The Turla APT campaign has baffled researchers for months as to how its victims are compromised. Peaking during the first two months of the year, Turla has targeted municipal governments, embassies, militaries and other high-value targets worldwide, with particular concentrations in the Middle East and Europe.
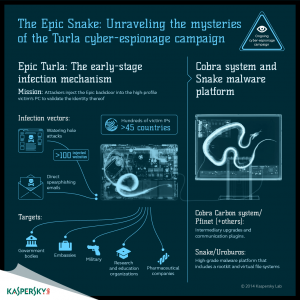
Researchers at Kaspersky Lab, however, today announced they have discovered a precursor to Turla called Epic that uses a cocktail of zero-days and off-the-shelf exploits against previously unknown and patched vulnerabilities to compromise victims. Epic is the first of a multistage attack that hits victims via spear-phishing campaigns, social engineering scams, or watering hole attacks against websites of interest to the victims.
Epic shares code snippets with Turla and similar encryption used to confound researchers, suggesting a link between the two campaigns; either the attackers are cooperating or are the same group, Kaspersky researchers said.
To date, there are more than 500 victim IP addresses in 45 countries, and as Tuesday the campaign remained active. The malware establishes a backdoor connection to the attackers through which system information is sent in order to determine which exploits are fed to the compromised machine and ultimately where stolen data is exfiltrated. The attackers have a variety of backdoors at their disposal, and use them according to the value of the target, Kaspersky researchers said.
Two zero-day exploits against Windows XP and Windows Server 2003 (CVE-2013-5065) vulnerabilities and Adobe Reader (CVE-2013-3346) have been used against some targets in order to gain administrative privileges. Users are infected via spearphishing emails with infected PDF exploits, or via infected websites hosting Java exploits that are really malware installers posing as a .scr file or Flash Player. Victims are tricked, in the last two cases, into installing the infected files, Kaspersky researchers said.
More than 100 websites have been infected in the Epic campaign, most of them municipal government websites, including the website for City Hall in Pinor, Spain, an entrepreneurial site in Romania and the Palestinian Authority Ministry of Foreign Affairs. All of the sites were built using the TYPO3 content management system, indicating the attackers have access to a vulnerability on that platform. Once compromised, the websites then load remote JavaScript that performs a number of tasks, including dropping exploits for flaws in Internet Explorer 6-8, recent Java or Flash bugs, or a phony Microsoft Security Essentials application signed with a legitimate certificate from Sysprint AG.
“The Epic Turla attackers are extremely dynamic in using exploits or different methods depending on what is available at the moment,” Kaspersky Lab said in its research report.
More than 50 hacked servers make up the Epic Turla command infrastructure, Kaspersky Lab said. Victimized computers communicate to a centralized server via a network of proxies and VPN connections. The attackers make a determination whether to exploit a particular machine based on a number of existing system and third-party application configurations. If certain processes, such as tcpdump, windump, ethereal, wireshark and others are running, the backdoor will terminate. Otherwise, if the victim is of interest, a different backdoor called Carbon or Pfinet, is deployed and the Epic campaign updates the configuration file with a new set of command and control servers, further indicating a connection between the Epic and Turla campaigns. Attack commands are sent that include a keylogger used to steal credentials in order to move laterally, as well as a list of specific .doc files to search for. Some of the document searches found are: “NATO.msg;” “eu energy dialogue;” and “EU.msg.”
“The configuration updates for the Cobra/Carbon system malware, also known as Pfinet, are interesting, because this is another project related to the Turla threat actor. This suggests that we are dealing with a multi-stage infection that begins with the Epic Turla – to gain a foothold and validate the high profile victim. If the victim is interesting, it gets upgraded to the full Turla Carbon system,”said Costin Raiu, Director of the Global Research and Analysis Team at Kaspersky Lab.
The Carbon backdoors, meanwhile, share characteristics with other attack platforms such as Tilded and Flame, as well as some subtle connections to Miniduke. The attackers do not seem to be native English speakers, Kaspersky’s report said. One of the Epic backdoors is called “Zagruzchik.dll” which translates to bootloader in Russian, and the Epic Turla control panel is set to Cyrillic.
Most of the victims are in France, the United States, Iran and Russia with targets ranging from ministries of the interior, trade and commerce, foreign affairs and intelligence in the European Union and Asia.