Cloud-based note taking service Evernote this week pushed out three new security features including two-factor authentication for some users’ accounts in hopes of adding an extra layer of protection.
The service is among the latest to hop on the two-step verification bandwagon, following Amazon this week, Twitter this month and Microsoft in April.
For the time being the company is introducing the functionality only for Evernote Premium and Evernote Business users until it feels like it has optimized its processes and is confident it can support its entire base of users, according to a note on its blog Thursday.
As usual with the feature, users can choose to get an additional verification code – generated by Google Authenticator if they want – sent to their phone when logging into the site or whenever the application is installed on a new device. Users will then have to enter in their usual password in addition to the one-time password to get access to their account.
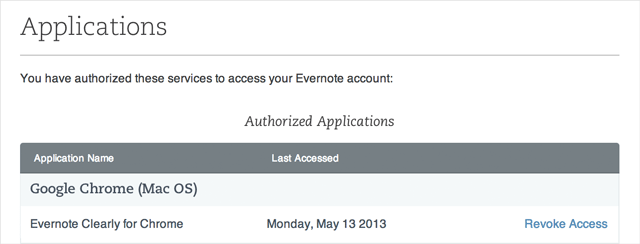
Evernote has also introduced a new feature where users can revoke existing versions of the application from any device it may be associated with. If a user loses their cellphone, they can log-in to the site to make sure the app requests a password the next time it’s opened on the device.
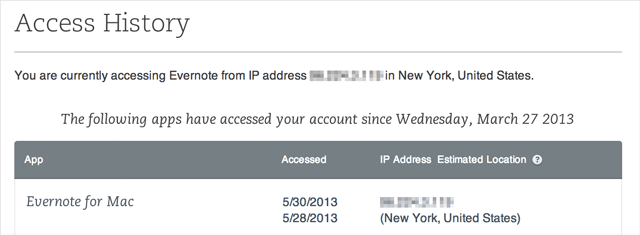
This feature, along with another called “Access History,” which allows users to show a running list of every time the account has been accessed over the past thirty days – along with locations and IP addresses – can be used by any user, regardless of whether or not they pay for Evernote.
The news of more security coming to Evernote is assuredly welcome news to some. The service popped up in the news earlier this year when it was reported that attackers had hacked the service and gained access to some of its users’ information, including their email addresses and hashed passwords. Attackers even managed to leverage the service in March and get it to mimic a control and command server. URLs on Evernote led to a malicious .DLL file, which in turn, led to a backdoor for a data-stealing Trojan.