Facebook has patched a vulnerability that could have allowed a malicious user to bypass certain security restrictions, according to Sow Ching Shiong, an independent security researcher who discovered the flaw on the popular social network earlier this week.
Currently if a user wishes to change their password on Facebook through conventional means, they’d still have to enter their current password. However, in detailing the vulnerability on his personal blog, Shiong notes that a user could have also changed or reset a Facebook user’s password without entering the current password through the site’s Report Compromised Account page, “https:www.facebook.com/hacked.”
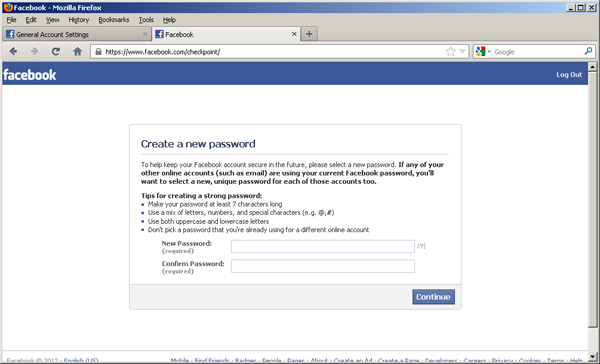
If a user was left logged in on a public computer or if a user’s session ID was stolen via clickjacking, they could be directed to the following URL where the username would appear in the website address: “https://www.facebook.com/checkpoint/checkpointme?f=[userid]&r=web_hacked.”
Chiong notes in his blog if someone wanted to reset this person’s password, Facebook would fail to request that password for the password change through the Report Compromised Account page.
Once in, an attacker could create a new password, confirm it and gain access to their victims’ account.
According to Shiong, the vulnerability was confirmed and patched shortly after it was brought to the attention of Facebook’s Security Team yesterday. Today, a visit to Facebook’s list of White Hat researchers who have responsibly disclosed bugs to the company now reveals Shiong’s name.









