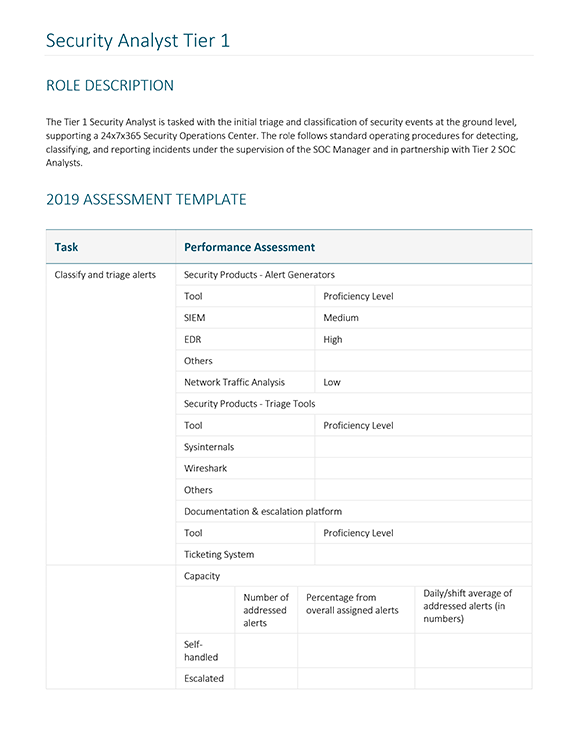
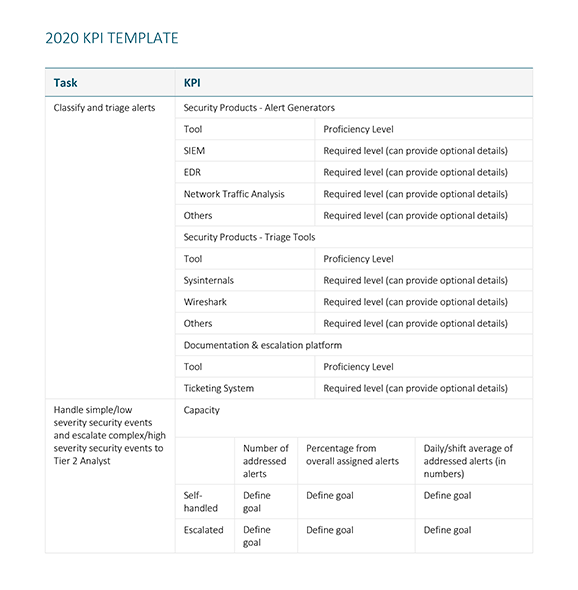
- Security Analyst Tier 1 – responsible for first triage and classification of security events as they happen, providing backup to the 24x7x365 SOC. Those fulfilling these responsibilities are expected to adhere to standard operating procedures in detection, classification, and reporting of incidents and events while being supervised by the SOC manager and working in unison with Tier 2 SOC analysts.
Security Analyst Tier 1 2019 Assessment Sample
Security Analyst Tier 1 2020 KPI Sample
- Security Analyst Tier 2 – conducts the technical side of response operation in the case of critical events that have been escalated by the tier 1 security analyst. Responsibilities include: containment and its management, investigation, management of remediation actions.
- Security Analyst Tier 3 – carries out continual monitoring of systems, looking for vulnerabilities and threats to its safety. Also responsible for carrying out threat hunting utilizing IOCs from threat intel feeds and providing the team with visibility into the organization’s security posture in real-time, by carrying out proactive penetration tests.
- SOC Manager – creates and manages workflows for security incident monitoring, and their management and response. Ensure compliance with SLA and help an organization achieve operational goals by process adherence and improvisation.
- Director of Security – responsible for all security related issues in the organization, including compliance frameworks; product buying, deployment and maintenance; and workflows for breach protection. Works under CIO and serves as an informational point for all cybersecurity issues within the organization.
As function is more important than title, many organizations have persons carrying out multiple designation responsibilities as seen in the template, i.e. both tier 1 and tier 2 analyst, or Security Architect and SOC Manager. In large-size organizations, for example, Security Architects might have a team under them responsible for network, endpoint and cloud security. There are many potential variations in how security responsibilities can be assigned within any organization. Even so, the foundation of security practice remains the same, which means that CISOS should easily be able to match the functionalities described in the template to their team’s specific structure.
The Security Team Assessment Template (download here) can be used as-is, or CISOs can customize to fit the structure and responsibilities of their organization. Again, this includes both reviewing the 2019 performance points of each team member, while serving as an ideal tool for tracking and monitoring security functions moving forward.
If you find the template a good fit as-is, great. If on the other hand, you find your organizational structure and responsibilities require personalization, you can cut and paste the different responsibilities/KPIs to meet the needs and structure of your team.
‘The Ultimate Security Team Assessment Template’ can be downloaded here.