Malware writers are taking advantage of the popularity of the Instagram photo application to distribute a form of malware that can send background SMS texts from Android devices.
Instead of downloading the app from Android’s marketplace, Google Play, some users are being duped into downloading a bogus version of the app from a page that mimics Instagram’s actual homepage. The fake page, mostly in Russian, features a screenshot of an Android phone and beneath it, a download prompt.
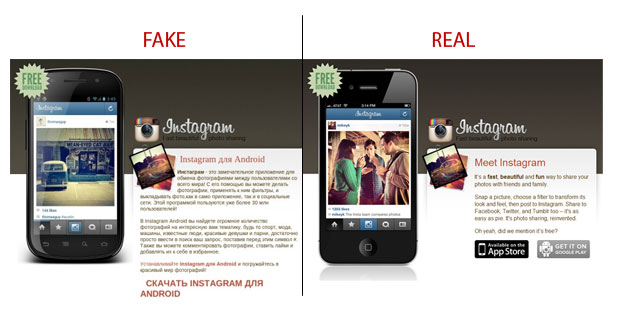
Instead of the application, the victim is actually downloading an .APK that enables attackers to send SMS messages on their behalf, according to reports from security firms Sophos and Trend Micro, who have begun to identify the malware as Andr/Boxer-F and ANDROIDOS_SMSBOXER.A, respectively.
The attackers appear to be capitalizing on the growing buzz behind the photo sharing app that was purchased earlier this month by Facebook for $1B in cash and stock. The app, available on iPhone since 2010, has amassed over five million downloads since coming to Android on April 3.
Android users, especially those who download their apps from unsanctioned marketplaces, have dealt with a rash of new malware in the last month, including variants that can record phone calls, gain root privileges and like the fake Instragram app, send premium SMS messages.









