A state-backed Iranian threat actor has been using multiple CVEs – including both serious Fortinet vulnerabilities for months and a Microsoft Exchange ProxyShell weakness for weeks – looking to gain a foothold within networks before moving laterally and launching BitLocker ransomware and other nastiness.
A joint advisory published by CISA on Wednesday was meant to highlight the ongoing, malicious cyber assault, which has been tracked by the FBI, the U.S. Cybersecurity and Infrastructure Security Agency (CISA), the Australian Cyber Security Centre (ACSC) and the United Kingdom’s National Cyber Security Centre (NCSC). All of the security bodies have traced the attacks to an Iranian government-sponsored advanced persistent threat (APT).
The Iranian APT has been exploiting Fortinet vulnerabilities since at least March 2021 and a Microsoft Exchange ProxyShell vulnerability since at least October 2021, according to the alert. The weaknesses are granting the attackers initial access to systems that’s then leading to follow-on operations including ransomware, data exfiltration or encryption, and extortion.
The APT has used the same Microsoft Exchange vulnerability in Australia.
CISA Warning Follows Microsoft Report on Six Iranian Threat Groups
CISA’s warning came on the heels of an analysis of the evolution of Iranian threat actors released by Microsoft’s Threat Intelligence Center (MSTIC) on Tuesday.
MSTIC researchers called out three trends they’ve seen emerge since they started tracking six increasingly sophisticated Iranian APT groups in September 2020:
- They are increasingly utilizing ransomware to either collect funds or disrupt their targets.
- They are more patient and persistent while engaging with their targets.
- While Iranian operators are more patient and persistent with their social engineering campaigns, they continue to employ aggressive brute force attacks on their targets.
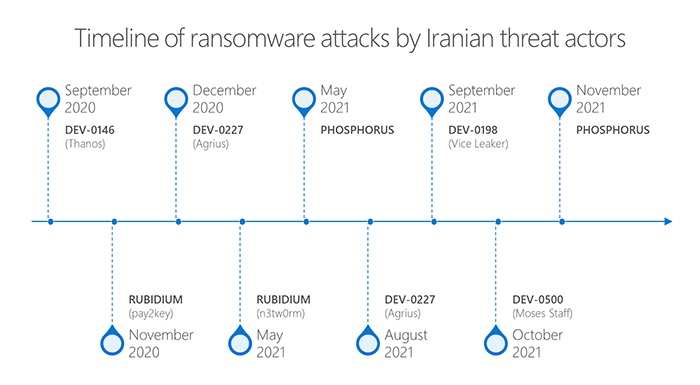
They’ve seen ransomware attacks coming in waves, averaging every six to eight weeks, as shown in the timeline below.
In keeping with what CISA described on Wednesday, MSTIC has seen the Iran-linked Phosphorous group – aka a number of names, including Charming Kitten, TA453, APT35, Ajax Security Team, NewsBeef and Newscaster – globally target the Exchange and Fortinet flaws “with the intent of deploying ransomware on vulnerable networks.”
The researchers pointed to a recent blog post by the DFIR Report describing a similar intrusion, in which the attackers exploited vulnerabilities in on-premise Exchange Servers to compromise their targets’ environments and encrypt systems via BitLocker ransomware: activity that MSTIC also attributed to Phosphorous.
No Specific Sectors Targeted
The threat actors covered in CISA’s alert aren’t targeting specific sectors. Rather, they’re focused on exploiting those irresistible Fortinet and Exchange vulnerabilities.
The alert advised that the APT actors are “actively targeting a broad range of victims across multiple U.S. critical infrastructure sectors, including the Transportation Sector and the Healthcare and Public Health Sector, as well as Australian organizations.”
Malicious Activity
Since March, the Iranian APT actors have been scanning devices on ports 4443, 8443 and 10443 for the much-exploited, serious Fortinet FortiOS vulnerability tracked as CVE-2018-13379 – a path-traversal issue in Fortinet FortiOS, where the SSL VPN web portal allows an unauthenticated attacker to download system files via specially crafted HTTP resource requests.
It’s déjà vu all over again: In April, CISA had warned about those same ports being scanned by cyberattackers looking for the Fortinet flaws. In its April alert (PDF), CISA said that it looked like the APT actors were going after access “to multiple government, commercial, and technology services networks.”
That’s what APT actors do, CISA said: They exploit critical vulnerabilities like the Fortinet CVEs “to conduct distributed denial-of-service (DDoS) attacks, ransomware attacks, structured query language (SQL) injection attacks, spearphishing campaigns, website defacements, and disinformation campaigns.”
CVE-2018-13379 was just one of three security vulnerabilities in the Fortinet SSL VPN that the security bodies had seen being used to gain a foothold within networks before moving laterally and carrying out recon, as the FBI and CISA said in the April alert.
According to Wednesday’s report, the APT actors are also enumerating devices for the remaining pair of FortiOS vulnerabilities in the trio CISA saw being exploited in March, which are:
- CVE-2020-12812, an improper-authentication vulnerability in SSL VPN in FortiOS that could allow a user to log in successfully without being prompted for the second factor of authentication (FortiToken) if they changed the case of their username, and
- CVE-2019-5591: a default-configuration vulnerability in FortiOS that could allow an unauthenticated attacker on the same subnet to intercept sensitive information by impersonating the LDAP server.
“The Iranian Government-sponsored APT actors likely exploited these vulnerabilities to gain access to vulnerable networks,” according to Wednesday’s alert.
In May, the same Iranian actors also exploited a Fortinet FortiGate firewall to gain access to a U.S. municipal government’s domain. “The actors likely created an account with the username “elie” to further enable malicious activity,” CISA said, pointing to a previous FBI flash alert (PDF) on the incident.
In June, the same APT actors exploited another FortiGate security appliance to access environmental control networks associated with a U.S. children’s hospital after likely leveraging a server assigned to IP addresses 91.214.124[.]143 and 162.55.137[.]20: address that the FBI and CISA have linked with Iranian government cyber activity. They did it to “further enable malicious activity against the hospital’s network,” CISA explained.
“The APT actors accessed known user accounts at the hospital from IP address 154.16.192[.]70, which FBI and CISA judge is associated with government of Iran offensive cyber activity,” CISA said.
Yet More Exchange ProxyShell Attacks
Finally, the gang turned to exploiting a Microsoft Exchange ProxyShell vulnerability – CVE-2021-34473 – last month, in order to, again, gain initial access to systems in advance of follow-on operations. ACSC believes that the group has also used CVE-2021-34473 in Australia.
ProxyShell is a name given to an attack that chains a trio of vulnerabilities together (CVE-2021-34473, CVE-2021-34523, CVE-2021-31207), to enable unauthenticated attackers to perform remote code execution (RCE) and to snag plaintext passwords.
The attack was outlined in a presentation (PDF) given by Devcore principal security researcher Orange Tsai at Black Hat in April. In it, Tsai disclosed an entirely new attack surface in Exchange, and a barrage of attacks soon followed. August was glutted with reports of threat actors exploiting ProxyShell to launch webshell attacks, as well as to deliver LockFile ransomware.
Indications of Compromise
CISA’s detailed alert gives a laundry list of tactics and techniques being used by the Iran-linked APT.
One of many indicators of compromise (IOC) that’s been spotted are new user accounts that may have been created by the APT on domain controllers, servers, workstations and active directories [T1136.001, T1136.002].
“Some of these accounts appear to have been created to look similar to other existing accounts on the network, so specific account names may vary per organization,” CISA advised.
Besides unrecognized user accounts or accounts established to masquerade as existing accounts, these account usernames may be associated with the APT’s activity:
- Support
- Help
- elie
- WADGUtilityAccount
In its Tuesday analysis, MSTIC researchers cautioned that Iranian operators are flexible, patient and adept, “[having] adapted both their strategic goals and tradecraft.” Over time, they said, the operators have evolved into “more competent threat actors capable of conducting a full spectrum of operations, including:
- Information operations
- Disruption and destruction
- Support to physical operations
Specifically, these threat actors are proved capable of all these operations, researchers said:
- Deploy ransomware
- Deploy disk wipers
- Deploy mobile malware
- Conduct phishing attacks
- Conduct password spray attacks
- Conduct mass exploitation attacks
- Conduct supply chain attacks
- Cloak C2 communications behind legitimate cloud services
Want to win back control of the flimsy passwords standing between your network and the next cyberattack? Join Darren James, head of internal IT at Specops, and Roger Grimes, data-driven defense evangelist at KnowBe4, to find out how during a free, LIVE Threatpost event, “Password Reset: Claiming Control of Credentials to Stop Attacks,” TODAY, Wed., Nov. 17 at 2 p.m. ET. Sponsored by Specops.
Register NOW for the LIVE event!