The security team at the world’s most populace social network over in Palo Alto, Calif., finally addressed the thorny issue of the DNSChanger malware to its users in a blog post on the Facebook Security page yesterday.
To the uninitiated, DNSChanger started popping up in security headlines earlier this year when it was targeted as part of an international botnet-takedown campaign dubbed “Operation Ghost Click.” It has since proven itself to be a tenacious adversary with some in the industry believing that it may be impossible to completely scrub the Internet of DNSChanger.
Facebook joined the DNSChanger working group (DCWG) earlier this year. The DCWG is a joint effort to remediate malicious DNS servers consisting of subject matter experts from various institutions and organizations including Georgia Tech, Internet Systems Consortium, Mandiant, National Cyber-Forensics and Training Alliance, Neustar, Spamhaus, Team Cymru, Trend Micro, and the University of Alabama at Birmingham.
As part of the working group, Facebook is capable of notifying users that are likely infected by the malware and giving them directions on how to go about remove it.
So, in the blog post, Facebook’s security team warns that users infected by DNSChanger will be shown the following warning message (which looks ominously similar to any number of Facebook scams):
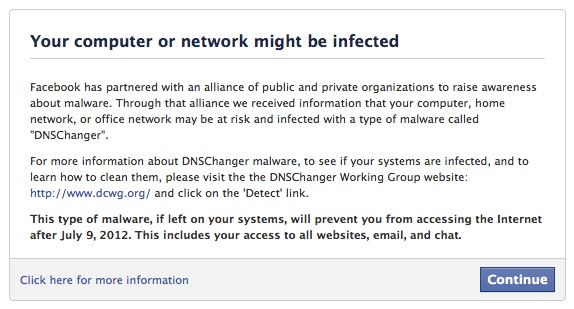
Facebook notes that any individuals (not just those on Facebook) that fail to remove DNSChanger by the July 9th deadline may lose access to the Internet altogether.
You can find instructions on how to remove DNSChaanger on the DCWG website here.









