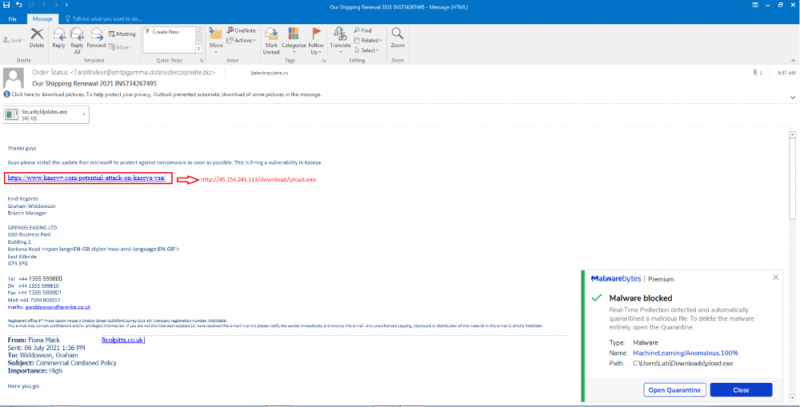
A malware spam campaign is milking the Kaseya ransomware attacks against its Virtual System/Server Administrator (VSA) platform to spread a link pretending to be a Microsoft security update, along with an executable file that’s dropping Cobalt Strike, researchers warn.
On Tuesday night, Malwarebytes Threat Intelligence tweeted a screen capture of the boobytrapped email, which included an attachment named “SecurityUpdates.exe” and a message urging recipients to “install the update fro= microsoft to protect against ransomware as soon as possible. This is fi=ing a vulnerability in Kaseya.”
A #malspam campaign is taking advantage of Kaseya VSA #ransomware attack to drop #CobaltStrike.
It contains an attachment named "SecurityUpdates.exe" as well as a link pretending to be security update from Microsoft to patch Kaseya vulnerability! pic.twitter.com/0nIAOX786i— ThreatDown (@Threat_Down) July 6, 2021
The attackers are looking to gain persistent remote access to the systems of targeted victims who fall for the ploy and run the malicious executable, or download and launch the fake Microsoft security update, on their devices.
UPDATE: Jerome Segura, a lead malware intelligence analyst at Malwarebytes, told Threatpost that so far, this is the first attack that’s been spotted piggybacking on the Kaseya attack.
While Malwarebytes hasn’t determined what threat actors are behind the Kaseya-themed malspam campaign, Segura said that the fake security update – the Cobalt Strike payload – is, interestingly enough, hosted on the same IP address used for another campaign pushing the Dridex banking trojan.
New #Dridex #malspam:
Email -> Contains Excel file -> Drops XSL file -> Creates a scheduled Task -> Calls Mshta.exe to execute XSL file by calling WMIC.exe -> Executes #Dridex payload using Rundll32.exeMaldocs:
ea3cc91ae1d7da1d5509530560f69f30
0e0c3c9cea7e59a5aee7a7ab2dd03eb2 pic.twitter.com/y4JA2c84xe— ThreatDown (@Threat_Down) July 6, 2021
“In the past we’ve seen the same threat actor behind Dridex using Cobalt Strike,” Segura said via email.
Issues Trip Up Kaseya’s Authentic SaaS Patch
Meanwhile, as Kaseya rushes to restore the software-as-a-service (SaaS) version of its ransomware-clobbered VSA, the IT management software company said this morning (Wednesday) that the SaaS deployment as well as the patch for the on-premises version has hit a snag. On-premises customers are the main targets of the ransomware attacks.
This will delay the release of the patch for the self-hosted version of VSA, it said in one of the regular updates it’s been providing since Friday’s discovery of the brazen attacks, pulled off by the REvil ransomware gang. The campaign led to the encryption of files for around 60 of Kaseya’s customers that use the on-premises version of the platform – many of which are managed service providers (MSPs) that use VSA to manage the networks of other businesses.
This morning, Wednesday at 8 a.m. EDT, Kaseya promised to provide a status update at 12:00PM EDT:
As communicated in our last update, unfortunately, during the deployment of the VSA update an issue was discovered that has blocked the release. We have not yet been able to resolve the issue. The R&D and operations teams worked through the night and will continue to work until we have unblocked the release. We will provide a status update at 12:00PM US EDT.
Cobalt Strike
Cobalt Strike is a legitimate, commercially available tool used by network-penetration testers. Its use by cybercrooks has shot through the roof, according to Proofpoint researchers, who recently said that the tool has now “gone fully mainstream in the crimeware world.”
The end goal of its use is to gain initial access and move laterally through a network, to make it easier for cyberattackers to either rip off sensitive data or deliver second-stage malware payloads. It’s extremely popular among ransomware attackers, researchers say.
“Interestingly, 66 percent of all ransomware attacks this quarter involved red-teaming framework Cobalt Strike, suggesting that ransomware actors are increasingly relying on the tool as they abandon commodity trojans,” the Cisco Talos Incident Response (CTIR) team said in a September quarterly report.
Proofpoint researchers meanwhile have tracked a year-over-year increase of 161 percent in the number of real-world attacks where Cobalt Strike has shown up. They’ve witnessed the tool being used to target tens of thousands of organizations, wielded by both general-commodity malware operators and advanced persistent threat (APT) actors.
Cobalt Strike sends out beacons to detect network vulnerabilities. When used as intended, it simulates an attack. But threat actors have figured out how to turn it against networks to exfiltrate data, deliver malware and create fake command-and-control (C2) profiles that look legit and slip past detection.
Cisco Talos and Proofpoint aren’t the only security outfits that have spotted rampant growth in the subversion of Cobalt Strike into an attack tool, an evolution that’s increased following the tool’s source code having leaked from GitHub in November. Two months after that leak, in January, researchers at Recorded Future documented a spike in the use of cracked or trial versions of Cobalt Strike, largely by notable APT groups including APT41, FIN7, Mustang Panda and Ocean Lotus.
070721 14:01 UPDATE: Added input from Malwarebytes’ Jerome Segura.
Check out our free upcoming live and on-demand webinar events – unique, dynamic discussions with cybersecurity experts and the Threatpost community.