Attackers are sending spoofed “pending notification” emails to Facebook users, claiming that the recipients overlooked some alert on the world’s largest social network, and providing them with a link that supposedly leads to the allegedly neglected content but which, in reality, funnels users to a series of compromised websites hosting the Black Hole Exploit Kit, according to researcher Dancho Danchev.
The malicious email, which can be seen below, is crafted to and does a serviceable job of mimicking Facebook’s widely-recognizable interface. However, it also contains a typo that is indicative of the sorts of writing errors that have become a hallmark of spam campaigns in general.
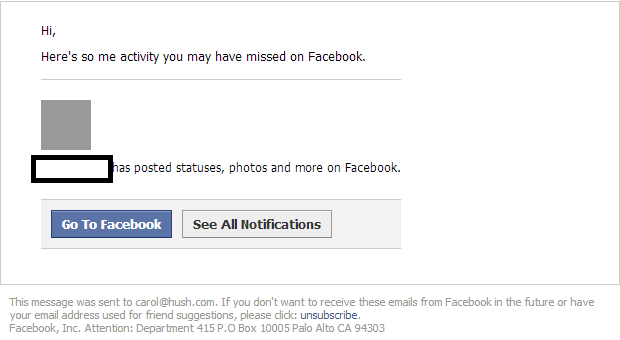
In his write-up on Webroot’s Threat Blog, Danchev identifies CVE-2010-0188, an Adobe bug patched in 2010, as an example of an exploit served in the attack. He also claims that the malicious payload and exploits appear to be hosted on a ‘ceredinople[dot]ru,’ whereas the compromised website that the email links to is ‘covellgroup[dot]com/new.htim?_RAINDOM_CHARACTERS.’
Successful exploitation drops this Win32 executable on its victims. It is detected by most antivirus products but is identified by a number of different names.
Danchev lists a number of IP addresses and related domains implicated in this campaign. You can see them in his report here.
This isn’t the first time Facebook users have been targeted in this kind of attack, in fact, so pervasive is the phishing problem for Facebook that they created a dedicated email address, Phish@FB.com, where users can forward suspect emails for inspection.









