With the latest iteration of the Blackhole Exploit Kit hitting the web this week, attackers are going to great lengths to spread around links to get unsuspecting victims to click through to the first version of the kit.
E-mail notifications claiming to come from Microsoft Exchange, ADP, the Federal Deposit Insurance Corporation and other purported “trusted sources” have been spotted this week leading web users to pages hosting the original exploit kit.
A post by Ran Mosessco, a Security Analyst at Websense on the firm’s Security Labs blog breaks down some of the deceptive emails.
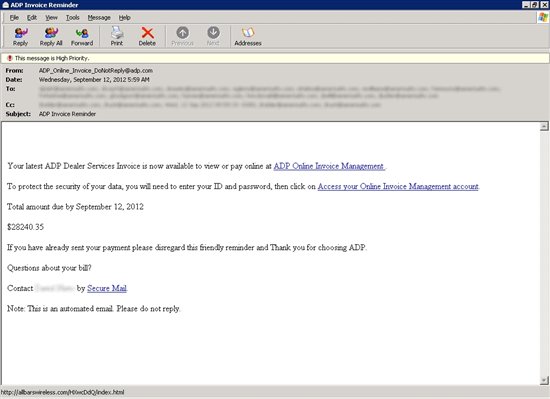
A notification claiming to come from payroll services company ADP tries to trick employees into clicking through to what appears to be their Online Invoice Management account to “protect the security of [their] data.”
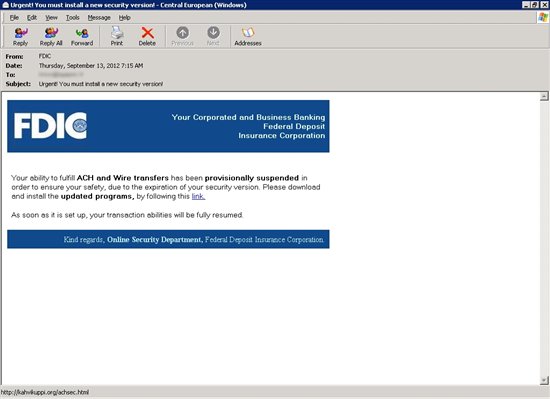
Elsewhere an email disguised as a voicemail notification from Microsoft Exchange Server tries to get users to double click a link to listen to a voicemail and an email that appears to come from the FDIC tries to get users to follow a link to download “a new security version.”
While all these links eventually lead to pages hosting the Blackhole Exploit Kit, Mosessco writes that it likely won’t be long until they begin directing to Blackhole 2.0. The latest version of the kit surfaced online earlier this week and was updated to remove old exploits that have already been fixed. It also came with new features that make it tricky for researchers to reverse-engineer the kit.









