Cynet launched in December 2019 the State of Breach Protection 2020 Survey. Based on the responses from 1,536 individuals, they now share the survey report that includes common practices, priorities, and preferences of security leaders as they strive to secure their organization from a breach (download the full survey report here).
One of the main challenges facing security executives is how to prepare and respond to threats they face in today’s continually changing landscape. They need to consider questions such as: Which attacks pose the greatest risk? What security products would best prepare them to face these threats; how to build a strong team of in-house security professionals, or alternatively, whether they are better off outsourcing the security operations, or finding a balance between the two? What level and kinds of automation can help them as part of their breach protection workflows? And more.
The State of Breach Protection 2020 survey also provides information such as:
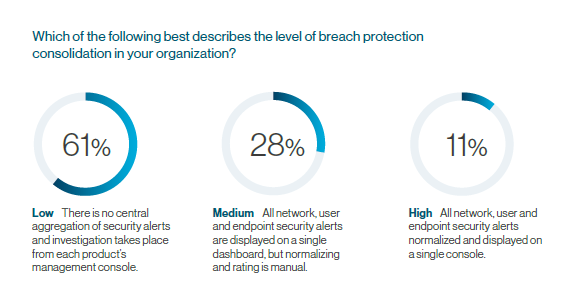
- Not consolidating gets in the way of achieving successful protection. According to the survey, organizations that deploy and utilize advanced security products find managing a multi-product security stack to be the biggest obstacle in achieving their goal protection level.
- The main focus of many organizations in 2020 is advanced protection projects. Most organizations that already deploy the basic AV, firewall, email security products, plan to add on EDR/EPP, Network traffic analysis or SIEM in the coming year.
- The Achilles heel of endpoint security is deployment. Just a small number of organizations say that they deploy EDR/EPP on over 85% of their endpoints without any launch or maintenance difficulties and issues. Since EDR/EPP is the main method used against attack, this is a concerning number.
- When it comes to advanced threat protection, a high number of alerts are unattended on a daily basis. Of the bodies deploying solutions such as SIEM, EDR/EPP, network traffic analysis, UEBA or deception, most say that over 25% percent of daily alerts are unattended.
- Automated remediation is still the poor brother of response orchestration. Only a small number of the responding organizations say that they utilize automation in their remediation workflows. Most do, however, orchestrate their IR operations from a centralized interface.
- Security outsourcing is a love-hate relationship for most organizations. With the security gap to deal with, organizations are forced to think of the out-source option, but the inclination is still to want to keep as much in-house as possible, especially when it comes to active attack remediation.
The wisdom of security professionals in one place – The State of Breach Protection 2020 survey – gives CISOs information they can use to make more educated, data-driven calls when it comes to their organizational security needs, providing a broad look at the trends and best practices of 2020’s advanced breach protection professionals.
Download The State of Breach Protection 2020 survey report here.