Dunkin’ Donuts may have just launched its first double-filled doughnut, but another doubling up is not quite as tasty. The chain has suffered its second credential-stuffing attack in three months.
Like the first incident, the attack targeted pastry aficionados that have DD Perks accounts, which is Dunkin’s loyalty program. Names, email addresses, 16-digit DD Perks account numbers and DD Perks QR codes were potentially exposed.
There’s a growing underground market for loyalty program data. Hackers can sell the account’s credentials, or offer direct access to the accounts to people that go on to use the stored value, coupons, points and so on contained in them for themselves. Other rewards-point abuse often revolves around the ability to set up scams offering “discounted goods” that were actually purchased using stolen points.
The company said that it believes the hacker obtained usernames and passwords from security breaches of other companies, and then used those usernames and passwords to try to break in to various online accounts via widespread automated login requests – a method known as credential stuffing.
This campaign started on or around January 10, the company said.
“Our security vendor was successful in stopping most of these attempts, but it is possible that these third-parties may have succeeded in logging in to your DD Perks account if you used your DD Perks username and password for accounts unrelated to Dunkin’,” the company said in a data-breach notification to the State of Vermont.
The company has forced a password reset that requires all of the potentially impacted DD Perks account holders to log out and log back in to their account using a new password, and is replacing any DD Perks stored-value cards with a new account number.
The Underground Credentials Scene
Malicious bots and botnet-as-a-service offerings are hackers’ primary tool for conducting credential-stuffing attacks, since they can be used to test massive lists of stolen credentials on any website with a login page in an automated fashion. That automation is helped along by a range of easily obtained tools on the criminal underground.
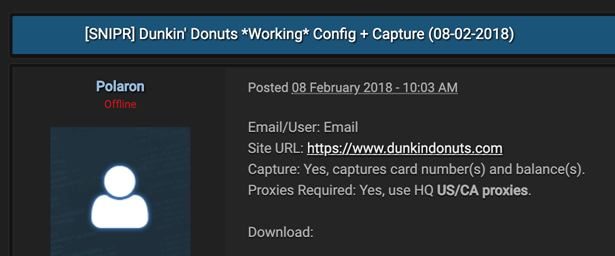
“Snipr is a tool that automates credential-stuffing attacks like the one on Dunkin Donuts,” Andy Norton, Lastline’s director of threat intelligence, told Threatpost. “You can see here from Feb. 8th someone has built a “Config,” which means emulated the login process for Dunkin’ Donuts, so that they can run credential lists at the site, looking for valid logins.
The attacks are also often fueled by big credential dumps on the Dark Web.
“Massive password breaches create huge spikes in bot traffic on the login screens of websites – in this case, the Dunkin’ Donuts site – as hackers cycle through enormous lists of stolen passwords,” said Distil co-founder Rami Essaid, via email. “While this is often framed as a problem for the individuals who own the passwords, any online business that has a user login web page is at risk of becoming the next breach headline.”
An analysis last year by the Distil Research Lab found that after the credentials from a data breach have been made publicly available, websites experience a 300 percent increase in volumetric attacks. In the days following a public breach, websites experience 3X more credential stuffing attacks than the average of two to three attacks per month.
Essaid added, “Password dumps create a ripple effect of organizations spending precious time and resources on damage control. The massive spike in failed logins, then the access into someone else’s account before the hacker changes the password, then the account lock-out for the real user, then the customer service calls to regain access to their account. All because a username and password was stolen from a different website.”
There are steps that companies can take to thwart these kinds of attacks.
“All organizations should implement two-factor authentication to protect their customers from these credential-stuffing attacks, and in order to save themselves from financial loss, reputation damage or customer churn,” Lastline’s Norton said.
Interested in learning more about data breach trends? Watch the free, on-demand Threatpost webinar, as editor Tom Spring examines the data breach epidemic with the help of noted breach hunter and cybersecurity expert Chris Vickery. Vickery shares how companies can identify their own insecure data, remediate against a data breach and offers tips on protecting data against future attacks.